The Best CMDB for Efficiency and Insight: Key Factors to Consider
Many IT teams operate based on an old rule of thumb: “If it’s not broken, don’t fix it.” However, forward-looking organizations disapprove of such ideologies, instead investing in a configuration management database (CMDB) for service mapping and to ensure that they stay ahead of operational challenges.
Sure, smaller operations might scrape by without a CMDB, but the lack of centralized visibility creates hidden inefficiencies and risks that organically scale alongside your business. Some successful companies may seem to thrive without a CMDB, but that’s generally because of one of these three reasons:
- Hidden CMDBs: They’ve built internal systems resembling a CMDB without formally calling it one.
- Bad experiences: Past failures with expensive, overcomplicated CMDB solutions have soured their perceptions.
- Lack of awareness of the benefits: They simply don’t realize how much smoother operations could be with a CMDB’s insights.
The right CMDB provides a dynamic map of your IT landscape, but are you missing out on the full potential of this powerful tool? In this article, we discuss the practical problems of working with an inefficient CMDB, key factors to consider before choosing a CMDB, and how Device42’s comprehensive solution considerably reduces the time needed to document a complex, hybrid IT landscape.
Key factors to consider when choosing a CMDB
| Key factor | Description |
|---|---|
| Scalability and performance | Consider the ability of the CMDB to scale and handle growing volumes of data and users while maintaining acceptable performance levels. |
| Integration with existing ITSM tools | Ensure the CMDB’s compatibility with your existing ITSM processes, including incident management, change management, monitoring, and service desk capabilities. |
| Security and compliance | Identify platforms that adhere to security best practices and compliance requirements such as GDPR, HIPAA, or industry-specific regulations. |
| Customization and extensibility | Look for features that provide the flexibility to customize the CMDB schema, workflows, and user interface to align with unique business processes and requirements. |
| Total cost of ownership (TCO) | Evaluate the overall costs associated with implementing, operating, and maintaining the CMDB over its lifecycle, including licensing fees, infrastructure, support, and training. |
Core functionalities of a CMDB
The exact mechanics of how various features of your CMDB work will depend on the CMDB solution you choose. However, the core principles outlined below typically remain consistent.
Configuration item (CI) modeling and relationships
A CMDB typically offers a structured way to define CI types (servers, software, network devices, etc.) and their attributes (such as serial numbers, versions, and owners). Relationship mapping is done through link types, specifying how CIs are connected (e.g., “runs on,” “is part of,” or “depends on”). This structured model mirrors your real-world IT infrastructure and provides a common reference for other CMDB features.
Enterprises must choose a CMDB with a flexible CI model that lets them align the CMDB to their unique assets, service dependencies, and internal terminology. Without the ability to clearly define and structure your CIs, the CMDB becomes a disorganized collection of data. A flexible CI model gives you a common language and a centralized repository, ultimately forming the foundation for all other CMDB functions.
Automated discovery and data population
Manual CMDB upkeep is unsustainable and error-prone in the context of handling the scale and complexity of hybrid IT. Modern CMDBs use various discovery mechanisms—often a mix of agent-based (software installed on devices) and agentless (network scanning)—to ensure that your CMDB is constantly refreshed and remains a reliable source of truth. Advanced solutions like Device42 offer both agentless and agent-based discovery without any difference in capabilities, irrespective of the discovery mechanism.
