Understanding IT Asset Discovery
The information age has led to not only an explosion of data but also a surge in the number of devices that create, store, and consume it. The list is endless: data center equipment, computing and mobile devices, IoT devices, and much more. Research suggests that by 2025 there will be 9.27 connected devices per individual. Considering that the human population recently hit 8 billion, the number of IT assets needed to support the global internet is mind-boggling.
Apart from the operational headache that organizations have to deal with arising from the growth of IT asset numbers and their complexity, they also have to deal with other challenges in the form of evolving data privacy regulations, cybersecurity risks, and the uncontrolled sprawl driven by shadow IT, bring your own device (BYOD), and other trends. Having a grasp of all IT assets within one’s domain and ensuring that they comply with established governance frameworks requires that the organization invest in capabilities that can comprehensively identify IT assets and provide up-to-date status information on their condition and usage.
This first step in IT asset management (ITAM) is termed IT asset discovery and is a foundational discipline underlying ITAM best practices. In this article, we will examine the best way to approach discovery and look at the value it provides as well as potential risks and challenges.
Executive summary
The key aspects of IT asset discovery that must be addressed to ensure excellence in ITAM include the following:
| IT asset discovery scoping | Setting the extent for IT asset discovery and outlining the process and categories. |
| IT asset discovery approaches | Evaluating and selecting the technical approaches to IT asset discovery based on the depth of information required and type of assets. |
| IT asset discovery solutions | Considering the right IT asset discovery solution by examining factors such as capabilities, licenses, and cost. |
| IT asset discovery benefits | Understanding the value of IT asset discovery from both technology and business perspectives. |
| IT asset discovery risks | Identifying and mitigating the risks related to IT asset discovery activities and technologies. |
IT asset discovery scoping
A scoping exercise provides the right foundation for starting IT asset discovery. Too big a scope might overwhelm the discovery process, while too small a scope might not support the organization in getting full value from its asset management framework. The ITIL 4 IT asset management practice guide suggests a progressive approach to scoping based on the what, where, and how of IT assets, as follows:
- What (IT assets to be managed):
-
-
- Hardware: Data center equipment, end-user devices, network and telecom equipment, peripherals, etc.
- Software: Operating systems, middleware, server applications, databases, licenses, device applications, etc.
- Cloud services: Virtual machines, containers, storage buckets, code repositories, etc.
- Data: Business data, customer data, internal user data, system logs, etc.
-
- Where (locations of IT assets):
-
-
- Environments: Development, test, staging, and production
- Facilities: Data centers, server rooms, and colocation sites
- Functions: Business units, departments, functions, and third-party suppliers
- Geography: Continent, country, region, state, and city
-
- How (activity of IT asset scoping):
-
- Organizational asset management policies
- Process activities and techniques for IT asset discovery
- Drivers for IT asset management, including financial, compliance, operational excellence, etc.
The scoping exercise is a consultative activity that requires input from key stakeholders involved in the IT asset lifecycle. An incremental iterative activity ensures that the organization is able to incorporate improvements in every sprint, ensuring that comprehensive information will be captured and any blind spots identified and dealt with immediately.
IT asset discovery approaches
In today’s digital environment, a manual approach to IT asset discovery is difficult and likely to result in missing out on the detailed information that supports other ITAM activities. Investing in an automated capability goes a long way toward making discovery activities efficient and effective.
There are two main approaches to automated discovery:
- Agentless discovery: This is an active technique where IT assets are discovered through network protocols. The discovery solution polls IT assets on the network and interrogates them for information on configuration and status. The protocols for discovery can include SNMP, SSH, WMI, and others, all of which provide different levels of information. This is a low-maintenance approach to discovery, with no need to identify the assets in advance. The network addresses that the IT assets are assigned are usually the only required information to be configured on the discovery solution. However, the IT assets need to be pre-configured for discovery, for example, by being SNMP-enabled. Information security considerations might require that the discovery solution be whitelisted to scan the network, so it is not detected as a potential threat.
- Agent-based discovery: This is a passive technique where the IT assets have a software agent installed that sends out periodic information on the device’s configuration and status to the discovery solution. Agents provide a greater level of detail about IT asset processes and activities. However, the organization needs to identify the IT assets beforehand (manually or through an agentless approach) and then install the agent. The maintenance and cost overhead for IT agents is significantly higher than agentless tools, but the amount of information they provide can make them worth the investment.
