Optimizing IT Service Management: CMDB Use Cases Explored
Achieving operational excellence in IT service management (ITSM) is next to impossible when the IT function has no visibility into how the IT services interact with the underlying components and other systems. Investing in a CMDB that provides visibility into attributes and relationships of configuration items is a critical decision that can bear significant dividends when the CMDB is fully utilized. When it is discovered, analyzed, and shared with relevant teams, this dependency information can be an important contributor to optimal solution design, successful change control, and effective technical support activities.
Along the ITSM improvement journey, reaching the highest level of maturity requires other ITIL practices, like service design, change enablement, and incident management, to ensure access to accurate information on the underlying relationships among IT assets. This can only be achieved when the CMDB is put to proper use by having the full scope of IT services and their component relationships populated and presented to key stakeholders.
In this article, we outline CMDB use cases that contribute to enhancing an organization’s IT service delivery value streams and operational processes. The focus is mainly on technical use cases from the point of view of IT functions that directly interact with the configuration information.
Summary of CMDB use cases
This table briefly describes the seven CMDB use cases we will delve into in this article.
| Use case | Description |
|---|---|
| Centralizing all IT asset information | Acts as the single source of truth for IT asset configuration and utilization |
| Facilitating IT change impact analysis | Highlights potential change impact on dependent systems and tracks changes to CIs over time |
| Supporting IT incident root cause analysis investigation | Enables quick tracing of dependent IT assets that contribute to IT service outages and degradation |
| Aiding IT compliance audits and investigations | Provides a one-stop shop for all information regarding IT assets and dependencies to support audit activities |
| Enhancing IT information security controls | Facilitates faster identification of IT assets with vulnerabilities or weakened attack surfaces |
| Supporting sustainability and carbon footprint management | Enables managing the acquisition, usage, and disposal of IT assets in a more environmentally friendly manner |
| Facilitating migrations and modernization of data center and cloud | Enables planning migrations and modernization with the right information to result in better effectiveness and efficiency |
Use case #1: Centralizing all IT asset information
The quintessential role of the CMDB is to store the configuration records of discovered IT assets throughout their lifecycles, which includes their attributes and relationships. As IT services evolve in scope and complexity, driven by digital transformation initiatives, the CMDB plays the pivotal function of centralizing IT asset information across all environments—from on-premises to the cloud. This starts with discovery, where the CMDB locates all hardware and software components on the network, including data center infrastructure and all cloud services that the organization has permitted.
Once the attributes and dependencies are populated, the CMDB then becomes more useful for tracking the status of IT assets through their operational lives and generating information on utilization. The value of this information comes into play during planning and budgeting activities, where the IT function is better equipped to make the right decisions about which components to invest in or divest from. For example, servers with problematic operating system versions or underutilized software licenses can be easily identified through the CMDB, thereby informing decommissioning or reallocation decisions. In an era when IT is constantly called upon to show value for every dollar spent, having the right information on which IT assets are generating the best returns operationally is a significant advantage.
The CMDB, when fully configured to capture all the attributes related to operational IT infrastructure and systems, becomes the source of truth that technology teams and their partners can rely on to make the right call when it comes to the design and support of IT services. The CMDB is incredibly useful for maintaining configuration information, such as software versions, resource allocation, and dependencies. Solution designers, systems administrators, security analysts, disaster recovery planners, and others can all benefit greatly when their operational activities are based on solid facts about what is configured in their environments.
Use case #2: Facilitating IT change impact analysis
The change enablement practice, as defined in ITIL 4, is best implemented when there is a balance among effectiveness, throughput, and risk control. The CMDB facilitates this balance by ensuring that the potential impact of IT changes is well understood during the planning and approval of changes. Using the CMDB’s service dependency maps, deployment planners are aided in understanding the possible effects that a change or a series of changes can have on IT services and associated components, resources, and users, especially where migration and modernization initiatives are carried out.
One of the major challenges that delays the approval and implementation of IT changes is when those responsible for making decisions are hesitant to make the call due to limited information about the risks involved. When a team lead, IT manager, or traditional change advisory board (CAB) lacks visibility into dependencies among configuration items, their perceived risk thresholds could be mistakenly informed by past experiences and limited information. This becomes a source of erroneous decisions that may result in significant service disruption or bureaucratic headaches that delay the business value potentially achievable from the execution of the IT change. The CMDB cuts through that muddle as change authorities are equipped with real-time information on IT system dependencies, so the process for change approvals becomes less bureaucratic and more effective.
