SSVC Best Practices
In modern enterprise environments, vulnerability backlogs can be overwhelming. Every week, new Common Vulnerabilities and Exposures (CVEs) flood in from various vendors, and security teams face the impossible task of deciding which to address first. Making this even more challenging is that traditional scoring models like the Common Vulnerability Scoring System (CVSS) offer a numerical severity rating, but miss the real-world context that determines whether a vulnerability is truly urgent.
This is where Stakeholder-Specific Vulnerability Categorization (SSVC) comes into play. SSVC is a decision-making framework that enables organizations to make clear choices on vulnerabilities based on real-world exploitation status, technical impact, and mission or business impact.
Developed through a collaboration between researchers at the Carnegie Mellon University Software Engineering Institute and the U.S. Cybersecurity and Infrastructure Agency (CISA), SSVC is dynamic, context-driven, and tailored to the needs of specific stakeholders.
Applying SSVC enables teams to make more effective vulnerability decisions by combining inputs from threat intelligence, asset context, and business impact. It is especially valuable for organizations overwhelmed by vulnerability backlogs or teams seeking to align remediation timelines with business risk tolerance.
Drawing on proven best practices and practical examples, this article shows cybersecurity professionals how to embed SSVC into their vulnerability management programs. Each practice is designed to make SSVC decisions timely, defensible, and tightly aligned with business priorities.
Summary of SSVC best practices
The table below summarizes the five SSVC best practices this article will explore in detail.
| Best Practice | Description |
|---|---|
| Maintain an accurate CMDB to support SSVC | SSVC is only as effective as the asset data being fed into it. Therefore, you need to ensure that your CMDB is accurate, updated with the right attributes, and includes dependencies. |
| Classify assets by mission impact | Make sure that every asset in your environment has been reviewed and assessed for its mission impact. This connects the technical vulnerability to its business impact, thereby improving vulnerability classification. |
| Collect exploitation status from trusted feeds | Using trusted threat-intelligence feeds, maintain a constant watch for any changes in the exploitation status of the vulnerabilities in your environment. If something changes, update your prioritizations accordingly. |
| Define stakeholder-specific SSVC decision paths | Leverage the different priorities of SSVC stakeholders to create a more accurate decision tree. This improves the overall impact of SSVC while generating more buy-in and trust. |
| Integrate SSVC outputs into workflows | Convert your SSVC calculations into outcomes by connecting them to remediation workflows and ticket management systems. |
| Automate SSVC decision tree evaluation | Enable your SSVC decisions to scale with your organization and vulnerability backlog by automating your decision tree evaluation. |
| Regularly reassess SSVC decisions | A vulnerability, classified by SSVC, loses relevance if the decision is not regularly reassessed in response to changing conditions. Use a combination of scheduled and event-driven reassessment criteria to ensure your SSVC remains up to date. |
A brief overview of SSVC
SSVC provides organizations with a structured decision-making process for classifying vulnerabilities. In its purest form, it distills each vulnerability into one of four vulnerability classifications:
- Track. No specific action is required other than remediating within standard timeframes.
- Track*. Requires closer monitoring, but still, no specific action is required other than remediating within standard timeframes.
- Attend. Closer attention is required by organizations, and they should consider applying remediations sooner than standard update timelines.
- Act. Closer attention is required, and, importantly, remediation should be as soon as possible.
Although the overall SSVC classification is simple, the underlying calculations are complex. Instead of relying on static severity scores (such as CVSS), which may be technically accurate but lack real-world applicability, SSVC considers five factors. Only when each of these factors is considered to the extent possible is the overall vulnerability classification derived.
The five SSVC factors are:
- Exploitation status, based on current Threat Intelligence
- Technical impact, primarily based on CVE metadata, although this can be supplemented by an organization’s internal analysis
- Automatable, referring to how easily an exploit can be integrated into the cyber kill chain
- Mission prevalence, which is analogous to mission impact or business impact,
- Public well-being impact, which is a more abstract concept that deals with the larger impacts on an organization’s operations
This approach is quite different from the Common Vulnerability Scoring System (CVSS), used prior to SSVC. CVSS focused exclusively on the technical aspects of a vulnerability, with no consideration for the operational realities an organization faced. For instance, a vulnerability classified as critical by CVSS due to its potential impact and ease of exploitation development may be less important operationally if it only exists in a non-production testing environment (mission impact). In a similar manner, a vulnerability classified as less critical by CVSS may be operationally more important if it resides on a production server holding sensitive information.
