Vulnerability Remediation Best Practices
Vulnerability remediation is critical in modern security operations, especially within platforms that monitor and manage large-scale IT and cloud infrastructures. These platforms provide ongoing insight into system weaknesses, but recognizing vulnerabilities is just the start: the real challenge is to act on that information swiftly, consistently, and through their resolution.
This article outlines key best practices that help organizations remediate vulnerabilities efficiently. The practices depend upon asset visibility, discovery processes, and operational planning. They serve regulated sectors, business IT, and hybrid cloud systems that require immediate remediation and precise asset data. By the end of this article, you will understand how to structure, prioritize, automate, and validate remediation efforts using a risk-based prioritization approach.
Summary of vulnerability remediation best practices
| Best practice | Description |
|---|---|
| Maintain an accurate CMDB | Ensure that the Configuration Management Database (CMDB) is continuously updated to reflect current asset states, ownership, and operational context. |
| Automate asset discovery and reconciliation | Use discovery tools to detect unmanaged or shadow assets and reconcile them with the CMDB. |
| Correlate vulnerability data with asset context | Link scanner data to CMDB records to provide business context for prioritization and task ownership. |
| Prioritize based on risk and business impact | Combine Common Vulnerability Scoring System (CVSS), Exploit Prediction Scoring System (EPSS), exposure, and criticality to rank vulnerabilities for remediation. |
| Define and enforce remediation workflows | Establish clear phases, responsibilities, and Service Level Agreements (SLAs) across teams to guide remediation execution. |
| Automate remediation for common vulnerabilities | Leverage orchestration tools to deploy patches or config changes for routine, low-risk issues. |
| Confirm remediation and update records | Validate fixes through rescanning, ensure that systems function properly, and document updates in the CMDB. |
Maintain an accurate CMDB
A precise configuration management database (CMDB) is the foundation of an effective vulnerability remediation process. It delivers full transparency about systems, including their existence, status, ownership, and interconnections. A CMDB must be accurate and comprehensive to enable effective remediation.
Achieving accuracy will almost always require a mix of automated discovery tools and regular audits to discover and reconcile discrepancies. Discrepancies in CMDB data that are inaccurate in time may result in remediation teams missing critical assets or taking actions against the wrong systems.
The CMDB must include comprehensive details about system relationships and dependencies in addition to static asset lists. These interdependencies are essential because they demonstrate the complete impact of vulnerabilities or configuration changes. For instance, the team can resolve a higher-priority vulnerability if they know the database server supports a customer-facing application.
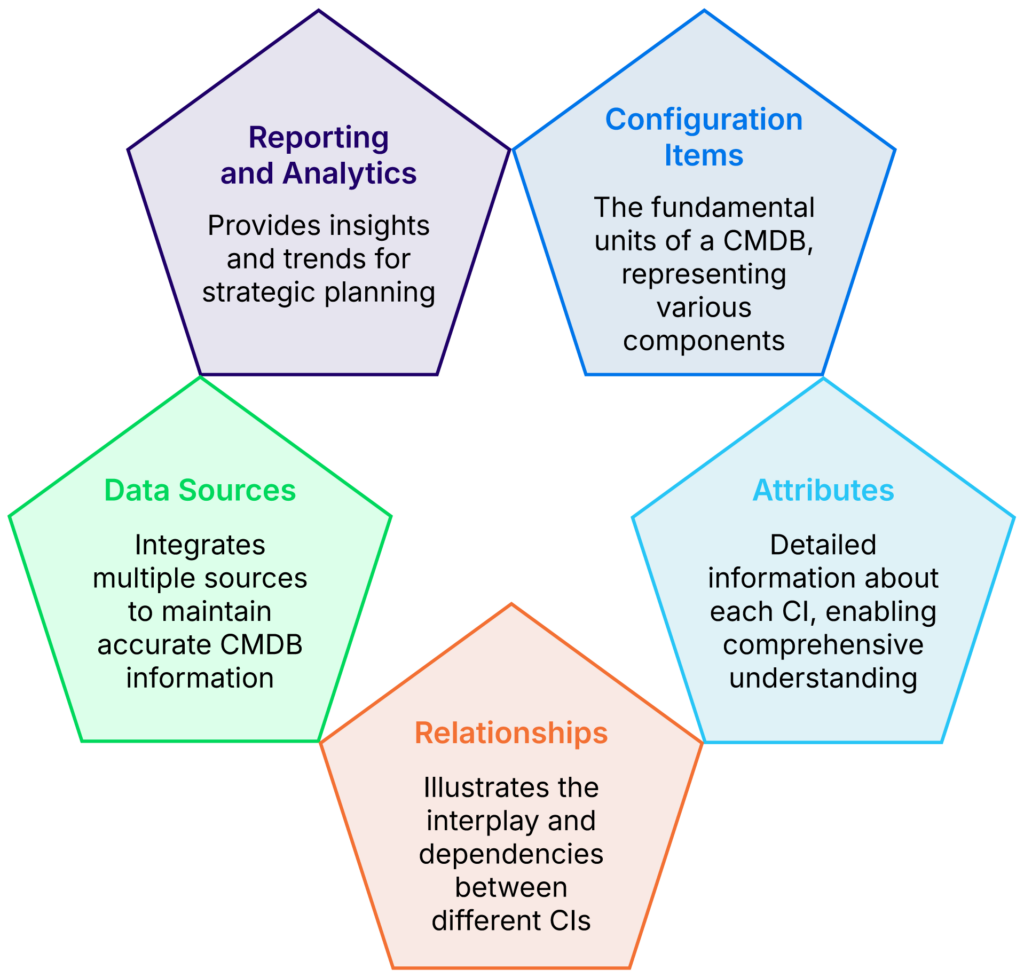
Key components of an effective CMDB (source)
The figure above illustrates the essential components of a well-maintained CMDB that supports effective vulnerability remediation. Configuration Items (CIs) serve as the foundation by representing all tracked assets, while attributes capture the critical details needed to understand each asset’s role and risk profile fully. Relationships illustrate the interdependencies between systems, an essential factor in determining the true impact of vulnerabilities or changes. Automated data sources ensure that asset information remains current through continuous updates and discovery, while reporting and analytics provide the insights necessary for planning and compliance.
Together, these components define what makes a CMDB accurate, comprehensive, and consistent with the criteria described above to deliver remediation work that is appropriately prioritized, complete, and based on authoritative operational data.
