CMDB for the Cloud Era
Device42’s CMDB provides a single source of truth within your organization. This gives you a clear view into your IT ecosystem to identify, manage, and verify all configuration items (CI) in your environment.

Load CI’s Fast with Powerful Auto-Discovery Tools

Discover
– All discovery tools are agentless
– All discoveries can be scheduled so you’re always up-to-date

Support
– Native support for virtualization platforms
– Native support for public and private
cloud platforms
– Native support for blade chassis

– Granular APIs with sample scripts for
custom discovery
– Fast, flexible and easy to deploy
– Result is a system that is always audit ready
Data Standardization and Enrichment
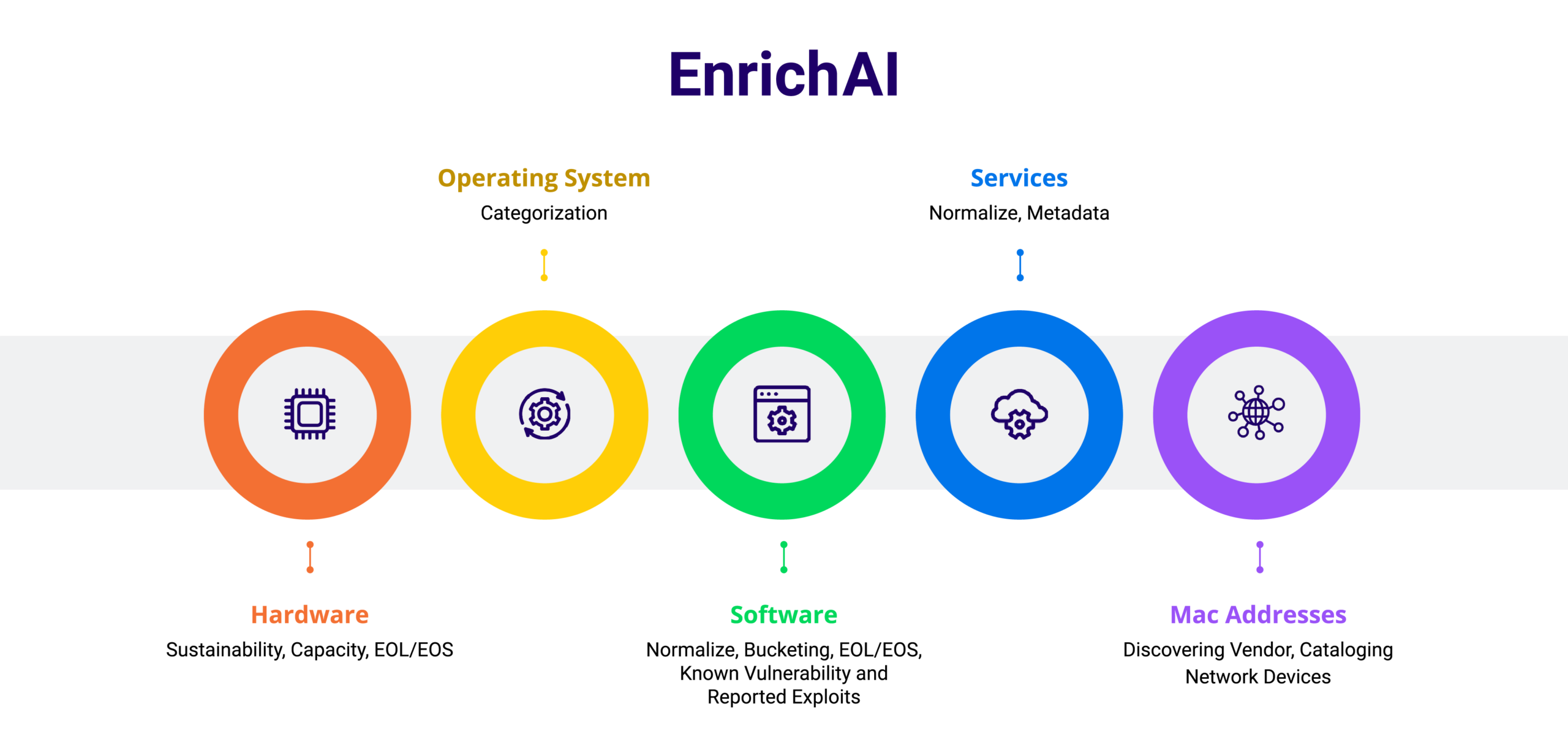
Your IT organization’s heartbeat lies in the CMDB, where the integrity and accuracy of your data is paramount. Yet, sourcing data solely from your infrastructure misses crucial insights provided by vendors and other trusted sources. Device42 EnrichAI uses artificial intelligence (AI) to consolidate, standardize, and enhance discovered configuration item (CI) data. By tackling the challenges of inconsistent and incomplete CI data, EnrichAI offers actionable insights that empower you to improve IT operations management.
