A Free Guide to IT Asset Lifecycle Management
Getting a handle on the evolving complexity of today’s technology environment is a serious challenge for most organizations. Whether it is tracking user devices, software licenses, cloud instances, or IoT sensors, IT leadership struggles with difficulties in knowing current status, assigning accountability, and computing return on investment. In addition, trends impacting IT asset management — such as shadow IT, BYOD, technology sprawl, sustainability, and remote working — add extra layers of complexity.
For all these reasons, having visibility and control of IT assets, from when they enter the IT environment until they are no longer required, is a key determiner of operational excellence. Succeeding in this area requires both leadership support and technology enablement.
The ISO 19770-1:2017 standard on IT asset management defines the lifecycle as the stages involved in the management of the IT asset. Having an integrated asset lifecycle is a critical step for any organization seeking the right approach to obtaining full value from their IT asset management practice. According to the ITIL 4 IT asset management practice guide, the lifecycle consists of stages represented by various statuses that the IT asset attains as it transitions from planning all the way through disposal.
An effective IT asset lifecycle management practice can provide numerous benefits:
- Maximizing value from IT asset usage
- Properly controlling associated IT asset costs
- Managing risks related to IT asset underutilization or overutilization
- Providing the right level of information to support decision-making on IT asset acquisition, usage, and disposition
This article will step through the journey of IT assets through the lifecycle, looking at both on-premises and cloud-hosted environments. It recommends best practices that can enable enterprises to obtain the most value from their technology investments.
IT Asset Lifecycle
The IT asset lifecycle can be summarized as follows:
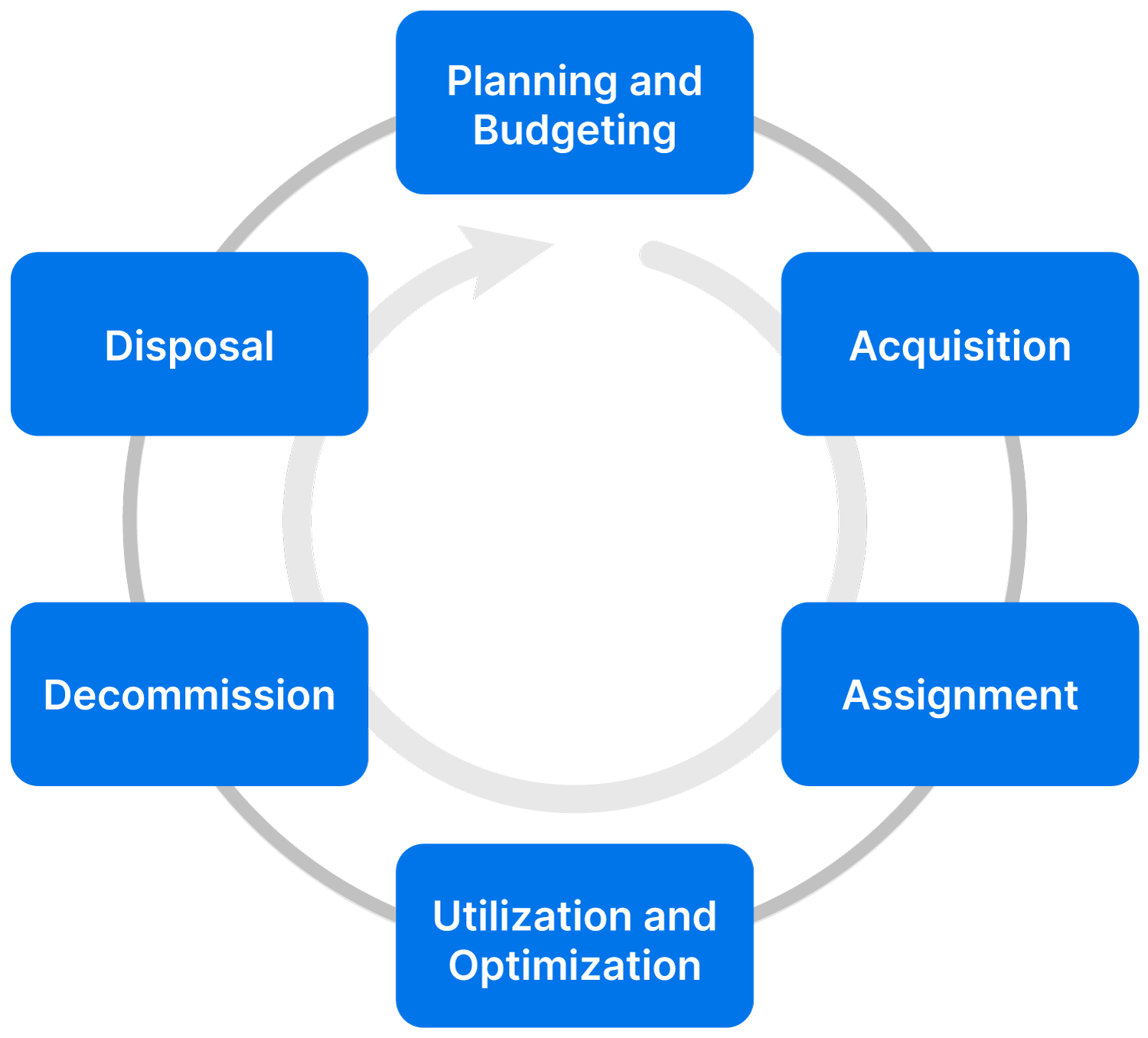
| Lifecycle Stage | Description |
|---|---|
| Planning and Budgeting | Identifying stakeholder needs and aligning with business strategy and investment priorities |
| Acquisition | Procurement (buying, leasing) and onboarding into the IT environment |
| Assignment | Deployment into service for both user fulfillment (devices) and service delivery (infrastructure and applications) |
| Utilization and Optimization | Using the asset, monitoring usage, addressing incidents, maintenance, and dealing with warranty claims |
| Decommissioning | Initiating disposition by removal from service in line with information security requirements |
| Disposal | Removal from the IT environment per business requirements, including sustainability needs |
IT Asset Lifecycle Stages
Planning and Budgeting
As the organization defines its IT strategic goals and objectives, a key activity is evaluating the current state of its internal and external environment and determining a target future state through plans and initiatives. Information to be reviewed during this evaluation will include its IT assets, as the leadership reviews whether its existing IT systems are fit for purpose, cost-effective, and able to meet compliance requirements.
The decisions made during strategy planning will determine the future direction that the organization will take regarding IT asset management from the technology, cost, and compliance perspectives. Many organizations now consider sustainability part and parcel of their business strategy, so IT asset management must consider social and environmental considerations as well as financial ones.
