Designing a User-Centric ITSM Service Catalog: Best Practices
The modern IT enterprise is characterized by flows of information related to the production and consumption of IT services. To meet current and future enterprise needs for IT products and services, a common understanding of what is offered by the service provider is essential. And it’s not only current and potential users and customers who will be interested in this information. Other stakeholders within the enterprise will also want visibility into which IT services are currently available or on the horizon for the purposes of planning, budgeting, vendor management, compliance, or other business reasons. For IT operations teams, the service catalog serves as a critical reference point for incident response, asset tracking, configuration management, and understanding service dependencies.
The ITIL 4 framework defines a service catalog as the structured information about all the services and service offerings of a provider that are relevant to a specific target audience. To meet the needs of different stakeholders, the ITSM service catalog has to be created, marketed, and updated based on the requirements of different IT stakeholders, including users, consumers (i.e., the business), and the service provider’s staff. Managing the service catalog involves capturing the requisite information about current and anticipated IT services and presenting it in a manner that suits the needs of those interested in them.
This article covers best practices in managing an ITSM service catalog, providing practical guidance for developing and deploying a fit-for-purpose ITSM service catalogue that supports service mapping, incident response, and IT asset management.
Summary of essential ITSM service catalog management best practices
A summary of ITSM service catalog management best practices is provided in the table below.
| Best practice | Description |
|---|---|
| Analyze ITSM stakeholder requirements | Identify and analyze relevant stakeholders and their needs for input into the catalog design. |
| Discover services using application dependency mapping | Use automated discovery and application dependency mapping to identify services and relationships across your environment. |
| Define the right catalog data structure | Ensure that the right data fields for present and future needs are defined and tested. |
| Map services to infrastructure components | Establish relationships between catalog entries and underlying configuration items, assets, and dependencies. |
| Integrate the service catalog with ITSM systems | Use the service catalog to link to ITSM ticketing systems for tracking service status, requests, assets, and configurations. |
| Maintain service catalog accuracy | Implement processes to keep catalog entries synchronized with actual infrastructure and service changes. |
| Track service catalog operational effectiveness | Establish and report metrics and indicators for service catalog content quality and operational effectiveness. |
Analyze ITSM stakeholder requirements
The IT services that an organization provides during interactions with its consumers result in a service relationship. To start this relationship, the service provider must present a service offering to a potential consumer, who agrees to use the service. The ITSM service catalog is a subset of the service portfolio that lists the deployed and released IT services that are available to users and consumers.
For IT operations teams, a good starting point is understanding which infrastructure components, applications, and configuration items support each service—information essential for incident triage and root cause analysis.
The ITSM service catalog requirements that inform the definition of services and the structure of the catalog can also be informed by vendor datasheets, industry standards, discovery tool outputs, and applicable compliance needs. For example, the ISO/IEC 20000-1:2018 standard for service management requires that the service catalog include the descriptions, intended outcomes, and dependencies of IT services.
Qualifying IT services can start with a distinction of visibility to the customer through the following:
- Customer-facing services: These are IT services that are seen by the consumer and directly facilitate their desired outcomes and business processes. Examples include services accessed via desktop applications, web browsers, mobile apps, sensors, and robots, among other end-user devices.
- Supporting services: These IT services underpin the customer-facing services and are typically invisible to the customer. These include infrastructure services, network services, and technical services.
Each service in the catalog needs to be represented with its full supporting stack to be operationally useful. Consider a reporting service as an example. End users see a web interface, but behind that sits middleware handling application logic, a SQL database storing the data, and storage infrastructure like a Hitachi array keeping everything persistent. If any layer fails, the service fails—but incident responders can only troubleshoot effectively if all these components are documented and linked to the service. During stakeholder analysis, work with application owners and infrastructure teams to identify what sits beneath each service. This information needs to be captured in the ITSM backend so the service catalog reflects not just what users consume, but what IT must maintain and monitor to deliver it (more on this in the next section).
Analyzing stakeholder requirements enables the person responsible for the service catalog to make the right decisions in determining the sources of the ITSM service catalog content, the level of granularity required, and content presentation expected. Should stakeholder requirements differ significantly, a consultative approach to find that a compromise position may be required; otherwise, the IT service provider may find it difficult to consolidate and maintain the right information to suit all parties.