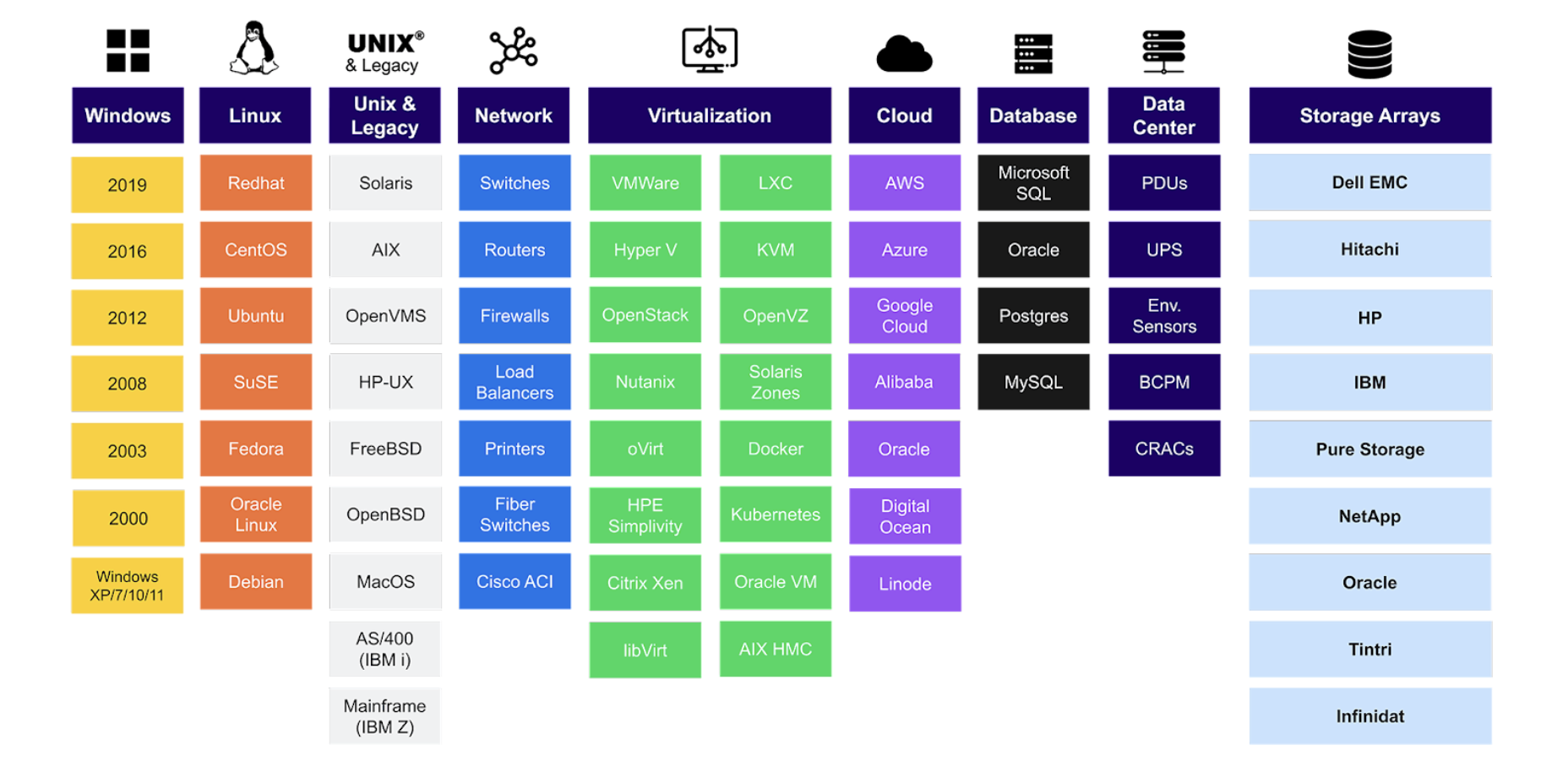
Sample of resources discovered by the Device42 automated discovery engine
Discovery starts with probing your environment and identifying devices, their configurations, and installed software. Discovered data is then automatically fed back into the CMDB, updating existing CIs and creating new ones for a near real-time picture of your infrastructure.
For instance, in a typical hybrid setup, automated discovery can scan your network and find a device with a specific IP address. The discovery further probes that device, learning if it’s a specific server type with certain software installed. This data automatically creates a new “server” CI in the CMDB or updates an existing one, populating the relevant attributes.
Version control and change management
CMDBs store historical snapshots of CI attributes for swift troubleshooting and root cause analysis. Every time a CI changes (e.g., a patch is applied or a configuration is updated), a new version is recorded. Advanced CMDBs integrated with change management systems link these versions to approved change requests. This may involve automated updates (a change task triggers a CMDB update) or a semi-automated workflow (the CMDB prompts for updated CI info as part of the change process).
Impact analysis and dependency mapping
Blindly making changes without understanding their consequences leads to service disruptions and poor CSAT scores. Building on the relationship model, a mature CMDB with dependency mapping cuts through the clutter and lets you visualize the downstream effects of changes graphically. You can drill through these connections to see how a planned change to one CI might cascade to others. This may include direct dependencies (like one server relying on another) or subtle, indirect risks (such as the failure of a component affecting multiple systems).