Based on the strategy chosen, the different IT units will have the information needed to draw up their operational plans for the period defined. These plans will include the IT asset requirements of the business and users as well as acquisition and disposition approaches. Plans will be prioritized and presented with related budget estimates to leadership for approval. Budgeting for IT assets will consider sources of funds, proposed acquisition sources, financial policies on depreciation, and ROI, among other cost dimensions.
Acquisition
The acquisition stage is triggered by a request that is approved by management. This stage follows planning, and that sequence is very important to follow for the organization to obtain full value throughout the IT asset lifecycle. Some organizations fail to plan in advance and jump right to acquisition, which is likely to result in some combination of overpaying, wasteful spending, and compliance issues. Following a formal acquisition process that includes justification and vendor evaluation can limit such potential risks from materializing. Leveraging economies of scale and standardizing IT assets are important considerations in proper acquisition that will provide benefits that accrue across the IT asset lifecycle.
Acquisition approaches can vary based on business strategy and environment. They include:
- Procurement through outright purchase: Here, the organization procures the IT asset from a vendor through its capex budget and has full ownership of it. Depending on the purchase agreement, the payment can be a lump sum or done in installments. Outright purchases may come with a limited warranty term, and the organization may need to pay additional costs in the future for support or spares.
- Procurement through leasing: In this approach, the organization will not have full ownership but rather rent the IT asset from the vendor. This may look cheaper in the short term due to reduced upfront costs, and using opex may spare the organization from depreciation, as it can swap the IT asset for newer or better models in the future. That said, the long-term costs can be higher for leasing.
- BYOD as a form of acquisition: Some organizations may ask users to bring their own IT assets for use. This would mostly apply to end-user devices. Here the users would comply with a BYOD policy (crafted as part of planning) and allow the IT team to configure the devices to access approved business software and information.
Once received, acquired IT assets are onboarded in readiness for assignment to the IT environment.
The first part of this process is registration of the asset within inventory, where its components can be confirmed against the requisition requirements. From a financial perspective, IT assets that are not consumables would be recorded in the fixed asset register so that their financial value can be tracked through the balance sheet.
The asset is also tagged with a label and identifier for traceability. Many organizations tag assets using barcodes, QR codes, or RFID tags. The IT asset is then logged into the IT asset register, which then facilitates and tracks deployment and use. A digital asset register is more useful than manual recordkeeping in this regard since it can discover IT assets, capture a lot more information (such as name, type, location, vendor, etc.), facilitate easy searching, and track status automatically.
