Happy Halloween from all of us over at Device42! This special post isn’t about giving away candy or spooky costumes, but instead is about Zombies. Zombie servers, that is! Zombie servers are present in data centers all over the world, and their effects wreak silent havoc on the bottom lines of companies of all sizes. The good news is that Device42 has added new features that make locating zombie servers even easier. The newly added resource utilization features are available today, and besides helping you with capacity planning, migrations, and a host of other digital transformation projects alike, resource utilization data is a powerful ally in the fight against zombies in your data center. In fact, when used together with information gleaned from Device42’s ADM (application dependency mapping), zombies become almost as easy to see as lit jack-o-lanterns on Halloween!

Why do we have to kill zombies? Well, we’ll go into more detail below, but the long and short of it is that no matter what digital transformation plans you have upcoming or already in the works, zombie servers actively (and passively!) stand between those plans and getting the most from your data center. Besides wasting expensive space and resources, did you know they can also be a rather serious security risk? Scary indeed! Zombies have no place in an agile organization, and therefore they surely have no place in your organization. Device42, with trusty dependency and topology diagrams, and now with resource utilization, is here to help.
What is a Zombie Server?
Zombie servers are servers that take up valuable resources in your data center without doing anything useful. They often consume power and pump out heat in a rack while providing nothing in return, and they take up scarce rack space that could be used for something else. Zombies can even be found during an audit in a powered off state. Some might have been left running amid configuration when an employee transitioned, while others might have been configured for a temporary purpose long forgotten. Though zombies can come into existence for several reasons, they all share a common trait: they all take from your bottom line without contributing!
Zombies are particularly hard to find, however, because they are disguised as completely normal servers! Unlike our customary Halloween costumes that make us stand out, typical zombie attire makes them more likely to blend in! Zombies therefore need to be identified in other ways:
Zombies come in many different forms, some more obvious than others:
- Zombies may exist that simply have no software installed
- Some Zombies may have software installed but have no services running
- Other Zombies yet might have installed software and/or services, but nothing connects to utilize them (nothing is dependent)
- Servers that experience unnoticed partial hardware failure could become zombies
- Zombies could be powered off in the rack, hiding until the next audit
Whatever caused each server to end up a zombie, one thing is certain: it’s best to find and eliminate them. Besides wasting valuable space and power and pumping out heat, zombie servers can sometimes be more harmful than the cost of wasted capital and otherwise useful data center space they consume might at first indicate. How is this so?
Remember, zombie servers don’t become zombie servers because they’re being actively watched — They become zombie servers because they were put in place temporarily, or for some long-forgotten purpose, while documentation concerning the zombie was either entered incorrectly, lost, or skipped entirely. As forgotten servers, they are also likely unpatched, and can serve as an ideal attack vector for a malicious actor to gain access to your network. Think of all the possible vulnerabilities!
A Firewall Isn’t Enough Anymore

The days of running unpatched servers behind a firewall or two with a DMZ and calling it secure are long past, as the data many organizations are entrusted to hold safe is simply too important, while the threats become ever more sophisticated. Zombies, by their nature, are hidden from the update process as well as from sight, and thus don’t receive the regular updates they need to stay secure. These unpatched servers can leave a gaping hole that could allow an attacker to completely bypass your firewall, and therefore must be located and eliminated.
For many of these vulnerabilities, the only solution is a patch or upgrade. Even stable and LTS (long term support) operating system releases aren’t immune, needing updates applied regularly to remain secure. Unfortunately for the security of your infrastructure, many of these OS’s require some level of manual intervention to install, or at least administrator approval, as many of the most critical updates require a reboot to install. These patches usually address low-level kernel vulnerabilities, or were just written as such (Windows Server, we’re looking at you).
To stay safe, it’s a good idea to make a zombie server sweep a regular thing. Possibly monthly or quarterly, assign someone to lead the search and scan your infrastructure for undocumented zombies, and when found, to act on them. Locate them, document them, update them, or re-purpose or decommission them entirely. Go with whatever option makes the most sense for your organization, but whatever you do, don’t leave them alone!