Reporting and data visualization
Raw data in a CMDB is only useful if you can extract insights. The ability to present that data in clear, actionable ways is what turns your CMDB into a strategic tool.
Are you spending money on unused software licenses? Are you heading for a capacity crunch due to hardware patterns? These answers guide smarter budgeting and more proactive IT planning.
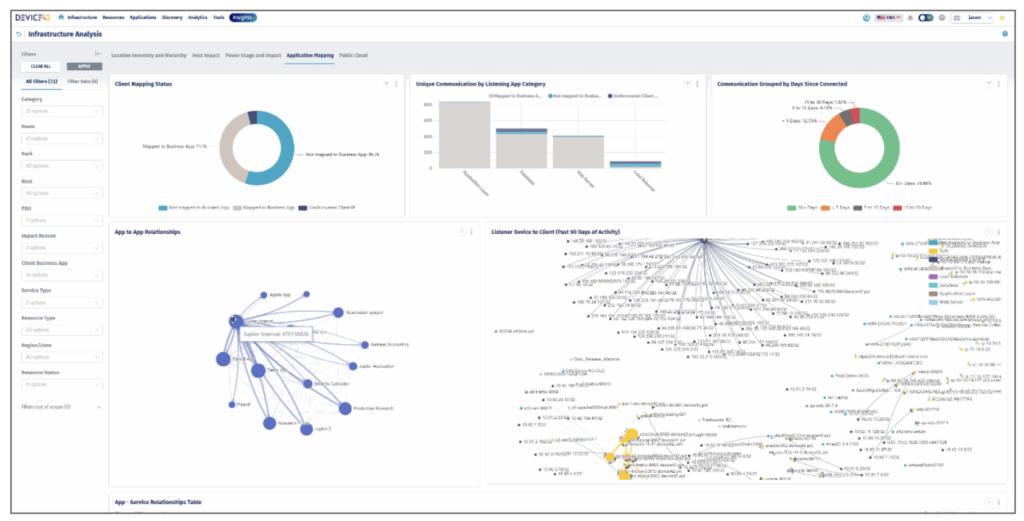
Customized asset visualization and reporting with Device42
The right CMDB platform should offer straightforward ways to cut through the complexity, whether that’s accomplished through query languages, user-friendly report builders, or integrations with powerful business intelligence tools for sophisticated analysis. Reports may be tabular (e.g., asset lists and compliance checks) or visualized via charts and dashboards (e.g., license usage trends or the distribution of hardware types).
Choosing the best CMDB: differentiation and selection criteria
While all popular CMDB platforms share common core functionalities, the nuances in how they’re implemented can have a considerable impact on whether a solution is capable of supporting your operations or becomes an expensive source of frustration. Let’s dive into those critical areas of differentiation and what to consider when making your choice.
Scalability and performance
A CMDB implementation’s initial success can paradoxically become a roadblock if it can’t scale alongside your growing IT landscape. Many projects stall because a tool that worked great for a small business unit choked as the company expanded.
Look beyond immediate needs and choose a solution built for enterprise scale that can, more importantly, support a hybrid IT estate. Also, pay close attention to performance. Complex hybrid environments demand clear dependency visualization capabilities, so assess how quickly the CMDB can render dependency maps, especially multi-tiered ones.