In practice, this meant that every organization applied its own logic to filter CVSS results into something that made more sense operationally. In turn, this drove the need for a more formal framework for vulnerability categorization. SSVC was the result.
What makes SSVC truly valuable to organizations is its ability to be customized within each organization to meet specific needs. Two organizations may have vastly different perspectives on the same vulnerability, driven by their unique product, regulatory requirements, and software configurations. Using SSVC, each organization can calculate vulnerability classifications that make sense within its context while maintaining the integrity of the overall framework.
The result is a prioritization model that reflects both the current threat landscape and the organization’s specific business priorities.
Maintain an accurate CMDB to support SSVC
The effectiveness of SSVC depends entirely on the quality of the asset data it receives. If your configuration management database (CMDB) is incomplete, outdated, or misclassified, the entire decision-making process produces unreliable outcomes.
For instance, imagine a server marked as a test system that is actually hosting a production API for customer transactions. Based on that inaccurate classification, your SSVC process is more likely to misprioritize incoming vulnerabilities, which would, in turn, impact your overall organization. Or imagine if you thought you had disabled Remote Desktop Protocol (RDP) in your organization, but actually hadn’t when the Microsoft BlueKeep Vulnerability (CVE-2019-0708) was published.
Understanding your environment in detail is foundational for success with SSVC. Which means ensuring the quality of your CMDB data is essential. Follow the three steps below to ensure your CMDB can support an effective SSVC implementation.
Enrich the CMDB with critical asset attributes
Firstly, you need to make sure your CMDB is more than just a simple inventory of physical servers. Instead, include supplementary information such as ownership details, the business processes the asset supports, the type of data the system handles, and whether the system is externally accessible.
On top of this, you should also include information such as:
- Software inventory
- Virtualized servers, containers, and cloud inventories
- Identification of unlicensed or potentially unwanted programs (PUP)
All of this information is critical as it allows your SSVC process to apply its calculations to the real state of your environment.
Map dependencies
Next, expand your CMDB to include dependencies. This provides additional operational context for each asset, thereby improving the accuracy of your SSVC.
For instance, imagine a small MySQL database sitting somewhere in your infrastructure. Initially, it may seem relatively small and unimportant, especially if there are infrequent Input/Output (IO) operations on a month-to-month basis. However, if dependency mapping revealed that it underpins a payment service or customer portal, its importance would change dramatically. In turn, this would impact how the SSVC process prioritizes the vulnerability.
To see what effective dependency mapping looks like, check out the screenshot from Device42 below. You can immediately see how a seemingly simple application can quickly snowball into a more complex web of interactions when dependency mapping is applied:
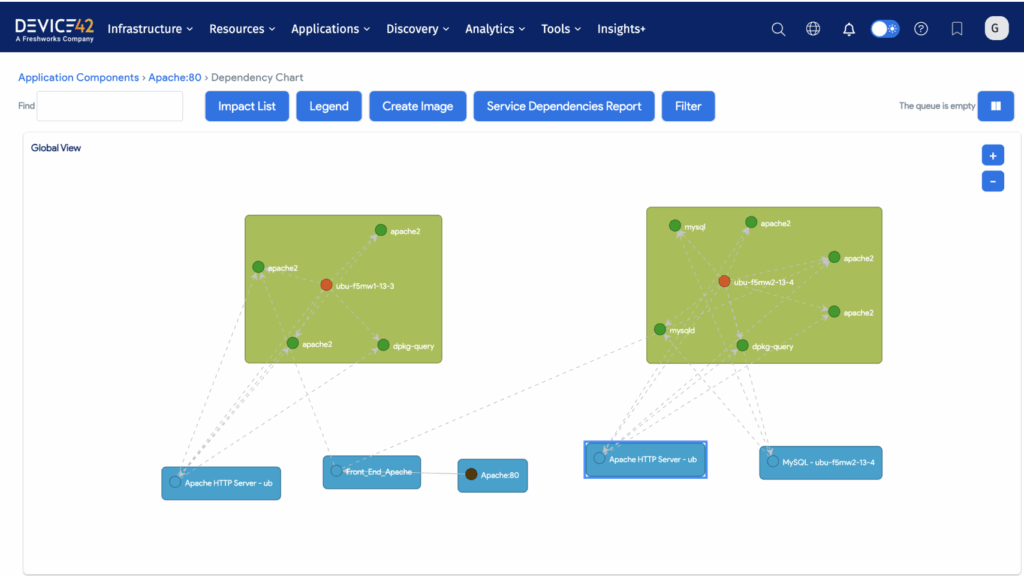
Application dependency mapping (source)
Automate discovery
Finally, ensure your CMDB discovery process is automated. Modern enterprise infrastructure is rarely static. Assets appear and disappear constantly across on-premises data centers, public clouds, and SaaS environments. Some assets are ephemeral, others are constant, and dependencies can change as new applications and services are introduced.