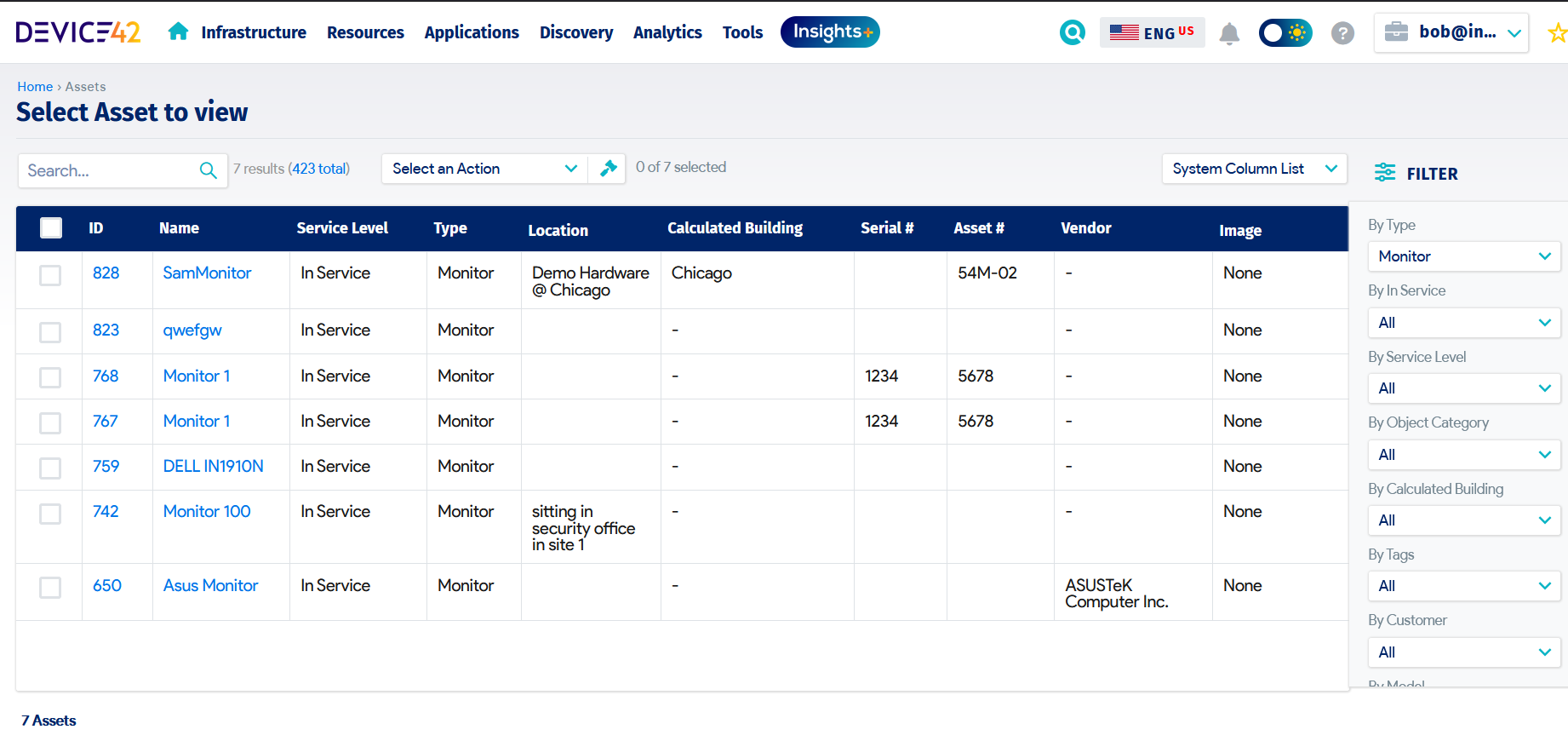
An IT asset register
Assignment
At this stage, the registered IT asset is ready for deployment into service. Some IT assets will come preconfigured from the vendor, while others will require IT staff to prepare them for use by placing a base-level image in accordance with corporate IT policies. This preparation includes configuring approved operating systems, installing role-based business applications, and setting security controls.
IT assets may be kept in a storeroom or datacenter awaiting dispatch or be directly delivered to the user from the vendor. The IT asset register should be updated with the change of state following assignment.
For end-user devices, assignment would be done through the fulfillment of requests raised via the IT service management system in use, which will tie the device to a user. Some IT organizations require users to agree to acceptable usage policies before they are given access to the device. For data center IT assets, configuration and deployment would be a planned exercise in line with the organization’s change enablement policies. Cloud assets can be configured and deployed automatically using continuous integration and delivery (CI/CD), but consideration must be made for financial costs.
