Software Asset Management Best Practices
Technological advances have led to an evolution in how organizations deliver services to their users and customers. Whether enterprises transition to cloud-centric environments or remain with legacy on-premises data centers, as the scale of business operations grows, the sprawl of users and associated IT assets leads to a complex environment whose coordination stretches the limits of IT governance. Software asset management (SAM) has thus become a critical capability for all organizations seeking to get and maintain a proper grasp on usage, costs, security, and other essential considerations for business applications.
The ISO 19770-1:2017 standard for IT asset management outlines the industry definition of software asset management as “all of the infrastructure and processes necessary for the effective management, control and protection of the software assets within an organization, throughout all stages of their life cycle.” Examples of software IT assets include the following:
- Operating systems
- Middleware
- Server applications
- User applications
- Mobile applications
- Software licenses
- SSL certificates
- Cloud applications (IaaS, PaaS, and/or SaaS)
No matter the service delivery model, SAM continues to increase in importance, especially because of changes in delivery models, industry dynamics, and business concerns. The rise of hyperscalers and serverless applications means that tracking software and associated licensing must cover a scope that is beyond an organization’s operational footprint. In addition, tracking costs related to users, devices, instances, and hardware is becoming a major headache for financial controllers as well as a focus area for auditors and vendors from a compliance perspective.
Proper management of software assets produces benefits that include enhanced operational effectiveness, cost efficiency, and reduced risk of noncompliance. In this article, we dive into a selection of best practices for software asset management that encompasses oversight, technology, and process perspectives.
Summary of SAM best practices
We have identified five essential software asset management best practices that can help your organization get the most out of your software assets.
| Develop a SAM strategy | Software asset management should be aligned to business and IT strategies. |
| Integrate SAM into the asset management lifecycle | SAM should be considered from acquisition, through usage, and until disposition of all IT assets. |
| Implement end-to-end SAM license management | Tracking of software license usage across all domains and lifecycle stages limits noncompliance and maximizes value retention. |
| Plan and report on SAM costs | SAM costs should be planned in advance, tracked, and reported to key stakeholders. |
| Manage relationships with SAM vendors | Proactive engagement and keeping tabs on changes to vendor contracts and terms ensure that SAM remains valuable. |
Develop a SAM strategy
The management of software assets should be given the same level of attention as other business assets whenever business and IT strategies are crafted. A SAM strategy will be based on information from the following areas of business and IT strategy:
- Business goals and needs
- Technological evolution
- Information security risks and associated controls
- Software vendor direction
- Compliance audit findings
The SAM strategy will assess internal and external issues facing the organization and then provide direction on the acquisition, deployment, and disposition of software assets, including licenses, across the technology environment. This is an important governance element for ensuring that the organization puts in place policies for managing software throughout the IT asset lifecycle, monitors usage regularly, and evaluates the impact of SAM on the achievement of business objectives and the mitigation of business risks.
Accountability is an important element in actualizing the SAM strategy. Ownership of software assets and licenses must be clearly outlined and assigned. Decisions across the IT asset lifecycle must be made with all impacted business leads and communicated to all stakeholders. Even if the enterprise chooses to outsource responsibility for software assets, accountability for them must remain within the organization.
Integrate SAM into the asset management lifecycle
The IT asset management lifecycle encompasses all the stages and related activities that an IT asset undergoes throughout its life within the organization. A lifecycle approach offers the best chance of fully realizing IT asset value, properly accounting for assets, and ensuring their effective and efficient use.