Discover services using application dependency mapping
Once the business level analysis is complete, consider the technical aspect to know what services actually exist in your environment and how they’re related. Many organizations struggle with this step often because service definitions are either non-existent or there is not a single source of truth that retains the info. Application dependency mapping (ADM) provides a systematic approach to discovering and documenting services based on actual infrastructure relationships.
To build this technical map, most teams choose between agentless and agent-based discovery methods. While both approaches offer similar capabilities, the choice often depends on your network architecture and security rules. Agentless discovery is an excellent starting point because it provides broad visibility quickly. When you are able to scan servers and network connections without installing extra software, you can create a reliable baseline of your environment in a very short time.
However, choosing to use an agent is often a matter of communication patterns rather than just data depth. For example, servers sitting within a DMZ often have strict security rules that block inbound scanning. In these cases, agent-based discovery is required because it allows the server to send data “out” to your management system rather than waiting for a scan to come “in.” Using a mix of both methods ensures that you can map your entire environment regardless of whether a server is easily reachable or tucked behind a restrictive firewall.
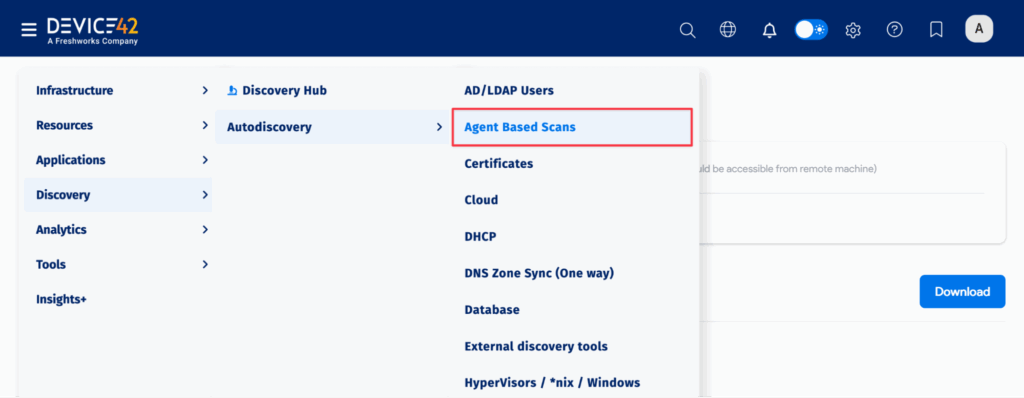
Device42 offers both agentless and agent-based discovery
Keep in mind that some environments present unique challenges. Some legacy systems or air-gapped networks may not be fully visible to discovery tools, and may require manual documentation to fill gaps. Separately, cloud and container environments with ephemeral infrastructure need discovery tools designed to track dynamic resources and map services that don’t run on fixed servers.
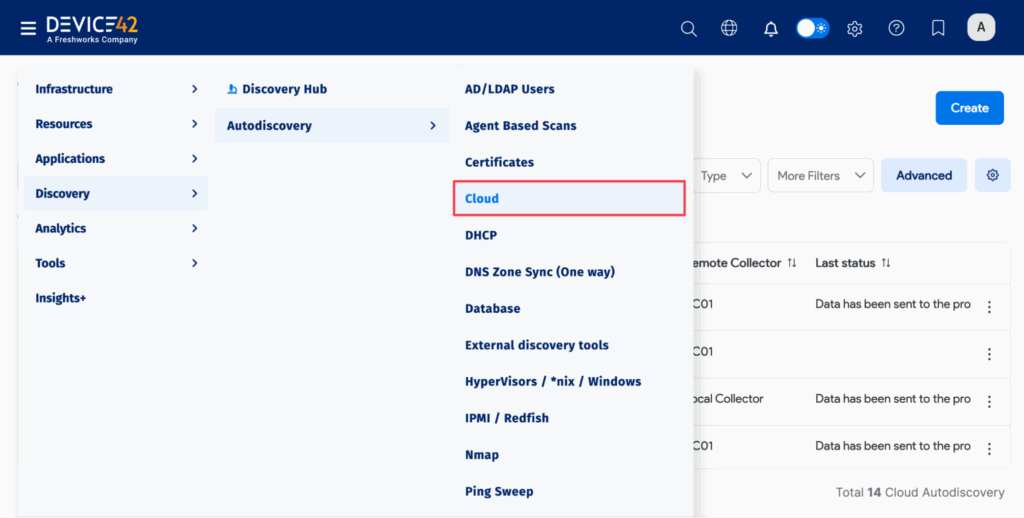
Device42 cloud platform autodiscovery
You don’t need to document everything at once. Focus your initial discovery efforts on business-critical services or those that experience frequent incidents. This approach delivers immediate operational value and builds momentum for broader coverage over time.