During discovery, the information captured depends on the type of asset. For example:
- Hardware asset discovery: Ping response time, port usage, and OID information from MIBs discovered via SNMP, providing information on status, hardware type, vendor, status, CPU/memory/disk usage, etc.
- Software asset discovery: Port usage, network packet data, and vendor code signatures can provide information on IT asset types, versions, hosts, licenses, etc.
- Cloud asset discovery: The discovery tools connect to cloud environments through cloud provider APIs and leverage native cloud services to get information on instances, statuses, license usage, etc.
IT asset discovery solutions
Obtaining the right IT asset discovery solution is a key enabler of ITAM practices. The decisions on selection and deployment of discovery solutions have to be based on the organization’s IT asset discovery scope. It would not make sense to invest in a solution that is unable to comprehensively discover the asset types that the organization has in its domain. For example, an environment that has a heavy investment in legacy equipment like mainframes requires a discovery solution that can discover mainframes, such as those running z/OS operating systems. At the other end of the spectrum, environments deploying more modern technologies like cloud assets, such as virtual devices and containers, would need a solution with the capability to discover them.
As mentioned earlier, modern IT asset discovery solutions support both agent and agentless discovery, and they can span a variety of IT asset types and vendor offerings. They also come with API connectivity to software and cloud service vendors’ environments to ensure that discovery information is constantly updated based on ongoing additions, changes, or removal of the IT assets. An example of a cloud discovery capability is shown below:
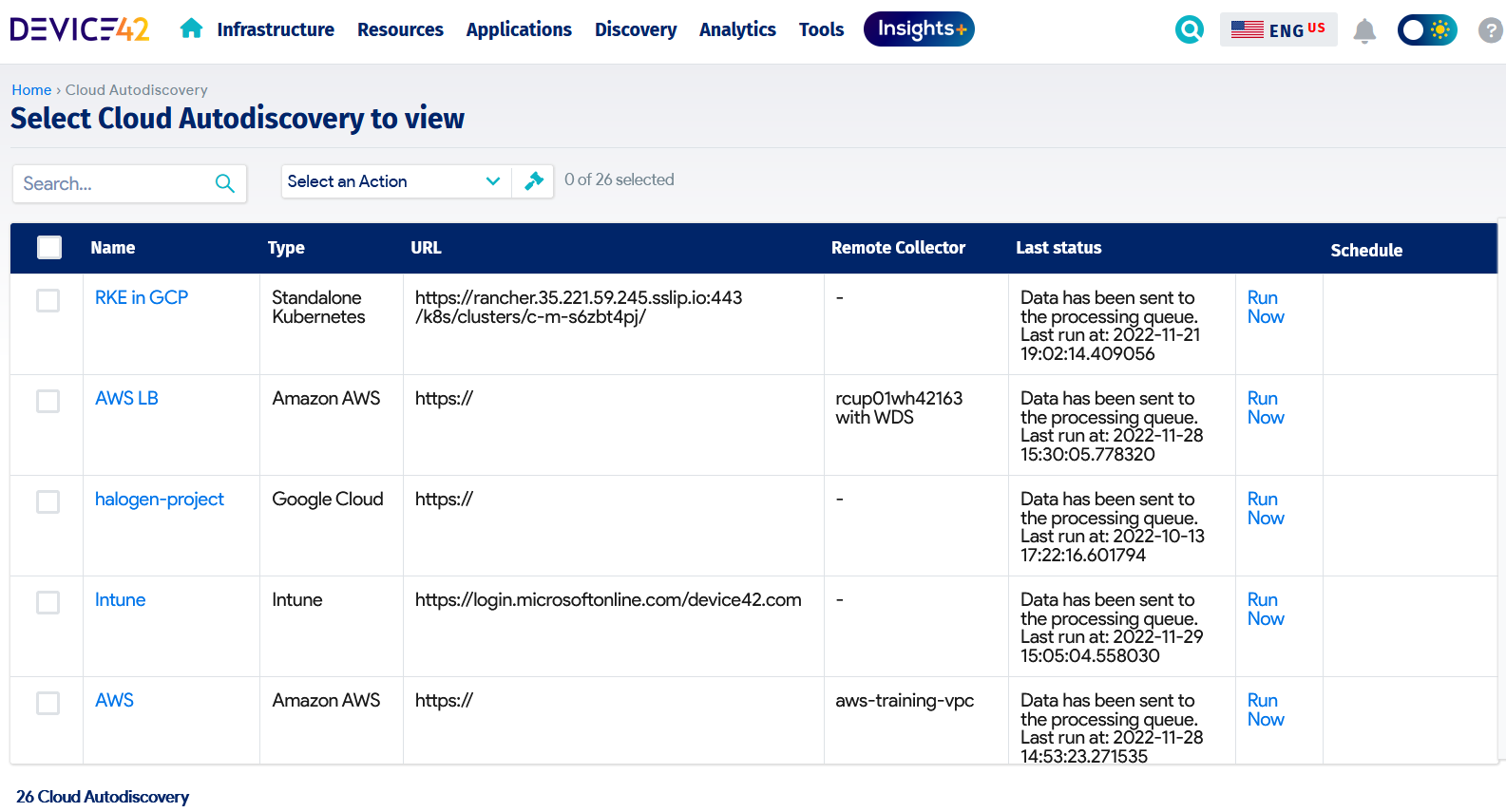
Device42 Cloud Autodiscovery module
The main capabilities to look for in an IT asset discovery solution include the following:
- The ability to support both agent and agentless discovery techniques
- The ability to identify and track physical and logical components, their relationships, and their interdependencies
- The ability to integrate with standard IT systems, including load balancers and hypervisors, to support IT asset discovery
- Out-of-the-box integration with common software and cloud asset management systems as well as customizable APIs
While some organizations may choose to employ a mix of tools to cover the full scope of their capabilities, this can result in higher operational overhead, which might not be cost-effective or efficient in the long run. There is also the need to consider the license costs since some discovery tools are priced based on the number of IT assets to be discovered. Other cost factors include on-premises vs. cloud offerings, subscription vs. perpetual licenses, support requirements, and SLAs.
A variety of technologies and discovery methods should be supported by the ideal IT asset discovery solution. Effective IT asset discovery is only possible when the chosen solution is able to identify each configuration item (CI) in a unique way regardless of the environment in which it is located, correlate all of the data that is available about that CI across various integrations, and present a full set of attributes for every configuration item. By enabling the appropriate level of visibility, this depth of discovery supports the full value of IT asset management and service management processes. The diagram below shows the breadth of technologies that must be considered in a typical enterprise project.
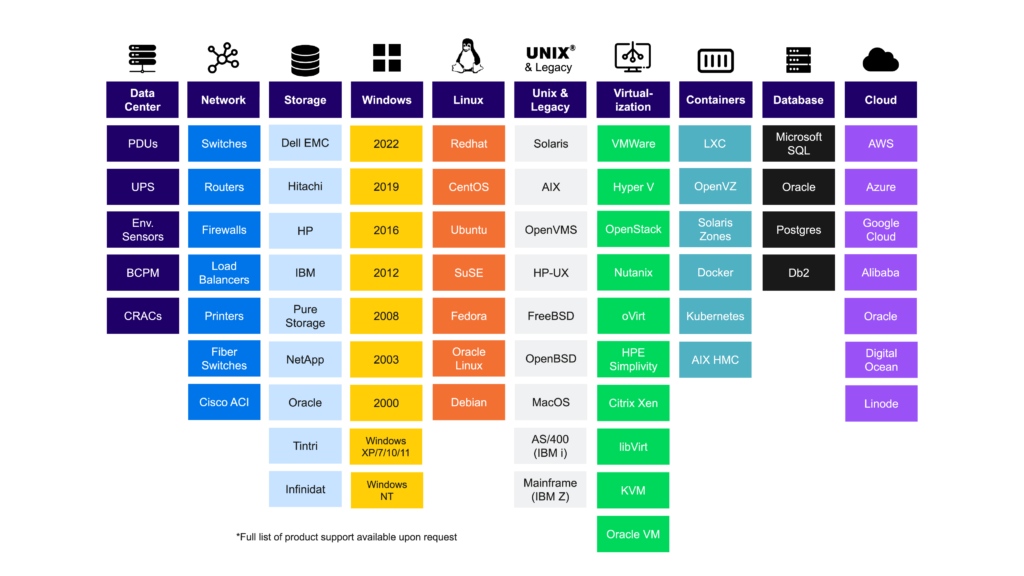
A broad array of supported technologies is key for IT asset discovery.