The IT asset management lifecycle stages are as follows:
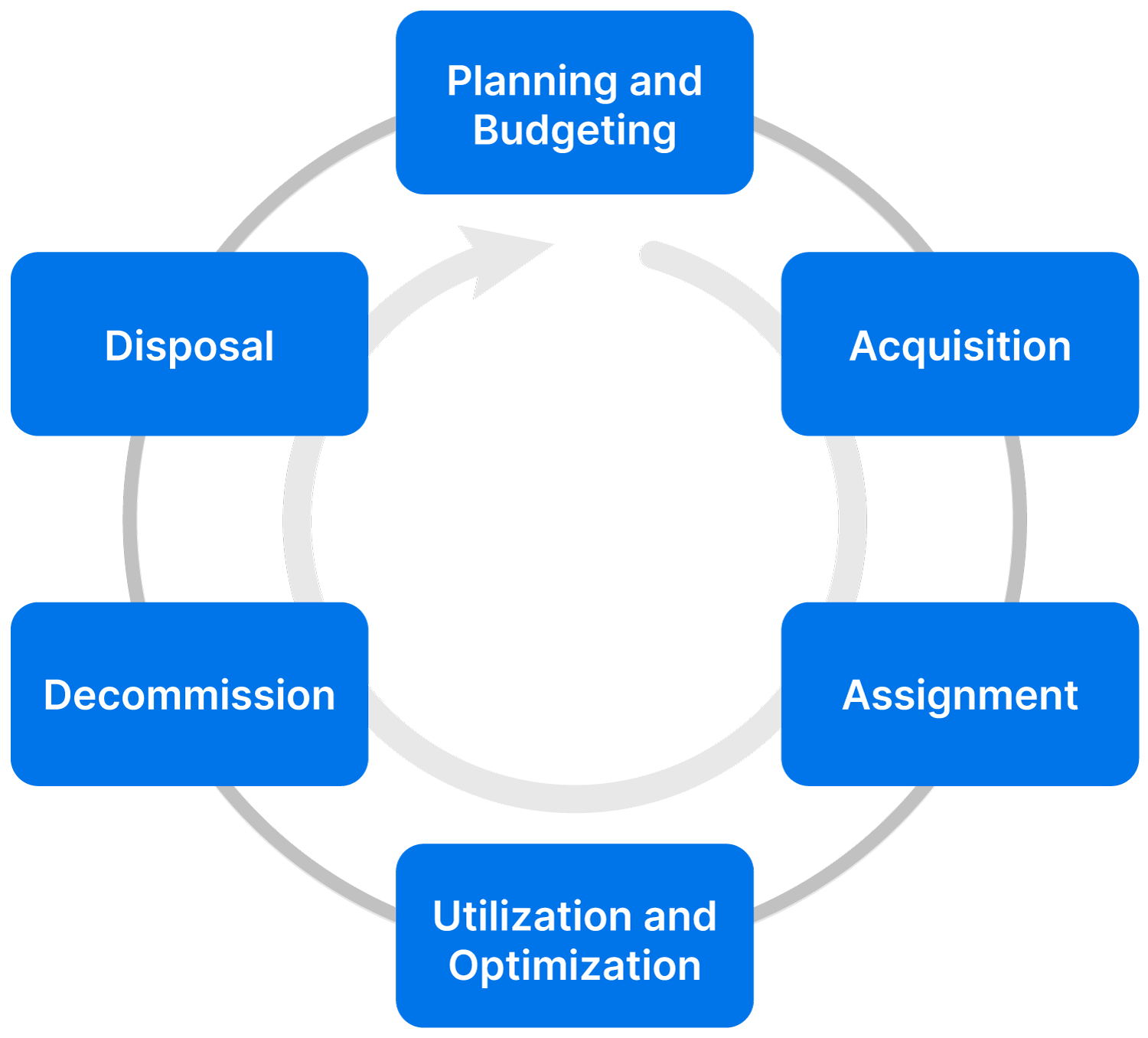
IT asset management lifecycle
Of course, software isn’t really “disposed of” in the same sense as hardware; here, this stage refers to declaring the software end of life and shutting it down or uninstalling it.
To get the most value from the investment in software assets, SAM activities must not be isolated from other IT asset management practices. Information about software assets must be captured in the IT asset register, starting with the acquisition stage and going all the way through to decommissioning. Leveraging an automated solution for the asset register can go a long way toward ensuring that the enterprise optimizes software asset utilization while mitigating the risk of noncompliance arising from shadow IT.