Pre-configured CMDB
No need for a long, drawn-out CI design process because all your CI’s and relationships are pre-configured. But Device42 does not simply lock you into an inflexible structure. You can create your own CIs and relationships to complement the built-in structure provided. Additionally, you can define user, groups, passwords, and object-level permissioning.
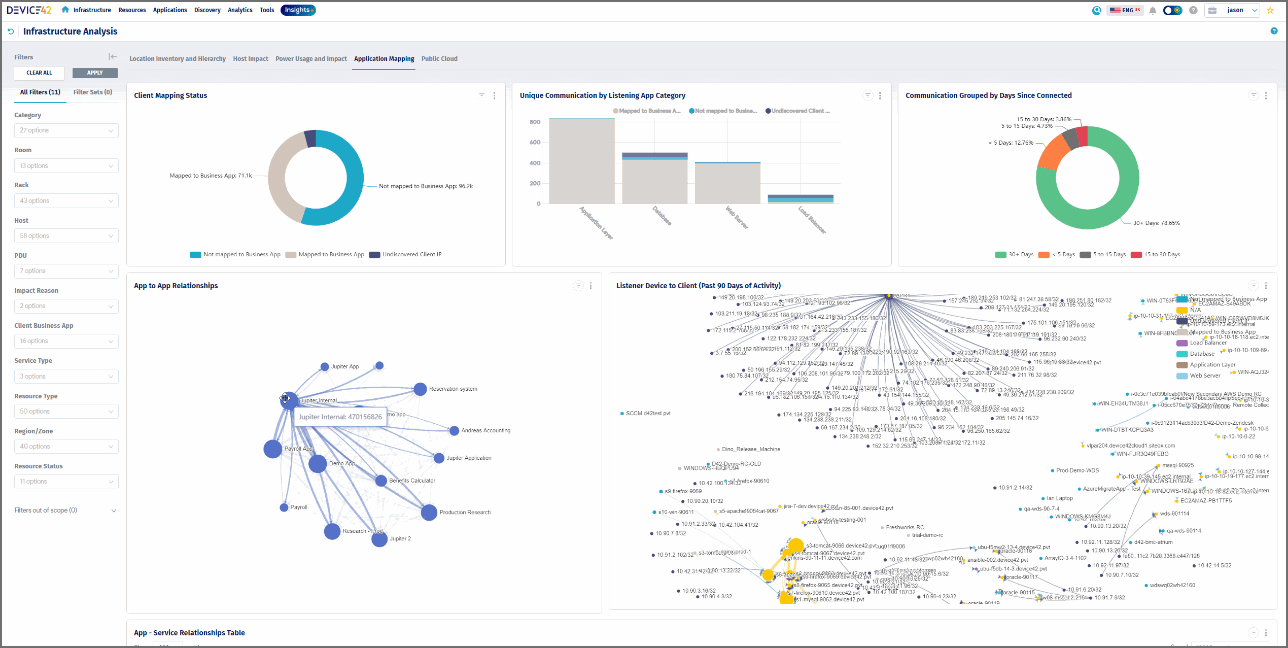
Visualizations
Once your data is loaded, it’s time to reap the benefits. Device42 offers an extensive and highly-customizable set of reports and inquiry screens to access your CI data. But even better, provides an extensive set of visualizations including:
– Your computer rooms and racks with power and capacity heat maps
– Your full IP connectivity and power chain
– Your hardware, software, and application dependencies
Fast and Easy Integrations
Device42 includes a very granular and secure set of RESTful APIs for integration with other applications used to manage your IT infrastructure.