IT service management processes (incident response, change control, etc.) must be tightly coupled to the CMDB to support effective asset lifecycle management. This relationship ensures that remediation activities leverage complete data while consistently documenting completion. In the following example, a financial services organization used a correct and fully integrated CMDB to resolve a data center outage quickly by following these steps:
- Initial issue: Critical vulnerabilities were left unaddressed, resulting in service disruption.
- Root cause: Lack of asset visibility and dependency mapping.
- Solution: Implementation of a centralized, accurate CMDB.
- Action taken: Documented all configuration items and their interdependencies.
- Result: Vulnerability remediation efforts were better prioritized and timed by understanding system dependencies.
- Outcome: Reduced missed remediation windows and improved vulnerability coverage across critical systems.
Automate asset discovery and reconciliation
Organizations should implement continuous, automated asset discovery across all environments to support scalable and reliable vulnerability remediation. Manual inventories are error-prone and quickly become outdated, introducing security blind spots. A regular discovery process can detect new devices, virtual machines, containers, cloud workloads, and applications when they come online.
Security and IT teams should select discovery tools beyond basic network scans. Look for solutions to identify dynamic and transient assets such as ephemeral cloud resources, SaaS applications, and microservices. The discovery process should integrate directly with your configuration management database (CMDB) to maintain accurate, up-to-date asset records without requiring manual reconciliation.
Integrate your asset discovery system with your IT service management (ITSM) platform where possible. Whenever newly discovered assets are automatically recorded and linked to known configuration items, vulnerability data can immediately be relayed to the appropriate owners and business units, eliminating inefficiency and delays.
As mentioned previously, prioritize the platforms’ generated dependency mapping capabilities. Understanding how these assets are tied together in technical and business services gives you a greater understanding of the context of the vulnerabilities. This clarifies how a baseline level of remediation is established to guide sequencing, timing, and risk acceptance decisions in complex environments with mission-critical applications.
The table below outlines the specific stages where automation should be applied in your environment.
| Stage | Action to take |
|---|---|
| Asset visibility | Implement continuous discovery tools that identify and update asset records in real time across all environments, including on-premises, cloud, and hybrid systems. |
| Unmanaged asset detection | Deploy discovery processes that automatically identify and flag shadow IT, unauthorized devices, and unmanaged cloud resources for remediation. |
| CMDB maintenance | Integrate asset discovery with the CMDB to facilitate automatic reconciliation of newly identified assets and to eliminate obsolete ones. |
| Dependency mapping | Utilize discovery tools that automatically chart system dependencies, allowing for a clear understanding of asset relationships and accurate prioritization of remediation efforts. |
| Asset classification | Apply dynamic tagging and classification rules so newly discovered assets are categorized by criticality, environment, and ownership without manual intervention. |
Correlate vulnerability data with asset context
To prioritize and resolve vulnerabilities effectively, security teams must go beyond raw scan results and link each finding to detailed asset metadata. Correlating vulnerability data with contextual asset information, such as ownership, system role, business function, and network exposure, transforms static risk scores into actionable intelligence.