The CMDB also enables efficiency in change planning because conflicting IT changes can be flagged much more quickly when impact analysis is concurrently conducted. Change planners from different teams receive accurate information that allows them to reschedule changes to ensure that unplanned outages or degradation do not occur. Another benefit that the change enablement practice acquires through the CMDB is the tracking of changes in configuration items (CIs) over time, which is valuable input for change impact analysis. Change implementers can relate their change records to associated hardware and software, and this information can be a goldmine for making decisions on investing in upgrades or determining return on investment for IT spending.
Use case #3: Supporting IT incident root cause analysis investigation
Quickly restoring normal IT service operations to minimize the negative effects of an outage or failure is the fundamental purpose of incident management based on ITIL 4 guidance. A recent study by the Uptime Institute stated that the costs associated with IT incidents are increasing as organizations grapple with lost business revenue, negative customer sentiments, lost productivity, and potential regulatory fines and penalties. The CMDB is an important aid in both incident and problem management practices as it provides the IT asset dependency information that facilitates faster localization of problematic CIs to affected business services. IT support teams are better equipped to quickly pinpoint hardware and software components that are hanging or causing errors when they have access to the right CMDB data.
The Uptime Institute also reported that in 2023, configuration and change management issues were the leading cause of major network-related, system, and software outages. When addressing incidents caused by changes to IT assets, the CMDB can be used to quickly identify the particular configuration items that have undergone recent changes, be they related to software versions or hardware modifications.
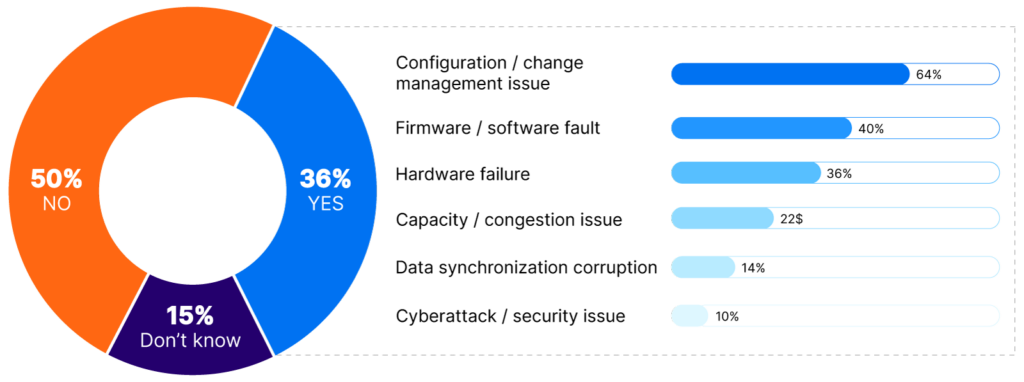
The most common causes of major IT system/software-related outages (source)
By linking affected CMDB CIs to knowledge articles containing workarounds and known errors, the CMDB becomes the reference that allows teams investigating incident root causes to be better informed as they conduct their research into repeat incidents. The reduction in the service restoration timelines through the CMDB usage results in significant cost benefits and enhanced customer satisfaction for IT users and stakeholders.
Use case #4: Aiding IT compliance audits and investigations
An IT audit’s success is heavily determined by the quality of information received and analyzed about the IT operational environment. When an IT auditor is at the fieldwork / data-gathering stage, having the right knowledge of an organization’s IT asset inventory and dependencies is critical. Without this knowledge, the IT auditor is prone to detection risks and may fail to comprehensively determine whether required IT governance controls are working effectively or whether the compliance posture adequately meets requisite regulations. The CMDB as the single source of truth can provide the right visibility into the workings of IT systems, and by doing so, make the IT audit process credible and effective.