Before you begin mapping, decide how granular your service definitions should be. Similarly, consider how deep to go with dependencies. Mapping every downstream connection would likely create overwhelming complexity, while shallow mapping may miss critical relationships. A practical approach is to document two to three levels of dependencies for most services, while going deeper only for your most critical ones.
The output of application dependency mapping will provide the raw material for service catalog entries. For each identified service, the mapping data contributes the list of associated servers and infrastructure, application components and their versions, network dependencies and communication flows, and upstream and downstream service relationships.
While automated discovery can reveal technical relationships, it cannot tell you where one service ends and another begins. For instance, two systems communicating doesn’t necessarily mean they belong to the same service. You’ll need to go back to validate discovered data with application owners and operations teams who understand how services are actually delivered and supported. Consider using tools that can streamline this validation process by providing visual dependency maps that make it easier for stakeholders to confirm relationships and identify service boundaries.
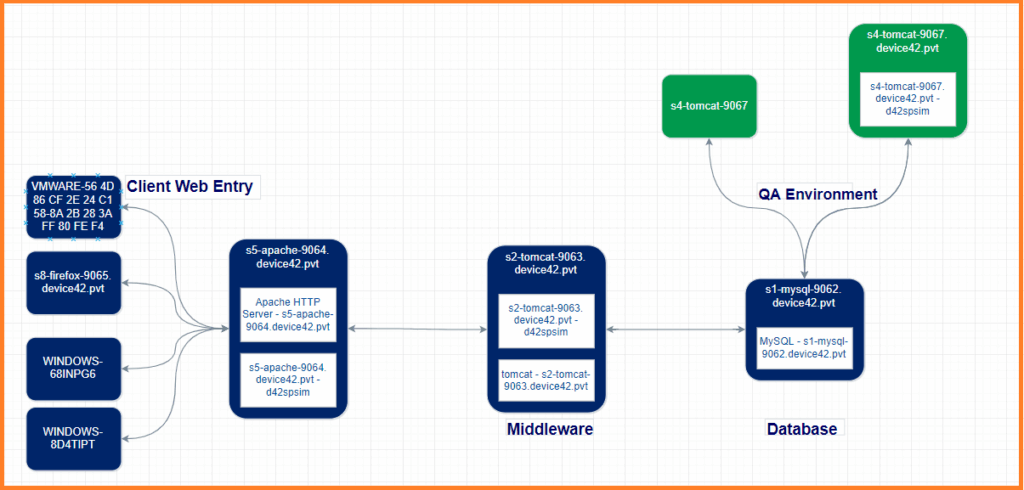
Mapping business services by leveraging Device42’s discovery and Application Group capabilities
Define the right catalog data structure
The ITSM service catalog is a key reference for setting customer expectations. In the process of designing the structure and presentation of the ITSM service catalog, the IT service provider should take into consideration the different and sometimes conflicting needs of various stakeholders. The scope of each service reflects the customer’s business activities, so the catalog structure should ultimately lead to an improved understanding of services by the relevant stakeholders. The service catalog manager is responsible for defining, designing, and maintaining the service catalog and should thus consider the key data fields required to address stakeholder requirements.
The ITSM service catalog structure should be designed so that the information is easy to maintain. By implementing a logical and efficient grouping of catalog information, the IT service provider can minimize the changes in structure that are needed whenever there are new, modified, or removed services. The organization can design a service catalog to be managed as a central database or as multiple databases that are managed by different teams, for example, product teams responsible for certain business products.