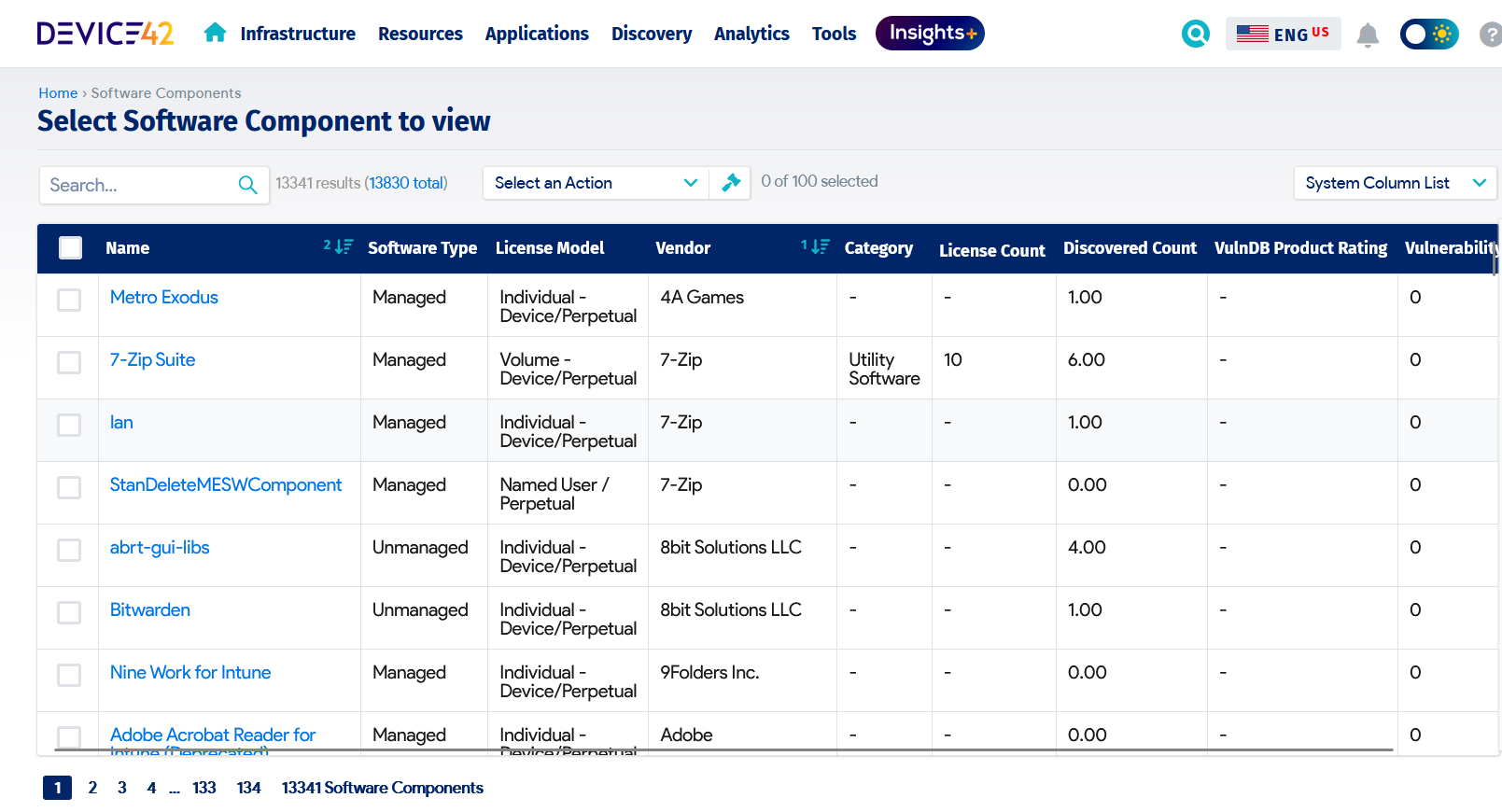
Software entries in the IT asset register
The capabilities of such a solution to support the asset lifecycle include the provision of the following:
- Automated discovery of software assets across on-premises and cloud environments
- The ability to categorize software assets based on business need, technology platform, and risk
- Tracking status throughout the lifecycle
- Tracking dependencies and warranty and compliance information
- Triggering alerts for compliance violations and timelines for renewals or determining end of life
Implement end-to-end SAM license management
Commercial software comes with vendor-set usage limits that depend on a number of factors, including the environment where the software is used, the number of users, usage type, and modification rights. The software license, while identified as a software IT asset, is actually the terms and conditions of use coded within the application. Major software vendors configure their systems to discover and send alerts whenever the license terms are violated; they may then appear on your doorstep for an unannounced audit. When a company is found to have illegally or improperly deployed software against these terms and conditions, it can be hit with hefty penalties that amount to thousands of dollars through settlements or forced purchases, depending on the scale of the misuse.