ITSM Integrations
- Link CIs from Device42 to your ITSM tickets
- View or Edit CI details from ServiceNow requests
- Search JIRA issues by CI name
Configuration Management [CM] Integrations
- Device42 utilizes system information data stored in puppet manifests to populate asset inventory
- Streamline the task of provisioning, configuring, and maintaining servers
- Eliminating the need to run redundant auto-discovery processes across the IT infrastructure


Automation Integrations with Webhooks and Device42’s RESTful API
- Trigger events with Webhooks from Device42 based on just about any happening in your infrastructure
- Manipulate any CI within Device42 via its powerful RESTful API
- Direct, secure SQL access to the underlying database
- Easily build custom integrations
- Automate anything from common tasks to complex workloads
- Centrally manage multiple DNS providers from Device42
SIEM Integrations
- Link CMDB items to issues in JIRA
- View CI details from JIRA issues
- Search JIRA issues by CI names
- Display racks and devices inside JIRA when adding/creating/modifying issues

Rapid Deployment
- Most customers find they are up and running with much of their infrastructure loaded in less than a day
- Auto-discovery requires just filling in a few forms with parameters like IP ranges and authentication parameters
- Spreadsheet-based imports are available for data that cannot be discovered
- RESTful API’s are available for customized data-loading and mapping
Download the next generation CMDB
Ultimate Guide to Configuration Management Database (CMDB)
What is a CMDB?
A configuration management database (CMDB) is a repository used to store the data of an IT environment and its relationships. Think of a CMDB as a filing system for all of our important IT assets or configuration items (CI’s). We determine what CI’s in our IT infrastructure are important for us to retain in our CMDB, such as the software, hardware, network, and storage components. The CMDB is our centralized repository containing our entire IT infrastructure and it enables us to monitor, track and manage all of that infrastructure in one central place.
CMDBs are extremely helpful in making important business decisions. Because they are able to show relationships between assets, you can determine what services are connected to a down router or switch and quickly migrate those services to a different network. You are able to prepare for end of life (EOL) cycles by quickly determining what software is approaching EOL on what devices and update them accordingly. It helps with security and compliance by ensuring you know all the interactions between your servers storing sensitive information and the outside world.
How Does a CMDB Work?
In order for a CMDB to be useful it needs to contain up-to-date information. But how does it receive information? How is the CMDB populated?
Of course you could manually enter in all of the information about the devices in your infrastructure. But this would be incredibly time consuming and not a practical option. And the information would become out of date very quickly. You could also upload the information utilizing an Excel spreadsheet that your company has been using to keep track of CI’s, but that information is only as up to date as the Excel spreadsheet. The best and most efficient way is to use a discovery tool. By using a discovery tool you are able to scan and identify any IP enabled device on your infrastructure’s network. You can set time intervals to check and see if any devices have been added or subtracted from the network, and have reliable up to date information for your CMDB.
Once the CMDB is populated with all of your CI’s (configuration items) you are ready to access it. You can access the CMDB directly without the use of a reporting tool but the information is often overwhelming and not conducive to human readability.
What is CMDB Discovery?
There are many ways to populate a CMDB including manual entry, and uploading the data using a simple Excel file. However, the best way is to use a discovery tool. By utilizing a discovery tool you can discover and connect all of your IT assets into a single repository (the CMDB). In order to discover different infrastructure assets, a discovery tool needs to be able to efficiently use different protocols. For instance SNMP works for switches, routers, and networking hardware, WMI works for Windows machines, SSH works for Linux machines. etc.
Device 42’s discovery – agentlessly pull data from physical servers, hypervisors, cloud, network devices, applications, and more.
Why CMDB Still Matters in the Cloud Age
Virtual machines (VM’s), containers, public cloud instances, private cloud infrastructure, and hybrid cloud environments all get increasingly complex very quickly. Wouldn’t it be nice if there was software that could track complex arrangements of environments? If there was a way that you could see all of the application dependencies between a host and their VMs? Between a Kubernetes cluster and its nodes? Between your VLANs and your public cloud instances or hybrid cloud environments? A powerful CMDB can keep track of all your virtual appliances and more.
Many businesses think that because they operate in the cloud a CMDB must be obsolete. That it only tracks physical IT infrastructure or it’s the same as ITAM. But this couldn’t be further from the truth. Operating your business in the cloud creates an even stronger need for a competent CMDB platform. Being able to quickly identify containers, and instances that are spun up and then deleted from your infrastructure is key with managing efficient IT resources.