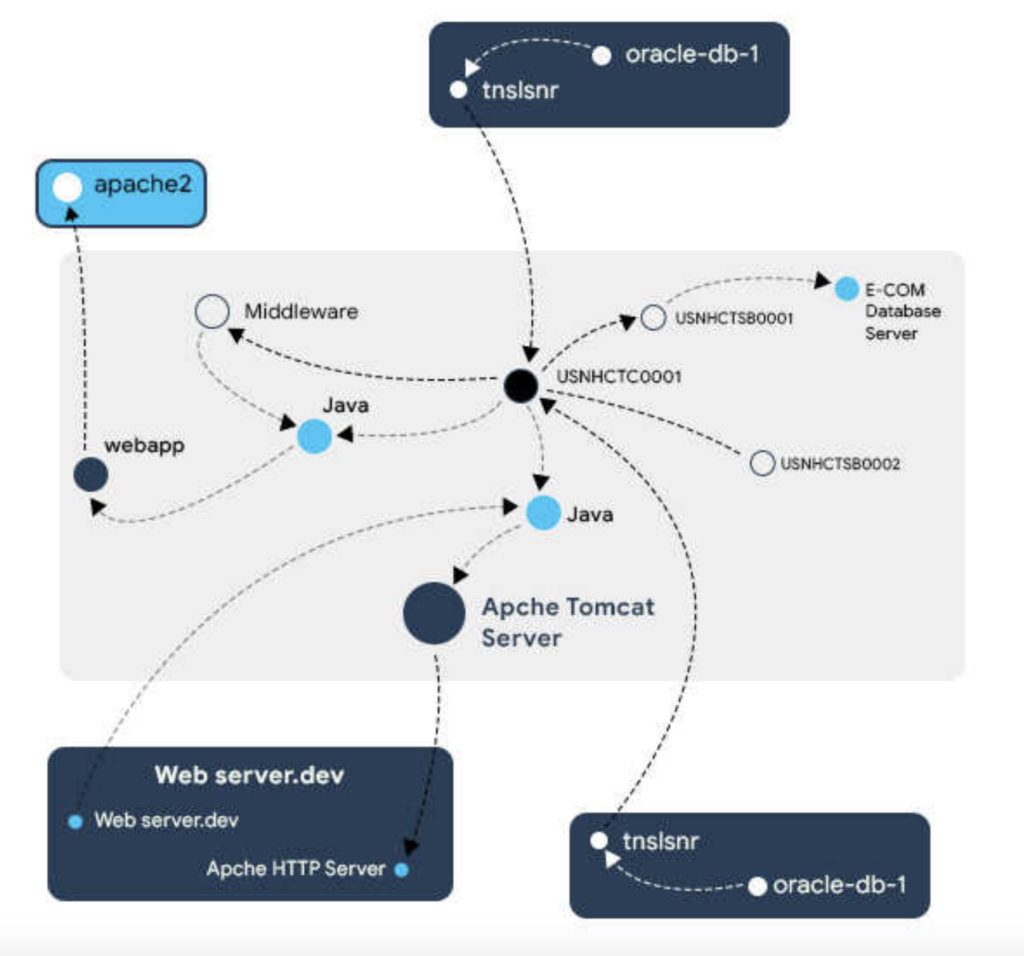
Application dependency mapping with Device42
Choosing a CMDB with robust APIs and a flexible data model is another crucial factor. This open architecture unlocks the CMDB’s potential to support IT / business service mapping, in-depth application dependency charting, and more. In addition, consider the following technical aspects:
- Identify whether the CMDB uses a traditional relational database or a more scalable graph database optimized for modeling complex relationships.
- Find out the CMDB’s indexing strategies. Efficient indexing is critical for maintaining query performance as data volume increases.
- Check if the CMDB can incorporate data feeds from your monitoring, discovery, and ITSM tools. Disparate data sources are common in large environments; ease of federation must be a key consideration.
Integration with existing ITSM tools
A true CMDB solution shouldn’t be a pile of disconnected modules. There have been instances when a routine patch led to a cascading outage for an organization, and it turns out that there was a hidden dependency no one accounted for.
Look for CMDB solutions that offer prebuilt integrations with your existing ITSM tools, like your ticketing system and monitoring platforms, or at least provide APIs for customization. This avoids reinventing the wheel and reduces implementation time. Also, consider ease of use. A complex syncing process or manual data updates can potentially become a barrier to adoption and defeat the overall purpose of solving operational bottlenecks.
Device42 was born from frustration with old, inefficient models. The platform’s powerful APIs and customizable discovery scripts let you tailor a solution to your unique environment, unlocking insights almost instantly. This level of adaptability helps enterprises address their particular challenges and gain essential insights into their infrastructure within a remarkably short timeframe.
Security and compliance
Unarguably, the worst part of IT is the constantly evolving security landscape. A CMDB helps you monitor your vulnerable assets and take corrective actions, but only if it is secure by design itself. Many compliance audits specifically examine how you manage and secure your CMDB data because your CMDB contains sensitive maps of your IT landscape, and a poorly implemented CMDB is a prime target of attack vectors.