Continuous, automated discovery ensures that your CMDB remains up to date as changes occur. Look for a platform that provides this by providing a fully integrated solution with passive and active discovery techniques, sophisticated asset identification algorithms, and an easy-to-use CMDB that integrates with the rest of your tooling.
Classify assets by mission impact
Once you have an accurate CMDB enriched with reliable asset data, the next step is to decide which of those assets truly matter. This relates to the Mission Impact branch of SSVC, which connects technical vulnerabilities to business consequences.
When going through this process, don’t fall into the trap of blindly marking every production asset as critical. This creates over-classification noise, which dilutes the urgency of genuine high-impact issues. Instead, assess each asset individually, and then update them as new services are introduced, retired, or reprioritized.
Most organizations already have a structured way to analyze their assets; if you don’t, the table below provides a practical and straightforward approach Modify and adapt this process as needed to meet your organization’s needs:
| Step | Description |
|---|---|
| Establish a recurring review forum | Meet every two weeks to validate or update impact ratings |
| Involve the right stakeholders | Include security engineers (exposure), application owners (business context), compliance officers (regulatory impact), and operations leads (downtime tolerance) |
| Use a shared scoring model | Rate each asset or service across revenue dependency, regulatory exposure, reputational risk, and downtime tolerance. Translate these into a Critical, High, Medium, or Low impact level |
| Apply dependency mapping to uncover hidden criticality | Many supporting assets appear low-value until their dependencies are made visible. These supporting systems should inherit the higher impact rating to prevent blind spots in SSVC |
| Feed results back into systems automatically | Update the CMDB and ensure the classifications are integrated with vulnerability management workflows |
An example of the results of this process is included below. You can add or remove columns as needed to match your organization’s specific needs:
| Asset/Service | Owner | Revenue Dependency | Regulatory Exposure | Reputational Impact | Downtime Tolerance | Impact Rating | Notes/ Dependencies |
|---|---|---|---|---|---|---|---|
| Payment API | E-commerce | High | PCI DSS | High | < 1 hour | Critical | Depends on DB-01 |
| Internal HR Portal | HR IT | Low | Low | Medium | 24 hours | Medium | None |
| Dev/Test VM | DevOps | None | None | Low | Indefinite | Low | None |
Collect exploitation status from trusted feeds
One of the strongest signals in SSVC is the exploitation status of a given vulnerability. This information alters a vulnerability’s risk calculus, as all other things being equal, a vulnerability that is actively exploited in the wild demands more immediate remediation than one with only theoretical exploitability.