Because a lot of time is spent sifting through data related to IT assets and their relationships, the CMDB can help in making IT audits efficient—the time taken to gather information about IT systems is shortened, and the IT auditor’s work is made easier. By being the one-stop shop for information about IT assets and their dependencies, the CMDB makes available the lifecycle information of the IT asset, including configuration changes, in a way that is easy to extract for auditors. The traceability of changes linked to CIs is also useful for IT auditors because the follow-up for corrective actions can be easily verified by reviewing the CMDB records.
Use case #5: Enhancing IT information security controls
Information security controls in IT are only as good as the configurations behind them. As an example, suppose that a company’s system administrators are notified of a vulnerability in a certain software version but have no way of ascertaining all the server instances that have that particular version installed in their data center. This may lead to a risk of cyberattacks caused by missing out on some VMs as they roll out a patch, therefore not effectively addressing the vulnerability. This scenario may be avoided by using the CMDB, which would enable the admins to speedily and comprehensively identify all IT assets with specific vulnerabilities linked to their configurations.
Another security use case is the need to identify IT assets that are at the end-of-support or end-of-life stages. These configuration items can become a source of vulnerabilities since they can be exploited by malicious actors who realize that their configurations have not been updated with relevant security patches, making them easy targets. The CMDB can be used by security administrators to easily identify which hardware and software components are at this stage, so they can be isolated for upgrading or decommissioning as required.
Security analysts know that unauthorized modifications to configuration items could point to a stealthy cyberattack within an organization’s IT infrastructure. Ports being opened, user accounts being created, or software being installed can all be signs of an intrusion. Identity access management (IAM) tools such as Microsoft Active Directory can control authorized access to systems by role and department and integrate with advanced CMDB platforms such as Device42. The resulting ability of a CMDB to track changes to configuration items and generate audit logs (see the screenshot below) can be an invaluable tool in investigating such attacks so that the security team can quickly clamp down on the intruders.
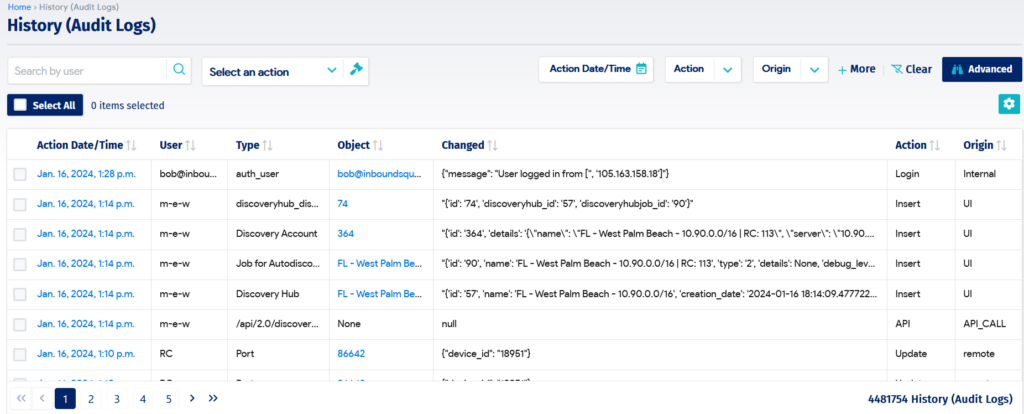
CMDB audit logs (source)
Use case #6: Supporting sustainability and carbon footprint management
Apart from supporting compliance with environmental regulations, sustainability in IT has become a significant competitive advantage, especially for organizations in consumer-based product development. Consumers are more likely to choose organizations and service providers that demonstrate that they care for the environment and are taking steps to reduce carbon emissions and tackle climate change. Also, these organizations can benefit from cost savings emanating from transitioning to IT infrastructure and solutions that are less resource-hungry.
When configured to capture IT asset information across the entire organization, the CMDB landscape becomes an invaluable tool in this endeavor since it readily provides dependency information on IT assets that can inform optimization efforts for carbon footprint management. For example, decisions on consolidating servers or reducing power usage in a data center by switching to more efficient systems can be made more effective when a CMDB is the point of reference for all IT asset information.
This capability can be extended when it comes to the identification of IT assets that are underused or that have reached their end-of-life and can be repurposed. The CMDB can be used by system admins to identify IT software and hardware that have exceeded their useful lives and can be upgraded, refurbished, or passed on to other organizations that can put them to alternate use. This can translate into a reduction of e-waste as organizations consciously review the status of their aging IT assets and seek to extend their usefulness without impacting the environment.