Shadow IT, ghost assets, and outdated information can all lead to blind spots in your security posture. These gaps increase risk significantly, making it difficult to respond to emerging threats as they arise. If your CMDB isn’t sharing data with your ITSM, ITAM, and security tools, you’re possibly missing out on crucial context. This limits your ability to identify vulnerabilities, track software licenses, and optimize incident response processes.
Here are some key implementation practices for CMDB security:
- Administer granular role-based access control (RBAC) to enforce data governance and protect sensitive information.
- Enforce encryption at rest and in transit for maximum protection, along with immutable audit trails for traceability in the face of incidents.
- Prioritize solutions that support change management workflows, automated reconciliation with discovery tools, and robust federated models to handle complex infrastructure.
- Choose a CMDB capable of tracking asset ownership and configuration baselines while supporting risk assessments aligned with NIST 800-53 or similar frameworks.
- Ensure that the CMDB is built with change management at its core, which enforces ITIL workflows with integrated ticketing systems and granular compliance reporting.
Customization and extensibility
A typical CMDB implementation begins with a focus on core IT assets, tracking hardware, software, and their configuration items (CIs). However, as the CMDB becomes a trusted source of truth, it’s natural to later extend the CMDB to model dependencies among various ITSM processes, applications, and other non-IT entities. When choosing the CMDB, the ability to customize it should be considered a key differentiator to ensure that it functions as a true service asset and configuration management (SACM) tool.
As a cloud-aware, next-gen CMDB, Device42 extends to include DCIM, ITAM, SSL certificate management, and IP asset management (IPAM) capabilities as a bundled offering. Device42’s solution offers flexible CI modeling, letting you define custom attributes, relationships, and federated data sources without introducing operational complexities. This adaptability extends the value of the CMDB beyond core asset tracking and ensures that the CMDB can accurately model your entire environment and its dependencies. Interestingly, many organizations with mature CMDB customization practices have reaped these benefits and discovered that they can confidently automate portions of their change approval processes. Rather than manually reviewing every routine patch update, the CMDB solution helped them assess its impact and automatically greenlight low-risk changes.
Total cost of ownership (TCO)
Traditional CMDBs were notorious for their cost and complexity. They often required a significant upfront investment in software licenses, hardware, and implementation services. This led to long, drawn-out projects with uncertain outcomes, leaving many organizations disillusioned about the promised value.
A big part of the problem stemmed from overly specialized tools. Companies had to purchase separate products for configuration management, asset tracking, and IP management. Integrating these disparate systems was both time-consuming and expensive, often requiring custom programming or consultants.
It is common for organizations to choose CMDBs that initially seem cheap until they need professional services for every little change. Be wary of such platforms, which try to offer multiple modules based on a sticker price. Consider the full picture: implementation costs (can your team manage it?), ongoing licensing, updates, and whether the vendor locks you in.
When evaluating CMDB solutions, look for a comprehensive platform that offers a range of core functions out of the box. Implementing and maintaining a CMDB takes effort, but it should eventually pay for itself. A solution with robust discovery capabilities and intuitive interfaces will, in most cases, reduce upfront costs and accelerate time to value.
Conclusion
Every organization has its own unique processes and terminology, which are often reflected in their ITSM practices and codified within their service catalogs. However, the more interconnected and sprawling things get, the greater the need is to end the constant juggling of tools and information. Given the relentless pace of change—such as new assets, migrations, and updates—the old ways of relying on spreadsheets and diagrams were never a real solution for modern IT.
The truth is that outdated CMDBs weren’t built with the dynamics of modern IT in mind. At Device42, we focus on a “self-documenting” CMDB. Powerful auto-discovery, deep integrations, and application analysis mean that good documentation becomes part of the workflow rather than a constant uphill battle.
Our agentless solution provides the deepest, most adaptable visibility into your hybrid IT landscape. We help you uncover every dependency and relationship, giving you a real-world model of your infrastructure.
To learn more about how Device42 can empower you to optimize day-to-day operations, confidently plan changes, and resolve incidents with unmatched speed, start a free trial here.




