Security and compliance are front and center for many organizations going in to 2018, and beyond. But you know that – we don’t need to convince you!
We live in an always-on world, and we’re all a part of it. The IS027001 security standard is one of many standards that exist to bring order to the layers of technology that otherwise run rampant about our lives. With regards to ISO 27001 compliance, we have good news: Though achieving official compliance requires a certification audit some real work, getting ready for it is a rather straightforward process. Device42 makes it a lot easier, too, tracking risk owners across your entire IT inventory!
What is ISO 27001?
“ISO/IEC 27001:2013 specifies the requirements for establishing, implementing, maintaining and continually improving an information security management system within the context of the organization.” — www.iso.org
Also known as ISO/IEC 27001:2013 and published September 2013, this standard is aimed at Information Security Management Systems (ISMS) organizations that, if audited by a qualified third party to meet the standards, can be accredited as certified compliant.
What exactly does this mean?
The goal of ISO 27001 is to help ensure, and let others know who might want to do business with you that you’ve worked to ensure the security of your technical assets. But it’s much more than simply an asset registry; As a matter of fact, ISO 27001 defines an asset, at least according to the 2005 version of the standard (the last to contain a definition), as “anything that has value to your organization”.
The standard’s goal revolves around establishment, documentation and improvement of policies and controls for those polices around IT asset security. The ISO 27001 implementation process is centered around a document or collection of documents known as the ‘ISMS’ (Information Security Management System), which must be assembled by each organization, and lays out the acceptable usage policies for your company assets including a set of controls that work to enforce those policies and mitigate any associated risks.
A complete and accurate record of all assets that make up your IT infrastructure is required to support these ISO 27001. Obtaining ISO 27001 Compliance requires nominating and tracking official ‘risk owners’ for every IT asset your organization owns, and [in plain English] that information combined with a formal acceptable use policy regarding those assets with (your ISMS), sums up the ISO 27001 standard.
In sum, that means to comply with ISO 27001, you must assign ‘risk owners’ to each and every asset you have, and do so in a way that is efficient and easy to understand. You’ll then need to get audited to prove you’ve done this. A good way to accomplish this is by leveraging a purpose-built software solution like a CMDB (configuration management database). Most modern CMDB’s, like Device42, can not only autodiscover all your assets, but can track these key details, and much more!
Getting ISO 27001 Compliant: The Device42 CMDB Can Help!
Achieving compliance is a two-part process. An ISO 27001 checklist is (almost) as simple as this:
- Write your ISMS and assign ‘risk owners’:
-
- Author official acceptable usage policies for your assets, and make them available to everyone in the company. ISO 27001 refers to this document as your ISMS, and it is central to achieving successful ISO 27001 compliance. Part of a complete set of policies includes controls, mitigations, acceptable risks, and your internal audit policy. A detailed guide to assembling your ISMS can be found here at itgovernance.co.uk.
- Assign each asset a “risk owner”.
- Perform an internal audit per the policy you created in 1(a).
- Hire and ISO 27001 certification auditor. The audit consists of:
- Stage 1 audit: “Document review”. Checking everything you did in 1(a).
- Stage 2 (main) audit: A review to see that your organization is really doing what your ISMS documentation says you would be doing.
Once you assign all of your assets initial risk owners, making compliance a part of your standard asset lifecycle workflow will help ensure you stay compliant going forward. When provisioning an asset, ensure a risk owner is assigned as part of the process. The Device42 CMDB application was designed to track the ownership information required to comply with ISO 27001, and a whole lot more. With Device42, answering questions like “Who owns this application?”, or “Who is in charge of these servers?” is as easy as a quick glance at the ‘End User’ field (or possibly the ‘Customer’ field, depending on your workflow) in the Device42 UI.
As an example, look at the screenshot below. Device42’s CI details for asset ‘d42laptop02’ identify “Matt” as the assigned end user (Matt is also the risk owner in this case, which may not always hold true):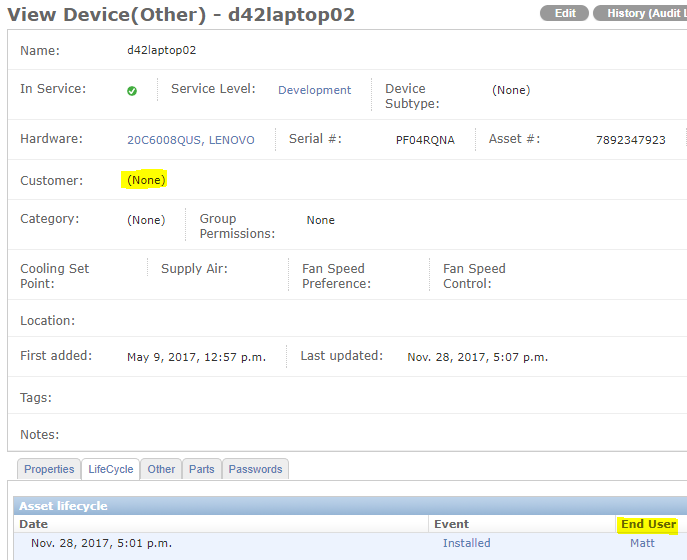
Not only will a CMDB like Device42 help you to easily stay in compliance with IS027001, but as a rather large bonus, Device42 will also help you to make sense of your entire IT infrastructure!
Device42 does this by auto discovering the majority of the information you care about documenting automatically, and also includes features that allow you to track the rest (like power and network cable connections that can’t be discovered). This will benefit you come audit time, and when working towards compliance with other standards like HITRUST, PCI, and the upcoming GDPR as well as ISO 27001.
Device42 can automatically discover and document all of the following (and more!):
- Hardware (computers and servers, networking equipment, power equipment, etc.)
- Software (OS type and all installed software)
- Services (running or not!)
- Power and Cabling Infrastructure
- And the interdependencies between all of these things.
On top of autodiscovery, if you already have assembled asset lists, ownership lists, or any other relevant information in spreadsheets or other similar formats, Device42 includes powerful universal import features that make importing your existing data easy, eliminating duplicate work.
You are also free to expand upon the provided fields, creating an unlimited number of custom fields to track any details that are important to your business and its workflows!
Special Case Risk Owners: Nominating Asset Owners to Unique Asset Types
On the surface, assigning risk ownership sounds rather straightforward: Matt ‘owns’ ‘Matt’s laptop’, while Joe ‘owns’ his company phone. Both assets can have their end user assigned in Device42 as shown above.
Things get more complicated when we begin to talk about companies using cloud-based software products, and technology companies who create and sell software for a living. It’s obvious which end users own the hardware they use, but who ‘owns’ a cloud based application, or the applications technology companies create? For less obvious and special case ‘risk ownership’ situations, where there may be multiple end users who might not also be the risk owners, you could assign risk ownership to your CTO or CIO for compliance.
Once you’ve assigned risk owners to everything you have, and worked through your special cases like your “cloud-based ERP system”, by making risk ownership assignment part of your workflow, you can ensure you stay ISO 27001 compliant going forward!
Do you have any questions or comments regarding the ISO 27001 standard, or about anything else Device42 related? Leave a comment below, or email [email protected]. Our engineers are standing by for your emails!
Device42 is a feature-packed software suite with comprehensive discovery, powerful ADM, a full CMDB, plus DCIM, ITAM, IPAM, webhooks and a complete, well-documented RESTful API, and a wide selection of third party integrations with the software you already use — all at a price point that will surprise you.
If you aren’t already a Device42 user, download your free 30-day trial today, and get on the road to IS027001 compliance!