Within the SSVC framework, this information is broken down into three categories: no exploitation, proof-of-concept (POC), and active exploitation. Each category denotes a different level of urgency, with the active exploitation category heavily weighted towards Attend and Act classification, as you can see in the CISA SSVC calculator below:
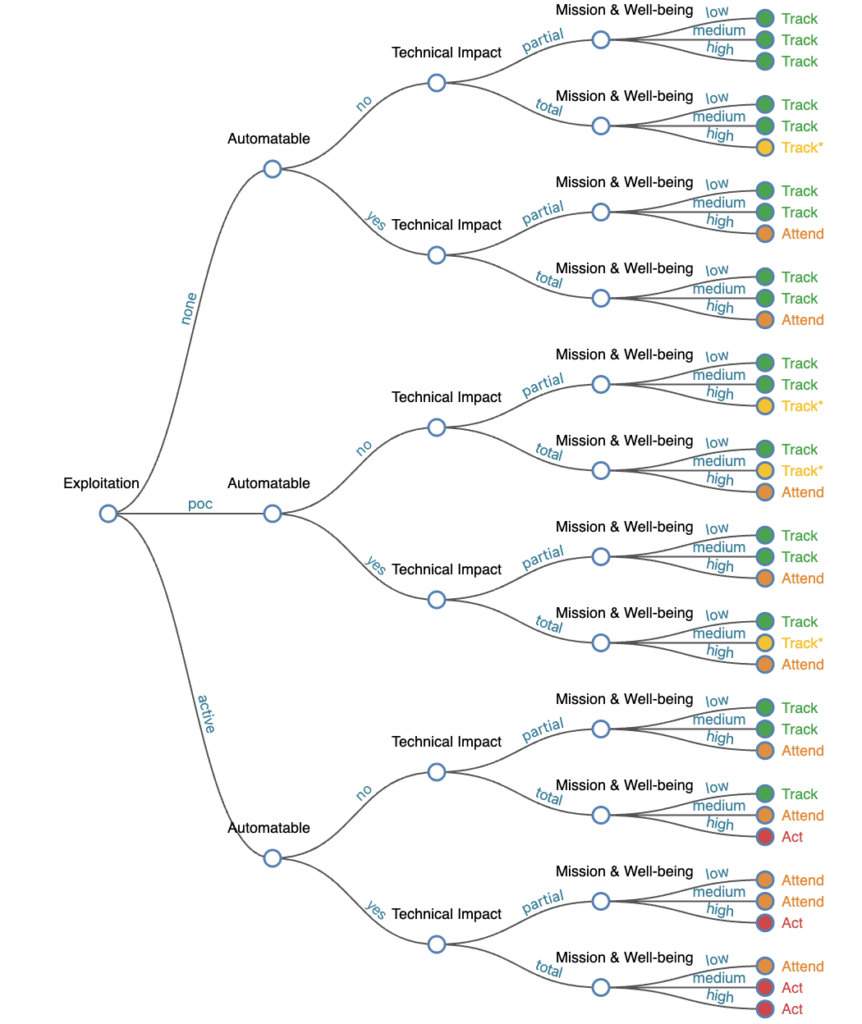
CISA SSVC Full Tree Calculator. (Source)
To get this information, you need to include live threat intelligence feeds from trusted sources, such as CISA’s Known Exploited Vulnerabilities (KEV), into your SSVC. Then, complete the loop by pairing these feeds with automation that analyzes your existing vulnerability backlog. As conditions change, update your prioritizations accordingly.
Define stakeholder-specific SSVC decision paths
The “stakeholder-specific” in SSVC is not an afterthought. Different groups care about different factors, and a single generic decision tree cannot reflect the nuance required for effective prioritization. For instance, security teams typically prioritize exploitability and exposure; IT operations, downtime minimization, and maintaining their SLAs; and business leaders, mission impact, regulatory exposure, and reputational consequences.
Rather than trying to normalize these differences into a single, one-size-fits-all tree, embrace them and ensure each group’s prioritization is captured. Then, include these in the overall SSVC decision tree.
A straightforward way to do this is to get the various stakeholders to go through a structured SSVC process together, using a previous vulnerability as a problem-solving object. Use this process to identify and understand each stakeholder’s decision points and priorities, which in turn helps you develop your overall SSVC decision tree.
Here’s what the process looks like:
| Step | Description |
|---|---|
| Outline the vulnerability | Choose a vulnerability that is well-known in the business and requires input from each stakeholder. |
| Define individual branches | Get each stakeholder to develop their own version of the SSVC decision points. |
| Create a SSVC decision tree | Put all the branches together into a unified SSVC decision tree |
| Refine as needed | Repeat this process until a prioritization equilibrium emerges. |
| Revisit quarterly | Revisit the branches quarterly to ensure they are still relevant. |
Integrate SSVC outputs into workflows
Once your SSVC generates actionable decisions, you need to push them into your remediation workflows. Your goal here is to provide as much information as possible to those remediating the vulnerability, so you can set your remediation teams up for success.