Software licensing models configured within an IT asset management system
To limit such occurrences, end-to-end SAM license management should be implemented in line with the IT asset management lifecycle. Investing in the right automated solution can provide insights into license type and deployment limits at the user, device, or processor levels. Rather than waiting for vendors to spring surprise compliance audits, it is more prudent to proactively check one’s environment and make the required remedial measures in advance.
From a governance perspective, an organizational policy on acceptable use of software should spell out the rules on adherence to license terms as well as disciplinary measures should users fail to comply. Implementation of controls to limit deployment of software outside license bounds should be automated as a safeguard to detect human error. In addition, regular IT risk assessments must identify risks of noncompliance with software license agreements and initiate appropriate mitigation efforts to limit the impact on the organization. Top management should regularly review reports on license usage and associated risks to the business should violations occur.
Plan and report on SAM costs
Business and IT strategy must be at the forefront of any decision regarding investment in software assets. Budgeting for software should be stringently planned, with commitments to significant purchases preceded by careful comparison of needs against benefits and ensuring buy-in from key stakeholders. All purchases should be formally recorded, and when the software and associated license keys are allocated, they should be maintained in secured repositories. A good IT asset register will facilitate the recording of software asset acquisition costs while tracking costs related to changes in license terms, warranties, and depreciation.
Reports on SAM costs should be published to stakeholders to provide insights on whether the organization is getting value for money on its investment. Such reports would include metrics on the frequency/level of software use, inactive or expired licenses, as well as system loads. For end-user software licenses, reuse must be prioritized over purchase since reuse is directly tied to value retention and prevention of avoidable financial loss from unnecessary acquisitions. This can be facilitated by automating the asset assignment process to ensure that when a device is decommissioned or an employee leaves the role related to the assignment, the software and associate licenses are transferred to a new device or employee instead of triggering additional purchases. The same approach can be applied to provisioned server or cloud environments, where disposition will be controlled so that license redeployment is the first option before contract cancellation.
Manage relationships with SAM vendors
As mentioned earlier, a surprise vendor audit is a possibility if you do not ensure compliance, and it’s no laughing matter. Proactively managing vendor relationships can go a long way toward limiting such embarrassing and costly encounters. The organization should assign accountability for vendor management to keep abreast of the current status of acquired software utilization, the expiry of maintenance contracts, and changes related to licenses and environments. Regular review meetings with vendor representatives can unlock opportunities to maximize software use and reuse or optimize license limits to meet organizational needs.
Some organizations may strategically decide to outsource software asset management to an external party. This can be standalone arrangement or integrated as part of a SIAM contract. No matter the approach, IT management must ensure that the governance of SAM does not take a back seat and that the provider delivers the expected value from maximizing the usage of software assets throughout the lifecycle.
Conclusion
Software asset management continues to rise in prominence, given that most new user applications reside in the cloud. Governance, risk, and control must be placed at the heart of the SAM lifecycle to ensure that the organization retains the full value from the right utilization while mitigating risks related to improper use or license violations. Investing in the right asset management tools to capture value throughout the lifecycle is a crucial differentiator for enterprises to get it right the first time. Value in SAM can only be realized when both ROI and service delivery exceed business expectations.