Device42 helps you find and eliminate Zombies
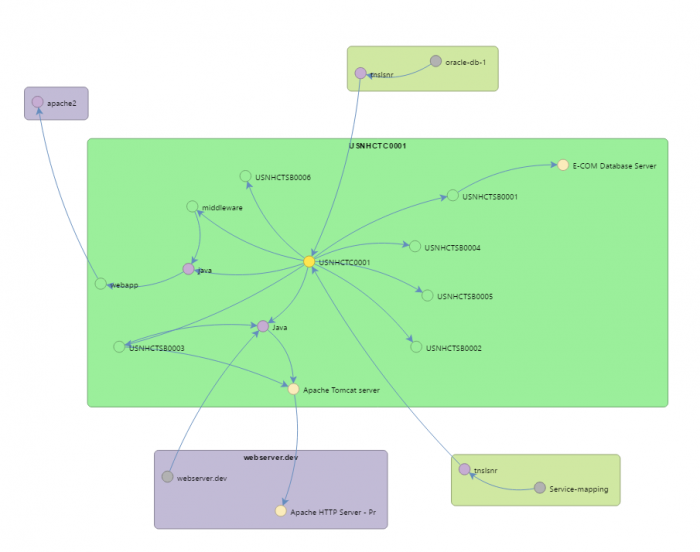
As we’ve noted, zombie servers aren’t easy to find at first glance. On the surface, zombies look like every other server in your datacenter. Zombies, however, waste precious resources, taking up space and costing your bottom line. They also can escape updates, and pose a security risk. Device42, however, helps you see past the disguise, allowing you to find and kill these zombie servers.
The good news is that identifying zombies in your data center can represent an opportunity to recoup valuable data center space, cut the power bill, and/or depending on how many are out there, discovering them could even help you postpone a migration or data center expansion by putting them to use. As a matter of fact, zombies come in a variety of forms.
Device42’s software and services module has been helping identify potential zombies with no software or services installed even before we added these new resource utilization tools to our ‘arsenal’. Comprehensive autodiscovery and powerful dependency diagrams have been assisting in the location of other could-be zombies by highlighting devices that have no connections, or only unimportant incoming and outgoing connections.
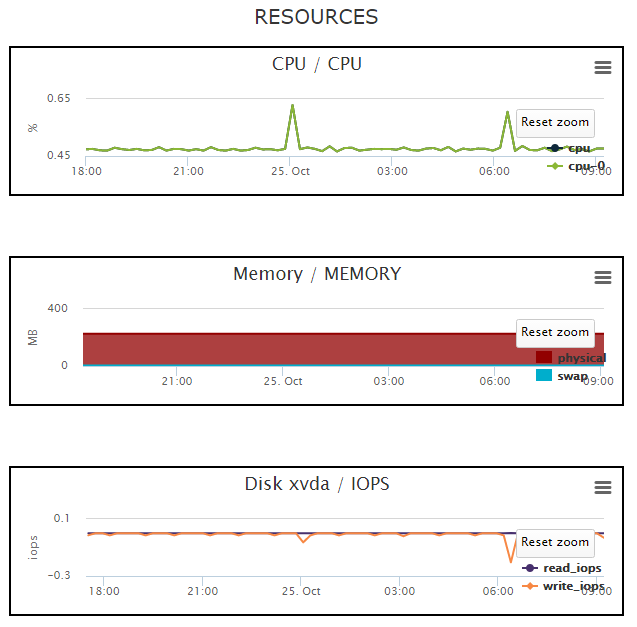
With our most recent addition, resource utilization, Device42 truly closes the loop on zombies, and knowing which servers to investigate is easier than ever!
Once you have resource utilization data exported, you can search for servers that are highly utilized but have few to no connections, and are just thus burning CPU and memory, or for servers that are sitting idle and doing your organization no good. What you do with them is up to you!
Download Device42 Today!
If you are already a Device42 user, make sure you’re using the latest version and take the new resource utilization features for a spin to see if there are any zombie servers hiding around your IT organization. If you are new around here, Download Device42 Today! It’s 100% free to try for 30 days, and you’ll be finding zombie servers before you know it!
Trick or Treat! We hope everyone has a safe and fun holiday!
Happy Halloween, and happy zombie hunting!
Questions? Comments? We love hearing from all of you. Leave a comment below, or email [email protected]