Notoriously complex cloud billing can be understood by utilizing a CMDB and seeing where and how your resources are being used. By having this data, along with dependency mapping for applications, you can ensure your VLANs are set up correctly and that only the resources you want attached to certain VLANs, or attached to the public internet are.
How Can a CMDB Help?
CMDB Use Cases:
Impact Analysis
Virtual machines (VM’s), containers, public cloud instances, private cloud infrastructure, and hybrid cloud environments all get increasingly complex very quickly. Wouldn’t it be nice if there was software that could track complex arrangements of environments? If there was a way that you could see all of the application dependencies between a host and their VMs? Between a Kubernetes cluster and its nodes? Between your VLANs and your public cloud instances or hybrid cloud environments? A powerful CMDB can keep track of all your virtual appliances and more.
Many businesses think that because they operate in the cloud a CMDB must be obsolete. That it only tracks physical IT infrastructure or it’s the same as ITAM. But this couldn’t be further from the truth. Operating your business in the cloud creates an even stronger need for a competent CMDB platform. Being able to quickly identify containers, and instances that are spun up and then deleted from your infrastructure is key with managing efficient IT resources.
Notoriously complex cloud billing can be understood by utilizing a CMDB and seeing where and how your resources are being used. By having this data, along with dependency mapping for applications, you can ensure your VLANs are set up correctly and that only the resources you want attached to certain VLANs, or attached to the public internet are.
Root Cause Identification
When a problem does occur, an organization can lose millions of dollars in just minutes. The faster you can find the root cause of a problem, the better your business will be. Because CMDBs have, or at least should, have the latest IT data in one central repository and the relationship of the resources, IT teams can become very productive in solving root cause problems much faster and dramatically reducing their MTTR (Mean-time-to-resolution).
As an example – If you have your network properly identified you can find which services are impacted by an outage and get them routed to a different router or switch saving you time and money. According to a report by Gartner – network outages average a cost of $5,600 a minute. Showing that even by reducing our outage downtime by minutes can save a bundle. A more recent data center survey in 2021 by Uptime Institute found that 62% of the outages classified as significant, serious, or severe cost over $100,000, with 15% of them costing $1 million. Outages will happen and being able to quickly discover which services are impacted and quickly implement an action plan is critical for business profitability.
Service Mapping
Service mapping allows organizations to view the entirety of their IT resources in the path of a particular service being delivered for a business unit or business function. For example an application like SAP Exchange may require servers, databases, storage, and networking to function and deliver that business service. The CMDB can provide the IT teams the ability to tag and view the resources that deliver that business service in one place. This data can be used for chargebacks, performance management, and also for future planning and optimization.
Service Performance Planning
CMDBs help with mapping the services and their performance of those services. You can use the service performance data to plan for future capacity based on recent changes and growth in various demands from the business on the IT infrastructure for example.
Auditing and Compliance
When an Audit takes place, most IT teams have to drop their already overloaded work schedules to deal with the audit. Having a solid and functioning CMDB means getting to complete audits much faster. You do not have to chase down spreadsheets, knowledge in people’s heads and computers to get the details the auditors need. You can get it all from the CMDB.
Malware & Security
When software reaches end of life (EOL) updates and security patches will no longer be issued by the manufacturer; this is when nefarious actors strike. It’s much easier for malicious actors to gain access to systems that are no longer supported because exploits are not going to be patched. Consider the chaos that the WannaCry ransomware caused in 2017. The WannaCry ransomware was one of the most prolific cyber attacks in recent history, and the main reason it was so widespread is because outdated computer systems had no way to prevent the attack. By utilizing a CMDB we can see what software on which devices are reaching EOL and update them accordingly. This allows us to protect our infrastructure from nefarious actors by having the latest security updates within our environments.
CMDB Deployment Best Practices
It is important to gradually deploy a CMDB– Moving too quickly can overwhelm your departments and create errors. Learn about the best practices for deploying a CMDB in a sustainable manner that gives you an accurate infrastructure portrait.
The Relationship Between DevOps and the CMDB
DevOps teams face gigantic challenges in managing complex, hybrid technology for their business. Stakeholders are charged with working together to turn more data into actionable insights, improve service delivery and reduce costs, and on top of these challenges, different teams manage different silos of technology using different models for success.
How can DevOps teams utilize a CMDB to face the increasingly difficult landscape of managing data?