When creating the ITSM service catalog structure, it is important to think of present requirements but also anticipate future needs. The set of service attributes required has to be carefully selected so that they describe and remain applicable to both current and future services that are in the IT service portfolio. Here are some examples of such attributes:
- Unique identifier
- Service name
- Description
- Owner
- Status
- Criticality/priority tier
- Technical and business dependencies
- Associated configuration items and assets
- SLA targets and thresholds
- Linked runbooks and incident response procedures
- Related IT assets (hardware, software licenses, subscriptions)
The data structure of the ITSM service catalog should be analyzed to define the technical approach to collect and maintain data, the approach to defining and presenting catalog views, and the requirements for automation and integration. The structure should be tested with sample data and presented to key stakeholders for validation, with their feedback incorporated. There is no single correct way to structure an ITSM catalog—each organization should consider its goals, objectives, and use cases to create a structure that meets its current and evolving needs appropriately.
Integrate the service catalog with ITSM systems
Once the structure and views are defined and agreed upon, the ITSM catalog is populated with the required service data. Some organizations may go for a manual catalog that is maintained as a physical document, while others may prefer a digital format like a document or spreadsheet. However, both are quite limiting in many ways since a service catalog needs to be easily accessible to stakeholders and must be updated quickly and efficiently. A better form is to host it in digital form through an intranet, web portal, or use a dedicated discovery and CMDB platform that feeds accurate, up-to-date service data into your ITSM tool. Regardless of the digital format deployed, integrating the service catalog with existing ITSM systems can maximize its value.
An integrated ITSM toolset can leverage automated discovery to help the IT service provider map services to underlying IT components, which aids in understanding and monitoring the actual status of IT services. The presentation of services on the ITSM service catalog can highlight to both users and support teams whether the services are up and performing as expected through monitoring information that is summarized via real-time status flags. This benefits users during the process of researching or requesting services, and it also reduces the amount of back and forth with the service provider for services that are out of order.
The ITSM service catalog can also be linked with your ITSM ticketing system for one-stop request handling. Request catalogs are a type of view addressed to users that provides details on new and existing services available for requesting. The user can submit a request for access or a device specific to an IT service, and that request is routed via workflow from the service catalog to an approver (if required), then assigned to a staff member or third-party provider for fulfillment.
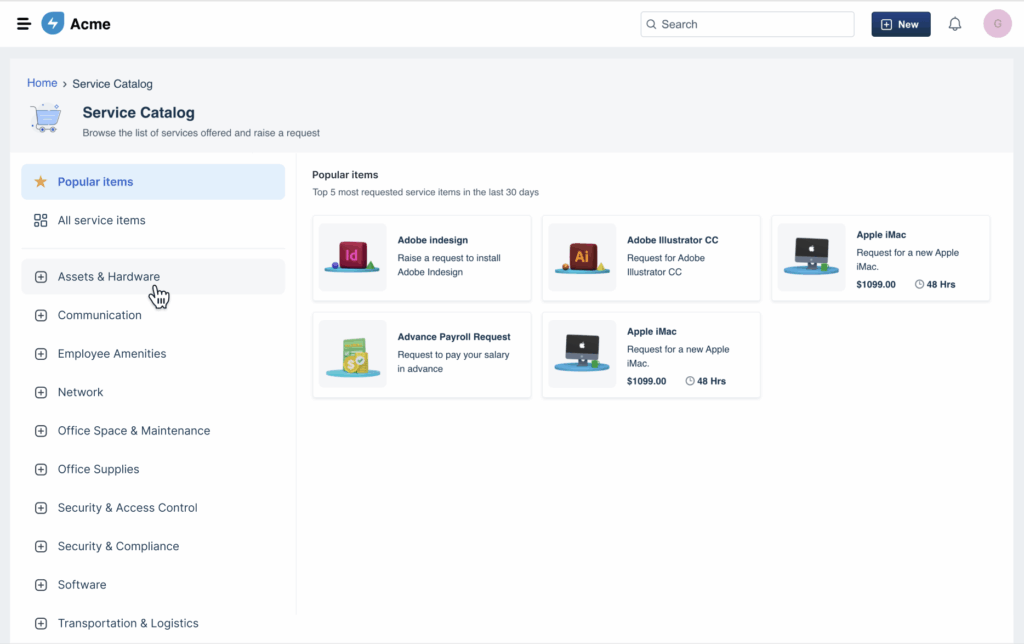
Freshservice allows you to create multi-level service catalog
In addition, the ITSM service catalog can be integrated with existing IT asset inventory systems to track the demand, cost, and issuance of subscriptions, licences, and user devices related to the specific services requested. This can be extremely valuable in analyzing end-to-end service costs, particularly concerning consumption and utilization. Integrating the ITSM service catalog with a CMDB can help you visualize the relationships between the catalog entries and underlying service components, which is critical to determining service value and supporting the service during incidents and problems.