Once vulnerabilities are identified, platforms integrating tightly with the CMDB can automatically enrich findings with asset-specific attributes. These include whether the system is in production or staging, whether it supports a critical application, or whether it is publicly exposed. Without this context, a vulnerability on a low-value test server might be treated with the same urgency as one on a customer-facing web application, wasting resources and increasing risk.
Organizations should invest in platforms that allow flexible asset tagging and automatic task assignments, thereby increasing remediation velocity and accountability. By connecting the vulnerabilities to system owners with contextual CMDB data and labeling the asset by function, priority, and/or compliance scope, the remediation tickets can be processed, prioritized, and routed to the correct team automatically. This eliminates manual triage effort, mitigates SLA breaches, and provides remediation opportunities defined by the organization’s overall risk profile.
The example below highlights how two identical vulnerabilities with the same CVSS score can require vastly different responses depending on the asset context. While Server A resides in an internal QA environment with limited exposure and low business impact, Server B supports a customer-facing application and is publicly accessible.
| Attribute | Server A | Server B |
|---|---|---|
| Vulnerability | Remote code execution | Remote code execution |
| CVSS score | 9.8 | 9.8 |
| Asset type | Internal QA environment | Public-facing production server |
| Business role | Non-critical, isolated | Supports a customer-facing application |
| Network exposure | Internal only | Externally accessible |
| Remediation priority | Medium—scheduled for routine patching | Critical—requires immediate remediation |
Prioritize based on risk and business impact
Organizations with limited time and resources must prioritize vulnerabilities based on severity scores and the risks that the vulnerabilities pose to the business. Effective prioritization is a multi-factor process that evaluates technical indicators and contextual asset information to guide remediation efforts where they matter most.
Instead of treating all high-CVSS vulnerabilities equally, organizations should adopt a risk-based model that blends several key inputs, as shown in the following table.
| Input | What it measures | Why it matters |
|---|---|---|
| CVSS score | Technical severity of the vulnerability | Establishes baseline impact based on vulnerability characteristics |
| EPSS score | Likelihood that a software vulnerability will be exploited in the wild | Helps prioritize vulnerabilities with real-world attack potential |
| Asset criticality | Importance of the affected system to business operations | Ensures that critical business services are protected first |
| Exposure level | Network accessibility (e.g., internet-facing vs. internal) | When higher, increases the likelihood and impact of exploitation |
The example below illustrates how two vulnerabilities with different contextual attributes are prioritized using a risk-based approach. Despite Vulnerability A’s higher CVSS score, Vulnerability B receives higher priority due to greater exposure, business impact, and likelihood of exploitation.
| Vulnerability | CVSS score | EPSS score | Asset type | Exposure | Final priority |
|---|---|---|---|---|---|
| A | 8.2 | 0.02 | Internal print server | Internal | Medium |
| B | 6.5 | 0.91 | Public-facing web app | External | Critical |
This example underscores the necessity of looking beyond mere severity when prioritizing vulnerabilities. While conventional models prioritize the highest CVSS score, considering factors such as exposure and business impact provides a clearer picture of actual risk. Here, a lower-scoring vulnerability represented a more pressing threat because it was in a critical, internet-facing environment. This illustrates how contextual risk scoring helps target remediation efforts effectively. Context-aware platforms integrating asset metadata and risk scoring can enhance prioritization and streamline task assignment.
Define and enforce remediation workflows
Organizations need to build managed remediation workflows that outline the evolution of any dangerous occurrence, from detection to repair, which allows consistent and fast remediation of vulnerabilities. Inconsistent remediation action often leads to miscommunication, missed deadlines, and unpatched critical infrastructure, especially in larger distributed environments.