CMDB For Compliance
IT Infrastructure teams are typically required to conduct, assist in, and endure several types of audits every year – finance audits, security audits, risk-related audits, budget cycle audits, ISO 27001 compliance audits, and more.
A software audit can be particularly difficult if:
- You don’t have an accurate inventory of all your software
- The data you do have exists only in somebody’s head, or you have personnel changes, and the information is no longer available
- Software is frequently installed and removed on servers and end-user machines without a record
All compliance requirements rely fundamentally on good, clean, and accurate data. To achieve one or any of these mandates, you need continuous compliance automation to keep the data accurate. A CMDB solution can autodiscover in real-time all hardware, software, and devices across your entire IT hybrid infrastructure, producing an accurate inventory that is always audit-ready.
A big part of ISO 27001 Compliance requires assigning risk owners to each IT asset you own. Using a CMDB as your source of truth, you can easily locate and assign owners to each IT asset.
Another capability of a CMDB is application dependency mapping, which is the ability to track and visualize application interdependencies with hardware, devices, and other systems and display that information visually in impact charts.
This gives you the visibility to understand where vulnerabilities might exist so you can address them before they become a compliance issue.
Learn more…
Continuous Compliance – the Newest Member of DevOps Pipeline
How Software Asset Management Can Reduce SOX Compliance Risk
CMDB Reporting, Dashboards, and Data Visualization
Making sense of your data is paramount to managing your environment. The typical CMDB provides tabular format reports, dashboards, and data visualizations that can quickly deliver insights into configuration Items(CIs), metrics, and analytics. This is actionable data that can help you identify the impact of changes, patterns that lead to incidents or problems, and operating costs in time, money, and personnel.
Tabular reports typically are used to look at the details of data sets for a more full analysis. Dashboards are used to look at a point-in-time to answer a specific question, such as “How many new devices have been added to the network in the last week.” Data Visualizations makes it easier to identify outliers, trends, and patterns in data sets.
Whether your data is formatted in a tabular report, dashboard, or data visualization, the result should provide actionable insights to better manage your IT environments.
Importance of CMDB Update & Data Refresh Strategy
Once you have implemented a configuration management database (CMDB), that is just the beginning of having transparency, visibility, and management of your environment. Environments change constantly, and in order to have data integrity, there should be a CMDB update process and be refreshed at regular intervals to ensure that it provides accurate information.
Up-to-date information helps you to quickly identify the affected device when troubleshooting an issue. It also helps improve IT asset management by providing you with an understanding of the relationships and interdependencies among software, hardware, and devices before decommissioning hardware, undertaking cloud migrations, and planning for capacity..
Keeping the information refreshed in a CMDB also helps in maintaining good security and compliance standards. If a patch has not been applied to an application, this can become a cybersecurity risk for an organization.
1. Develop a Data Refresh Strategy
Before you implement a CMDB, you should work with the functional areas that will be dependent on the data to understand business objectives.
A full data sync on an hourly basis might not be practical due to the amount of time it takes to update all the data. Instead, a strategy should be built around the business objectives and the specific configuration items (CIs) to support those objectives.
Once this has been defined, the frequency of refreshing the specific data associated with those CIs can be established on a higher frequency. A full data refresh sync can occur either daily, weekly, or at another frequency.
2. Data Sources
As part of the strategy, you should identify the sources from where the data will be pulled. The CMDB is intended to be your single source of truth, so it is important that the data is pulled:
- Directly from the source through auto-discovery.
- From integrations with orchestration and automation tools like MS SCCM, Intune, and Puppet.
- Working with APIs from hypervisor, hyperscale, and other control planes.
- By finding the correlation between all these sources, and de-duplicating the data.
- Or using best of breed products designed for this, such as Device42, that pulls the latest data, deduplicates, normalizes and categorizes the data for you automatically.
3. Auto-Discovery Key to Data Integrity
Your primary tool for refreshing data should come from your auto-discovery tool, which is part of the CMDB. Not all auto-discovery tools are created equal. This is why it is important when evaluating a CMDB to understand the breadth and depth of discovery capability.
It is also important that the auto-discovery tool have Integrations with external sources to pull and correlate the data to ensure data accuracy.
4. Cloud Environments
There are two ways to look at CMDB for the cloud era:
- Configuration Data. How a service should be, whether it is in scaled state or normal state.
- Ephemeral workloads that can be short lived.