Utilization and Optimization
Once deployed for service, the IT assets are monitored to ensure effective and efficient usage in line with business needs and compliance requirements. Monitoring is carried out through usage reports as well as regular financial and compliance audits.
Monitoring of utilization is critical to ensure that the assets and licenses acquired are in full use; otherwise, the organization will incur reduced ROI. Other aspects to be monitored include warranty expiration, support contracts or SSL certificates, upgrade requirements, vulnerabilities, compliance requirements, etc. Regular risk assessment and business impact assessment activities can provide deep insights into the value of IT assets, triggering appropriate action to optimize their usage.
The IT assets should be regularly optimized to ensure that they remain fit for purpose as they are being used. Through the change enablement practice, they should be serviced, upgraded, and maintained based on agreed schedules or whenever the need arises.
The IT asset management team should maintain close relationships with vendors to ensure that they don’t miss out on servicing opportunities provided via warranty as specified in asset contracts. Whenever incidents or problems affecting IT assets arise, they should be addressed quickly and effectively, with each occurrence recorded against the IT asset and reported as part of monitoring service levels to confirm fitness for use.
End-user devices will be closely linked to the employee lifecycle: If an employee changes roles or leaves the organization, the asset should be reconfigured and transferred to a new user or sent back to storage. Monitoring cloud assets will facilitate the shutdown of any instances or retracting of licenses that are not in use, thereby optimizing costs.
Decommissioning
Once an IT asset is no longer useful to the organization, it should be removed from service. Triggers for decommissioning will include end of life, depreciation, warranty expiry, damage, loss, lack of spares, or other reasons.
Decommissioning sounds like a simple process, but a lack of accountability, visibility, or direction can hamper the effort. Disposition planning can help the IT organization prepare for the decommissioning by ensuring that there is clear ownership and guidance on what, when, and how it should take place and who should be responsible.
For IT assets that are supporting business applications and data, removal from service is a controlled process through the change enablement practice. Risks should be assessed to determine whether decommissioning will impact live services prior to removing the assets from production. IT assets will be retrieved from users or the IT environment, and their status updated within the IT asset register. During this period, media will be sanitized through data transfer to storage or replacement devices, or outright deletion in a controlled manner, to prevent security incidents through loss or improper access. Once sanitized, IT assets should be securely stored while awaiting disposal.
Software licenses should be tracked and recovered back into the license pool for reuse at a later date or returned to the vendor to optimize costs. For cloud assets, decommissioning will involve turning off or deleting instances once they are determined to no longer impact live services. For devices that are lost or stolen, remote wiping capability would be triggered to decommission the assets and prevent data loss.
Disposal
IT assets that are decommissioned and can no longer be redeployed are ready for disposal. Decisions on disposal are tied to procurement approaches, sustainability and compliance requirements, and organizational policies related to asset write-off and disposition. IT asset disposal options include the following:
- Sale: If the IT asset’s financial value is significant, it can be offered for sale to the highest bidder. The asset must first undergo formal valuation, with the details of the sale recorded in the fixed asset register.
- Donation: Some organizations may choose to donate IT assets to educational or charitable institutions to extend their use.
- Return: Leased IT assets are returned to their vendors. Return may also apply to BYOD devices that go back to their respective owners.
- Recycling: From a sustainability perspective, IT assets can be recycled and parts potentially salvaged for reuse in other systems.
- Destruction: If no other option can be found, the IT assets are destroyed. In line with e-waste regulations and sustainability policies, the destruction should be controlled to limit negative impact on society and the environment. Only approved, reputable companies should carry out the safe destruction of IT assets, and they should provide disposal certificates as proof.
Regardless of the disposal method, the status of the IT asset should continue to be tracked and updated on the IT asset register. Reports also need to be presented to the organization’s leadership with regard to financial impact and sustainability.
Recommendations
To make the most of the IT asset management lifecycle, the following actions are recommended:
- Implement a governance framework for the IT asset lifecycle stages.
- Use an automated IT asset register to track status throughout the lifecycle.
- Invest in an IT asset management solution that can effectively discover IT assets and their lifecycle status.
- Independently verify IT asset lifecycle status regularly.
- Integrate the IT asset lifecycle with other ITSM practices, i.e., configuration management, change enablement, service financial management, incident management, problem management, etc.
Conclusion
The value of IT assets can only be assured by tracking their status across the IT asset lifecycle and making the information available to stakeholders in a timely and accurate manner. Investing in the right tools makes a big difference when it comes to effectively managing IT assets, whether on-premises or cloud-hosted, thereby ensuring that financial, regulatory, and contractual requirements are always met.