A well-defined remediation workflow should cover every phase of the response lifecycle as shown in the illustration below:
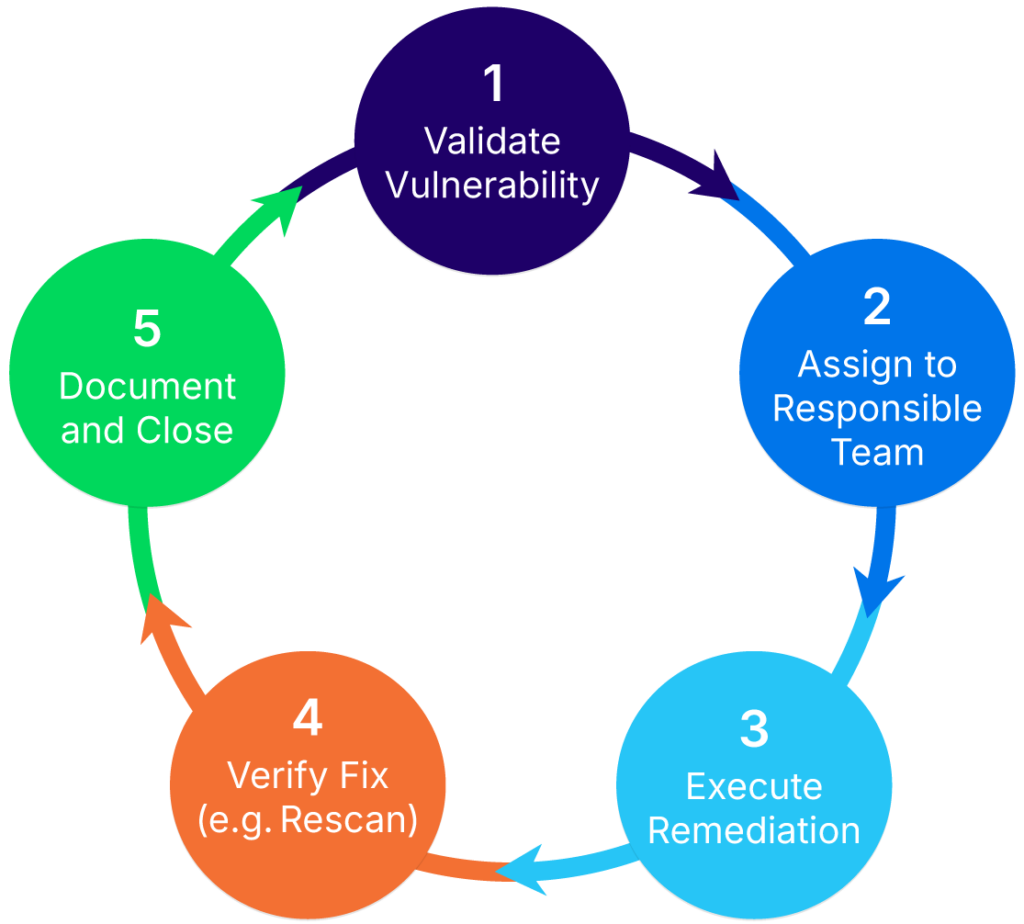
Vulnerability remediation cycle (source)
Each phase should be structured to ensure accountability, minimize delays, and support traceability. These workflows are especially critical in large organizations where multiple teams may be involved across departments, regions, or systems.
Organizations should incorporate vulnerability management solutions with ITSM platforms to operationalize their workflows. Ticketing systems like ServiceNow and Freshservice should automatically generate tasks for verified vulnerabilities, assign those tasks based on asset ownership, and track completion against the service-level agreement (SLA). In addition, workflows should incorporate escalation paths for unaddressed issues to ensure that high-risk vulnerabilities do not go unattended because of process gaps.
The roles and responsibilities of the application, infrastructure, and security teams should be well-defined within the process. Every stage should include documentation to guarantee that all remedial efforts can be tracked and that they align with internal controls or regulatory requirements.
Defining a structured remediation workflow requires more than setting guidelines—it necessitates embedding automation, accountability, and escalation mechanisms into day-to-day vulnerability management processes. The table below outlines key actions to enforce consistent, efficient remediation across your organization.
| Stage | Action to take |
|---|---|
| Ticket creation | Configure vulnerability management tools to generate remediation tickets automatically upon vulnerability validation. |
| Task assignment | Route remediation tickets directly to the responsible asset owners or teams based on CMDB data. |
| SLA enforcement | Embed service-level agreements (SLAs) within the workflow to track resolution timelines and trigger automatic escalations for overdue vulnerabilities. |
| Resolution consistency | Standardize remediation workflows across all business units to ensure consistent vulnerability handling, regardless of team or geography. |
| Risk oversight and reporting | Centralize the tracking and reporting of remediation activities to maintain transparency, enable audit readiness, and support executive reporting. |
Automate remediation for common vulnerabilities
In modern IT environments where thousands of vulnerabilities are detected regularly, not all issues require manual attention. Automating the remediation of recurring or low-complexity vulnerabilities can drastically reduce operational overhead and improve response times without sacrificing control or oversight.