CMDB must have the ability to digest and document the configuration data, underlying infrastructure, and connectivity status for such services. When it comes to ephemeral data, it can be subjective based on your needs.
You can only gain the value of a CMDB if your data is up-to-date and accurate. A data strategy should be defined and regularly evaluated to ensure that functional areas that depend on the data in the CMDB are getting the value to support their business objectives.
Benefits of a CMDB
What are the main benefits of using a CMDB? Why is a CMDB important for businesses? What can my business gain from utilizing a CMDB? Understanding. The purpose of a CMDB in the ITIL framework is to store configuration records throughout their lifecycle and maintain the relationships between them. Or to put it another way, to understand all of your CI’s and the dependencies between them. CI’s can be anything from software, hardware, network, virtual appliances, containers, power supplies, storage components, and more.
Three main benefits of a strong CMDB are to improve your mean time to repair (MTTR), for general planning and capacity of ITAM, and compliance.
Mean Time to Repair (MTTR)
Having your IT infrastructure and its interworking relationships cataloged in a central repository allows you to quickly identify any issues. Let’s face it, routers become unresponsive, servers go down or get misconfigured, switches get dropped, scheduled maintenance doesn’t always go as planned, and a million other issues arise in a data center. By using a CMDB you are able to see where your interdependencies lie. If a database server goes down that feeds into an application server, you are able to see the interdependency and get the application server hooked up to a backup database server, thus reducing your MTTR. If a switch gets misconfigured you are able to see all the devices that are connected to said switch and move them, getting your devices publicly accessible again.
To put it simply, having a robust CMDB helps with application dependency mapping (ADM), and that helps ensure that your infrastructure is up and running with as little down time as possible.
General Planning
By understanding your infrastructure you are able to plan for how it will be moving forward. A strong CMDB will assist with managing service health, help with service consumption and service cost, and give you a picture of your entire infrastructure. By having this understanding of your services and their costs, you will be able to plan your business priorities accordingly, increasing or decreasing certain aspects of your infrastructure to better suit your customers and objectives.
Compliance
CMDBs are critical come audit time. By having the central repository maintain all of your IT infrastructure relationships including dependency mapping, location of services, EOL on software, instances, and containers, you can assure that your infrastructure is compliant with any HIPPA, PCI-DSS, or ISO requirements. Having a central repository on where/how your data is stored makes everything easy come audit time.
Challenges of a CMDB
Configuration management databases (CMDB’s) can be unwieldy but have also become increasingly important in today’s heavily technology dependent world. With cloud computing expected to grow from 445.3 billion in 2021 to 947.3 billion USD in 2026, it’s no surprise that discovering, cataloging, and understanding interdependencies and infrastructure have become increasingly complex and burdensome. Let’s examine some of the most common pitfalls of CMDBs and how we can overcome them.
Bad Data
The most important portion to any CMDB is of course the data. But what if the data is inaccurate? What if you can’t trust your source of truth? Well, in one word your CMDB becomes useless.
Bad data can occur when the scope of the CMDB is not clear. Configuration items (CI’s) can be left out, unauthorized changes can occur, decommissioned servers and applications may not be registered and more. Once the trust of accurate data is broken, many employees will create different shadow systems to attempt to manage the infrastructure. These shadow systems will suffer the same issues as the core CMDB and often just exacerbate the issue because the key issues have never been addressed.
More than just having a clear scope, CI owners, and a configuration manager, your CMDB needs to be able to handle more than just bare metal.
Keeping Up With the Cloud
A CMDB needs to be more than just an asset registry for bare metal infrastructure. With the prevalence of virtual machines (VM’s), containers, public cloud instances, Kubernetes pods, private cloud hosts, software licenses and more, your CMDB needs to be able to interpret and handle complex data.
Unfortunately, many CMDB’s are either ill equipped to handle the modern complexity of many organizations’ infrastructure; or worse, are able to but are being utilized inefficiently and aren’t correctly capturing anything but physical devices.
If your CMDB can handle virtualization, containzeration, and cloud assets are you devoting enough resources to it?
Poor OPEX
CMDBs are great, but they DO NOT run themselves. Companies need to invest not just in the capital to purchase a CMDB but also in the operational staff to maintain and run it. Do you have a configuration manager to set the structure, format, and standard of your CMDB? Do you have stakeholders that are able to ensure the correct CI data gets captured? Did you invest in the scope of the project before trying to make it work?