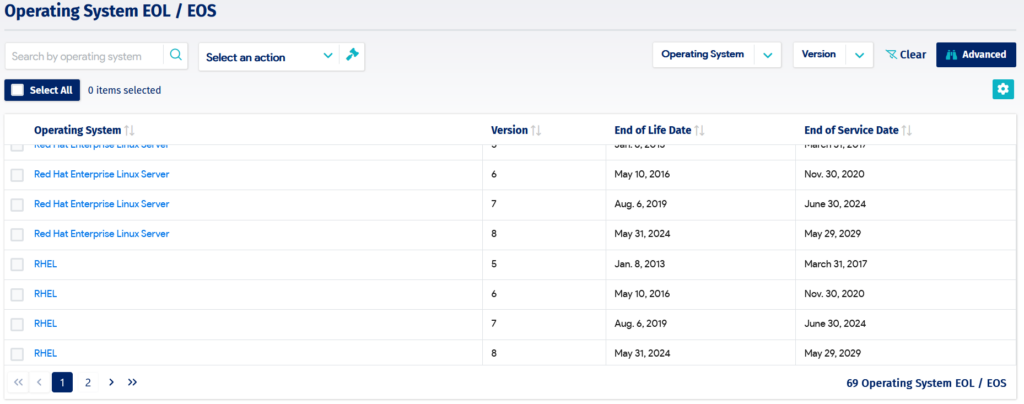
CMDB operating system end-of-life/support report (source)
Use case #7: Facilitating migrations and modernization of data center and cloud
As digital transformation strategies continue to be the mainstay of modern IT organizations, both data center and cloud migrations and modernization are key activities that continue to be executed so that the benefits of scalability, flexibility, and cost-efficiency can be applied to meeting business objectives. During such activities, however, there are potential risks, such as misconfigurations and data loss, that may throw a spanner into the works, leading to system failures, negative user experiences, and financial loss.
Cloud administrators can utilize the CMDB to de-risk migrations and modernization by capturing all IT asset dependencies, including services, ports, and user information, to ensure completeness and guarantee that the cloud environment provides a better experience for migrated IT systems. The CMDB can also be used to provide pre- and post-migration dependency maps, which can be compared to verify that the implemented changes have been conducted properly. Auditing IT service configuration after migration and modernization initiatives is better informed when the CMDB remains the source of truth across all the environments.
Recommendations
The CMDB’s usefulness in the IT service lifecycle is limited by the scope and level of detail that is captured, as well as whether key stakeholders in ITSM processes have ready access to this information. For the CMDB to support the listed use cases, organizations must ensure that the CMDB is integrated across the entire IT environment, including on-premises and multi-cloud resources. By capturing all necessary configuration information, including attributes and dependencies, chances are high that the maximum value of the investment in the CMDB can be extracted. This can only happen when IT organizations invest in the right CMDB capabilities that include fast and easy integrations with other infrastructure management and configuration management applications, as well as native support for cloud platforms..
IT system admins should also configure the CMDB’s automated capabilities regarding regular discovery to keep the configuration information fresh, ensuring that it provides quality information to support the above-mentioned use cases. When the CMDB’s information is stale, it can no longer adequately support ITIL processes, resulting in a poor IT service experience. A manual approach to updating the CMDB is ineffective in supporting ITSM practices, so it is recommended that the organization acquires an automated CMDB solution that supports scheduled discoveries and is always audit-ready.
Parting shot
The jigsaw puzzle of excellence in ITSM can only be completed when the CMDB is fully populated with all IT asset attributes and their dependencies. Maximizing the usage of the CMDB requires a robust process to support this robust solution. The service configuration management practice within the ITIL 4 framework is clear that the application of the information derived from the CMDB is what ultimately leads to value in IT service delivery.
Organizations should be aware that the listed CMDB use cases can only generate results when other factors within the IT environment are in alignment, such as leadership support, team capability, streamlined processes, and effective tools. When the CMDB captures the entire landscape of the IT environment and the information is made available to relevant stakeholders in the IT lifecycle, the promise of better service uptime, performance, and security can become a reality.