Maintain service catalog accuracy
Your ITSM service catalog should be regularly updated to remain relevant in supporting IT service management activities. Whenever changes are made to the service portfolio that impact live services (introduction or withdrawal), the same should be reflected in the service catalog. Alternatively, whenever there are changes in the organizational structure that affect request approval workflows or stakeholder requirements regarding the look and feel of the catalog, these should be formally implemented on the ITSM service catalog in a controlled manner.
Organizations that rely solely on manual catalog updates typically see data accuracy degrade within a few months of initial documentation. A recommended approach is to utilize automated discovery combined with scheduled reconciliation to maintain accuracy rates.
Your service catalog maintenance should be integrated with existing IT processes:
- Change management integration: When changes are approved and implemented, the service catalog should be updated to reflect modifications to service definitions, dependencies, or underlying components. Consider making catalog updates a required step in change closure. Practically, this means adding a mandatory field in your change ticket template that asks “Does this change affect any service catalog entries?” and blocking ticket closure until the field is addressed. You can even go further by requiring the change implementer to attach a screenshot of the updated catalog entry or a confirmation from the CMDB that the change has been synced.
- Discovery reconciliation: Schedule regular comparisons between catalog entries and automated discovery data to identify infrastructure drift, new components, or decommissioned assets that haven’t been reflected in service definitions. Weekly or bi-weekly reconciliation works for most environments, though organizations with high rates of infrastructure change may need daily comparisons. The reconciliation process should generate exception reports that highlight mismatches. For example, a server listed in the catalog that discovery no longer sees, a new application dependency that wasn’t documented, or a configuration item that has moved to different infrastructure. These exceptions should be assigned owners and tracked to resolution like any other operational task.
- Incident and problem management feedback: Root cause analyses often reveal previously unknown service dependencies or incorrect mappings. Establish a feedback loop to capture these findings and update the catalog accordingly. Consider adding a standard question to your postmortem template like “Were all affected components and dependencies accurately documented in the service catalog?” When the answer is no, create a follow-up task to correct the catalog as part of the incident’s remediation actions. Over time, this creates a self-correcting mechanism where incidents drive catalog improvements.
Track service catalog operational effectiveness
An ITSM service catalog’s value is a function of the quality of information it possesses and how much it is used by IT operations teams. The IT service provider should establish metrics and performance indicators to track the completeness of the service catalog and its effectiveness in supporting operational processes. Collecting metrics related to hits and interactions will allow the service catalog manager to monitor and analyze use patterns, preferred views, and most frequent searches. Surveys on the quality of information and user friendliness in navigating the ITSM service catalog pages should be regularly conducted, especially after each interaction.
Consider adopting metrics for measuring service catalog operational value include:
- Service mapping coverage: The percentage of catalog entries with complete service-to-infrastructure mappings, indicating how useful the catalog will be during incident response.
- Catalog accuracy rate: Measured through periodic audits comparing catalog entries against actual infrastructure, identifying stale or incorrect information.
- Mean time to identify service impact: How quickly IT teams can determine which services are affected during infrastructure incidents—a well-mapped catalog should reduce this metric.
- Change-to-catalog synchronization: The time lag between infrastructure changes and corresponding catalog updates, indicating how current the catalog data remains.
The service provider should also regularly analyze the impact of catalog errors and inconsistencies on supported ITSM processes. This can be carried out through formal and informal engagements with process owners, service owners, and IT operations staff to determine whether the information in the service catalog supports practices such as service level management, incident management, problem management, change management,and IT asset management, among others. Stakeholder feedback should be collated, processed, and used to generate improvements to the ITSM service catalog.
Last thoughts
A comprehensive and up-to-date ITSM service catalog is a valuable tool for enhancing the user and support staff experience during service provision and support. However, its value depends on the quality of information listed, particularly the accuracy of service-to-infrastructure mappings and integration with operational ITSM tools. Keeping the ITSM service catalog synchronized with your actual environment will ensure that IT service provider efforts to invest in it and maintain it are not wasted.