Too often companies bite off more than they can chew and create too complex of a data model. It’s much easier to create a complex data model than it is to ensure the data is properly maintained. Set the proper expectations and it will be much easier to succeed.
Refresh Cycles
With setting expectations, it’s important to know when the business’s refresh cycles are going to occur. Capturing the correct CI’s are incredibly important, and it’s difficult if stakeholders are not on the same page when it comes to updating data. Without having a clear understanding of when a refresh cycle occurs, the data captured by your CMDB is going to be incorrect.
Incorrect data in a CMDB is the heart of why CMDB’s fail, and lose employee’s confidence. Having bad processes in place is how it can occur.
Bad Process
What processes has your company created for keeping the CMDB up to date? Is the scope of the CMDB created and understood? Are the CI’s understood and clear? Are there stakeholders and business units in charge of updating CI’s? Do you have a configuration manager, or someone assigned the task of setting the structure, format, and standard of the CMDB?
Bad processes or clear gaps in processes will ensure that your CMDB is not being used to its full potential, and at its worst could make the CMDB useless.
Have specific issues with your CMDB? Maybe one of these three common fixes can help.
Want a more in depth look at how to fix your CMDB? Check out this webinar featuring Forrester Research and Device42.
The Best CMDB Options for 2022
When considering a CMDB it’s important that you know what your business needs. Can your CMDB account for cloud resources? Can your CMDB account for different softwares or services? Understand that a CMDB is not a discovery tool that will go out and discover your infrastructure for you and populate itself. You may want to consider a solution that has more.
Device42
Device42’s CMDB tool is built for the hybrid cloud, providing a single source of truth within your organization. This gives you a clear view into your IT ecosystem to identify, manage, and verify all configuration items (CIs) in your environment. The pre-configured CMDB eliminates the drawn-out CI design process and visualizations make it easier to access and analyze the data. With a deep library of integrations this tool fits seamlessly into any IT environment.
More importantly – Device42 has its own discovery and dependency mapping capabilities. Not only is this an all-in-one solution, but it also feeds into other CMDBs with its own unique approach to on-premise discovery, cloud discovery, asset management, and tracking.
BMC Helix
BMC Helix CMDB (formerly BMC Atrium) consolidates landscape and service information from multiple sources into a single representation to help businesses make better decisions. The key selling points for this tool are its scalability and adaptability.
GLPI
GLPI is a suite of information technology service management (ITSM) software that helps you plan and manage IT changes. In addition to CMDB capabilities, the platform provides numerous advanced features for inventory, asset and mobile device management. The main benefit of GLPI is that the opensource software gives you a free CMDB option. It works well if you can accept manual configuration and management of your CMDB despite the complexity and tediousness of these tasks.
Learn more about CMDB options
CMDB vs. IT Asset Management (ITAM)
The difference between CMDB and IT Asset Management (ITAM) comes down to how configuration items (CI’s), and assets are identified. CI’s are components that are managed in order to deliver an IT service, while an IT asset is defined as anything with positive monetary value for a company. Assets and CI’s are different but sometimes, there’s a direct relationship, like with a workstation. It’s an asset with a defined lifecycle and financial value, and it’s used in the delivery of a service, so it’s a CI. Even so, it’s actually an Asset and a CI both rather than the terms being synonymous. Why? A Dell Inspiron will always be a Dell Inspiron from the day you order it until the day it’s disposed. During that time, it could actually be multiple different CIs….a Windows 10 End-user machine, a Linux Developer machine, etc, which are all entirely different configurations. Almost all physical CI’s are assets but not all physical assets are CI’s. For instance an IT asset to a company could be personnel; personnel would not usually be considered a CI, and therefore not tracked within a CMDB. By drawing this conclusion further we can extrapolate that a CMDB is a type of Asset Management but not all Asset Management utilizes a CMDB.
Asset management is a broader term and can often be defined as a catchall for IT inventory management. While a CMDB oversees the management of CI’s and the motivation for a CMDB lies in the services availability, and delivering great services, asset management deals with the overall financial liability of IT assets. Asset management is primarily more focused on a high level overview of the overall health and financial obligations of the IT assets of the business. CMDBs on the other hand are often integrated with change management systems and focus more on the nitty gritty of the ins and outs of the infrastructure to help with planned maintenance, EOL software cycles, disaster recovery, and more.