To do this, start by ensuring you push all the information you currently have about the vulnerability into your existing ticketing system. At a minimum, this should include:
- Priority
- Asset information, including asset context
- Vulnerability description, including a link to the relevant CVE
- Mission impact rating
- SLA targets
- Last updated timestamp
Next, ensure each field in your ticketing system supports dynamic updates as conditions change. For instance, if your Threat Intelligence feed suddenly identifies a change in the exploitation status of a vulnerability, then you will need to update the priority, SLA targets, and last updated timestamp accordingly. Similarly, if an asset’s mission impact changes, its classification status may change as well.
Finally, ensure that the dynamic nature of your SSVC classification is reflected in your dashboards to keep all stakeholders up to date and aligned.
Automate SSVC decision tree evaluation
As your SSVC program solidifies, you will quickly find that manually running it across large vulnerability sets is unsustainable. There are too many factors to consider, and small changes in one vulnerability can quickly cascade into far larger SSVC updates.
Instead, encode your SSVC logic into a script or rules engine that you can use within your organization. Using event-driven processing, pull data from CMDB, mission impact classifications, and live exploitability feeds, then calculate each vulnerability’s outcomes as new intelligence emerges. This allows your SSVC to scale far more effectively, improving overall vulnerability outcomes.
While encoding your SSVC logic, make sure you follow these golden rules:
-
- Simplest logic possible. Use the simplest logic possible, keeping your SSVC automation modular and easily maintainable
- Test before release. Thoroughly test automated outputs against static test cases to validate the logic before pushing it into production
- Enforce version control. Make sure that each update to your SSVC logic is tracked through a version control system such as GitHub.
For instance, the lightweight Python script below fetches KEV updates every few hours, normalizes CVE identifiers, and flags matches for immediate reprocessing by the SSVC engine. You can see that it is a straightforward module that engineers can easily integrate into a larger script:
import requests kev_feed = requests.get("https://www.cisa.gov/known-exploited-vulnerabilities-catalog.json").json() my_vulns = ["CVE-2024-12345", "CVE-2024-67890"] for vuln in my_vulns: if vuln in [entry['cveID'] for entry in kev_feed['vulnerabilities']]: print(f"{vuln} is actively exploited. Reprocess SSVC decision.") <Add extra code here to extend the script>
Regularly reassess SSVC decisions
While this has been alluded to in the sections above, it also needs to be stated explicitly. A vulnerability classified by SSVC becomes less relevant if that decision is not reassessed as conditions change.
In practice, the best way to ensure your SSVC remains relevant is to leverage your automated SSVC decision-tree evaluation and combine it with scheduled and event-driven reassessments. This ensures that you have set times where you deliberately reassess all SSVC outcomes, while remaining responsive to smaller, more event-driven changes.
For your scheduled assessments, choose a timeframe that balances operational needs with prioritization accuracy. The goal here is to ensure that no vulnerabilities fall through the cracks, rather than creating a constant churn of changing prioritizations.
For most organizations, this is somewhere between once a month and once a quarter. Any shorter, and you will create unnecessary busy work for teams as they chop and change what they’re working on, and any longer, you risk a missed vulnerability scaling into something far larger.
In contrast, your event-driven changes focus on changes that could significantly affect the overall effectiveness of your vulnerability prioritization. This should include anything that changes an asset’s characteristics, such as:
- Mission impact, such as moving from a low-impact function to a high-impact function
- Exploitation status, such as a relevant vulnerability becoming actively exploited
- Exposure level, such as a system shifting from internal-only to internet-facing
- Service dependencies, such as a supporting database becoming essential to a revenue-generating application
Conclusion
SSVC goes beyond static scores, bringing structure, precision, and transparency to vulnerability management. By incorporating accurate asset inventories, mission impact classifications, and live exploitation data, it ensures that patching priorities are based on real-world threats and the actual business importance of affected systems. In turn, security teams move beyond reacting to high CVSS scores and instead make risk-aligned decisions that directly protect the most critical parts of the organization.
The best practices outlined in this article show you how to operationalize the concept of SSVC in your organization. Starting with an accurate CMDB and then moving through to leveraging each branch of SSVC, you now know the ins and outs of making SSVC work.
In a world where vulnerabilities can be weaponized within hours, not all issues deserve equal treatment. SSVC provides the decision-making rigor to focus resources where they matter most. Knowing that you cannot patch everything, SSVC ensures you patch what matters most.