IT asset discovery benefits
A mature IT function has a complete grasp of the IT assets within its domain. Visibility is the primary outcome of a properly functioning IT asset discovery capability, as this lends support for effective ITAM and IT service management (ITSM) practices such as the following:
- Configuration management: Ensuring that IT assets are configured in the right way—one that complies with service requirements and governance policies
- Change enablement: Ensuring that changes to IT assets are well managed and their impact across the environment and users well understood
- Incident management: Facilitating better understanding of the impact of incidents on IT assets and associated services and users
- Problem management: Supporting better understanding of root causes for problems
- Release management: Enabling the effective rollout of new or changed features to users based on the IT assets they use
- Deployment management: Facilitating better deployment of new or changed services or components across associated IT assets
IT asset discovery can provide benefits to the organization in many areas:
- Modernization: IT asset discovery can provide clarity on existing legacy systems and thus enhance the ability to make easier and better decisions on modernization efforts. Whether the modernization is a strategic initiative or driven by mergers and acquisitions, knowledge of the current state of IT asset deployment will derisk the transformation effort, especially where a shift-and-lift operation is required to ensure a seamless transition to the new state.
- Compliance: IT asset discovery can facilitate visibility into whether the user devices and systems deployed comply with organizational policies, vendor contract terms, and relevant regulations. Examples of areas of compliance include configurations, versions, and license usage. Of course, ensuring compliance is key to reducing the risk of penalties and fines arising from improper use of assets, such as unlicensed software.
- Security: IT asset discovery can enable security teams to identify vulnerable IT assets based on software version and configuration status. The information discovered can also be useful input for investigating the impact of cyber-attacks and data breaches.
- Cost management: Discovery can unearth unutilized or underutilized IT assets that the organization has paid for but is not getting value from. In addition, discovery can provide useful information on comparing asset usage with costs to identify potential savings by migrating to different vendors or providers.
- Risk management: IT asset discovery can facilitate IT risk assessment and business impact analysis activities by providing up-to-date information on the status of IT assets.
IT asset discovery risks
As with any other ITAM activity, IT asset discovery must be carried out in a way that ensures that the organization is not exposed to risks that would affect the process and information quality. Such risks and their mitigation steps include the following:
| Risk | Mitigation |
|---|---|
| Security risks from network scanning or deploying agents | Provide controlled administrative rights and permissions for discovery solutions. Ensure that agents are regularly updated. |
| Poor change enablement practices that introduce IT assets in an uncontrolled manner | Ensure that timely and accurate change information is provided to teams managing IT discovery to keep discovery parameters up to date. |
| Under- or over-scoping discovery licenses, leading to waste or smaller-than-expected numbers of discovered IT assets | Ensure proper planning for the discovery and scoping of IT assets before investing in IT discovery solutions. |
| Incorrect timing of discovery activities, resulting in incorrect IT asset discovery information | Work with IT stakeholders to structure IT discovery periods to follow the completion of executed changes to IT assets. |
| Incorrect network segment information, leading to some IT assets not being discovered | Ensure proper planning and scoping for IT discovery to ensure that comprehensive information on network segments is provided. |
| Negative impact of IT asset discovery on network bandwidth and service availability/performance | Ensure proper timing of IT asset discovery activity and controlled discovery activity that monitors the impact of discovery on live services. |
Recommendations
The critical outcome of a properly working IT discovery practice is the value it provides the organization based on the information on the state of its IT assets. Some recommendations that can lead to this value being achieved include the following:
- Choose an IT asset discovery solution that provides holistic visibility and integration capability.
- Define a process that includes accountability and regularity for IT asset discovery.
- Ensure security controls as part of compliance.
Conclusion
The value of IT asset discovery cannot be underestimated, since it is an integral foundational element for ITAM practices, which in turn support IT service management (ITSM) practices and organizational asset management policies. Combining the right process and tools will result in the highest probability of value for the organization.