As an example: Company A has a strong ITAM system – it knows what it has, and it stops there. Let’s say an engineer gets paged at 2:00 AM about a system being down. They will have to spend an enormous amount of time figuring out relations, dependencies, impacted users, and vendors to call even though they have hardware and software asset data.
Company B has a working CMDB system – it knows what it has, where it is and how it is all connected. In the same scenario as above when the engineer gets paged at 2:00 AM, they will save a lot of time (20% to 80%) knowing interdependencies, SLAs, impacted users and vendors.
How CMDBs Improve ITAM
CMDBs can work in conjunction with IT Asset Management and can improve ITAM. Having a central repository means that the management of the IT assets become much easier when you know all that you have is in one place. Of course, your CMDB has to have the freshest data, and be accurate for the full value to be realized for ITAM.
Having your financial liabilities and your dependencies for running your infrastructure in one centralized repository cuts down on unneeded overlap and provides a single source of truth for your asset management needs.
What’s the Difference between A CMDB and A DCIM Solution?
CMDB discovery is the functionality that identifies the hardware and software components in an IT infrastructure, also known as configuration items (CI), and populates the Configuration Management Database (CMDB) with their associated attributes such as their name, IP address, or version number. CMDB discovery uses various automated techniques for discovering components such as virtual machines, storage volumes, or packaged software applications.
A CMDB maps applications and business processes to their underlying hardware and software components to help you gain contextual insights making the execution of your daily tasks more efficient.
Unlike a CMDB, a DCIM solution is focused only on the monitoring and management of physical assets in the data center. DCIM solutions focus primarily on optimizing data center power, cooling, networking resources, and physical space. Both solutions have the capabilities of asset discovery and asset management, but the difference is the scope of usage.
Another difference is the monitoring and management of data center infrastructure. A DCIM solution provides real-time metrics to enable data center managers to understand the health of their environment with alerts that are triggered when the metrics fall below a threshold. A CMDB is a database that has limited monitoring and management capabilities.
A CMDB can be a component of a DCIM solution, but not the other way around.
The Benefits of Integrating a CMDB with a DCIM Solution
There is some overlap between the data that is stored in a CMDB and captured by a Data Center Infrastructure Management (DCIM) solution. DCIM solutions focus primarily on optimizing data center power, cooling, networking resources, and physical space. But the DCIM solution can feed the CMDB with its more accurate and fresh data.
Unlike a DCIM solution, the CMDB contains information about the entire infrastructure including data center hardware, off-premise infrastructures such as public cloud and colocation facilities, devices, and applications. It can depict the configuration item(CI) dependencies on the infrastructure and other systems.
The benefits of integrating the CMDB with a DCIM solution is that you have a single-source of truth for all infrastructure data and total visibility of your infrastructure, improving data integrity and increasing productivity.
By using a CMDB with a DCIM solution, the CMDB:
- Becomes the source of truth
- Improves workflow and productivity by reducing the input of data into multiple systems, and the management of user permissions for multiple databases,
- Ensures security policies are being met for those users who need access to the data, but not the DCIM solution;
- Increases collaboration across functional areas because it provides a holistic view of the hybrid environment; and,
- Helps you improve mean-time-to-repair (MTTR) because you can quickly identify what is impacted by an event and the dependencies.
The Benefit of Using A CMDB with ITSM
Integrating a CMDB with an Information Technology Service Management (ITSM) platform can improve ITSM efficiency by providing a centralized, up-to-date catalog of asset configurations, relationships, and dependencies.
An ITSM solution provides the workflows and processes for service delivery, including service management, change management, incident management, asset management, and knowledge management.
ITSM solutions have a CMDB as a component of the product, but not all CMDBs are created equal. Some CMDBs contain an expansive scope of assets and others are narrowly defined. If the CMDB has a limited discovery scope, this might limit the usefulness of the data for other functional areas.
The data captured in the CMDB can feed ITSM applications such as Jira™, ServiceNow™, and Zendesk™ to:
- Link configuration items (CIs) from the CMDB to ITSM tickets
- View or edit CI details from ITSM requests
- Search ITSM tickets by CI name
Using a CMDB with your ITSM application helps you identify and resolve issues faster, improves decision making, and refines budgetary forecasting for provisioning because you have a holistic view of your environment and the dependencies.
Learn more…