Automation is most effective for well-understood issues that follow predictable remediation patterns. These typically include outdated software versions, misconfigurations, missing agents, and unsupported protocols. Security and IT teams must implement automation to apply patches, adjust configurations, or execute predefined remediation actions for confirmed vulnerabilities. These can be performed through tools such as configuration management systems, orchestration systems, or native integration via endpoint management systems.
Automation should be implemented in phases to ensure reliability and minimize risk. Start with noncritical systems or sandbox environments and validate outcomes through monitoring or rescanning. As confidence in automated processes grows, the organization can expand the scope to cover broader asset classes or deploy auto-remediation in near real time for specific use cases, such as browser updates or agent reinstallations.
Policies and procedures with audit trails must govern automation. Every automated action related to an event requires logging using a process consistent with change control. This should provide traceability and accountability for compliance in a regulated environment.
In one case, a large organization automated remediation for recurring low-risk vulnerabilities, specifically outdated browser versions on employee workstations. The process began with scheduled vulnerability scans that detected non-compliant software versions. Once identified, the system automatically triggered a remediation workflow using an orchestration tool. The updates were deployed during off-hours to avoid disruption, and post-remediation checks confirmed the fixes were successful. This automation significantly reduced the time required to remediate these vulnerabilities, from several days to just a few hours, while eliminating manual intervention.
Confirm remediation and update records
When an organization remediates a task, the vulnerability management process is not necessarily completed. To achieve completion, all remediation tasks must be validated and recorded. When this doesn’t happen, organizations may believe that at-risk systems have been remediated when, in reality, they remain unremediated and at risk. Validating remediation work demonstrates integrity and a long-term commitment to security.
Remediation should always include a verification phase. The best option is to check with an automated scan or sensor, which allows verification that the specific vulnerability no longer exists on the asset. It is essential to verify that the appropriate and effective fix has been applied, not rolled back, and not removed or blocked by configurations. Verification is also formal proof of compliance in regulated environments.
Updating internal records is just as important. The CMDB should reflect the current state of each asset, in terms of configuration, patching level, or ownership, that resulted from the remediation. As all internal records are updated, they will improve the efficiency, accuracy, or reliability of future scans, asset assessments, or impact analysis. Failing to maintain accurate records, either when dealing with changed conditions or while the records are being updated, can pose increased risk or confusion in ownership or delay in effective incident response chronicling at a later date.
Additionally, teams want to develop a clear audit trail of all remediation actions. This should include closure notes informing them of each ticket’s closure date/time of remediation, who remediated it, and proof of successful remediation. This audit trail demonstrates accountability and makes reporting easier for auditors, regulators, and senior leadership sponsors.
The following summarizes a real-life remediation event that stresses the importance of verification and record-keeping in confirming that the vulnerability was fixed and documented:
- Initial remediation: A security patch was applied to the affected system.
- Verification scan: A follow-up scan detected that the vulnerability was still present.
- Root cause analysis: Analysis revealed a patch failure due to a missing system dependency.
- Corrective action: The dependency was installed, and the patch reapplied.
- Validation: A second scan confirmed that the vulnerability was no longer present.
- Record update: The CMDB was updated with the patch level and configuration details.
- Closure: The ticket was closed with documented resolution and validation evidence.
Conclusion
Effective vulnerability remediation depends on identifying risks and the ability to act on them with precision, context, and speed. This article presented a set of best practices forming a structured, risk-based approach to remediation, beginning with a reliable, continuously updated CMDB as the foundation.
Automated asset discovery ensures no system is overlooked, while linking vulnerability data to asset context supports better prioritization. Risk-based prioritization allows you to utilize CVSS, EPSS, and asset criticality and other context-specific inputs to determine which remediation actions will justify limited resources. Repeatable workflows ensure consistency between teams, and automation allows teams to mitigate low-impact actions more quickly and at scale. Finally, proper validation and documentation reinforce remediation efforts, ensuring accountability and audit-readiness.
By implementing these practices, security and IT teams can reduce exposure, minimize operational disruptions, and move from reactive vulnerability management to proactive risk reduction.