Understanding the Significance of CMDB Configuration Items (CIs) in IT Service Delivery
Having accurate and reliable information about the configuration of IT services and making this information available when and where it is needed are at the core of the ITIL 4 Service Configuration practice. These resources play an important role in product and service management—whether physical or virtual and whether owned or leased from a third party, they need to be managed effectively.
The main steps involved in this practice include gathering this data from various sources, integrating it, and presenting it in a meaningful manner for consumption by other practices, such as IT asset management, incident management, and change enablement. Without this information, critical decisions that impact the service lifecycle cannot be made effectively, which could potentially result in system downtime or poor performance.
In this article, we delve into the makeup of configuration items within the CMDB, looking at the processes of information capture, the type of information captured, and how it is applied in service delivery activities.
Summary of key CMDB CI concepts
The fundamental concepts for configuration items (CIs) maintained within the CMDB are summarized in the following table.
| Concept | Description |
|---|---|
| CI types | Typical CI types maintained within the CMDB include hardware, software, data center facilities, and cloud systems. |
| CI attributes | CI attributes are the CI characteristics captured in the CMDB, which are based on technical aspects or operational assignments and must be managed and verified for effective utilization. |
| CI relationships | CI relationships are the CI linkages that relate CIs and other records within the CMDB. They are the core differentiator of the CMDB from ordinary asset registers and include dependencies that are necessary for impact analysis. |
| CI discovery | CI discovery is the process of onboarding CI information into the CMDB. This involves various techniques to identify assets across all IT environments and onboard the required attributes into the CMDB. |
| CI concepts in IT service management | The value of CI information within the CMDB is actualized only when ITSM processes such as incident and change management harness it for IT service delivery activities. |
CI types
The base information element in the service configuration management practice is a configuration item (CI). The ISO 20000 service management standard defines a CI as any element that needs to be controlled to deliver a service.
The CI data is stored in records inside a configuration management database (CMDB), which holds them throughout their lifecycle. This database is referenced by the IT service management practices to enable the organization to make informed decisions concerning the planning, design, development, deployment, and support of services in a manner that meets customer and business needs.
Configuration items are service assets that need to be managed to deliver services. However, only service assets that can be individually managed are considered to be CIs. For example, knowledge may be a valuable asset in service delivery activities but is not considered a CI.
CIs vary widely in composition, size, and complexity, and the way they are categorized depends on the organization’s perspective or the CMDB configuration. A general approach to categorizing CIs is based on the types outlined below.
CMDB solutions can discover and capture these different CI types and present them in their categories for configuration management. Within the CMDB, each CI type holds records of CIs with similar properties. Generally, a CMDB platform will capture hardware and software types, enabling users to define custom sub-types that facilitate more in-depth categorization. ITSM publications like ITIL 4 list other types of CIs—such as documentation, users, or locations—that may not necessarily be automatically discoverable by the CMDB.
Hardware assets
This type includes physical or tangible computing systems, such as:
- Physical Servers: These are computing devices that provide resources and services to other computers. They are the core elements that host applications and store data.
- Networking devices: These are units that provide connectivity between servers and other computing systems, including routers, switches, and access points, load balancers, storage devices, among others.
- Security appliances: These are computing devices that provide security capabilities within IT networks. Examples include firewalls, access control systems, monitoring systems, and intrusion detection/prevention systems.
- End-user devices: These are the devices used by human users to access applications and data hosted on servers, on the internet, or other devices. They mainly include computers, laptops, tablets, mobile phones, desk phones, printers, scanners, and fax machines.
Software assets
These are the intangible programs that run on the hardware. They mainly include the following:
- System software: Commonly referred to as operating systems, these are the programs that interface the physical hardware with end-user applications. The most common are Windows, Linux, Android, and iOS.
- Utilities: These programs run in the background to support the operations of systems software and applications. They perform system maintenance, file management, security functions, and other related tasks.
- Applications: These are the main programs that end-users and other systems interact with. They facilitate interaction with information, data processing, and data transfer.
- Software licenses: These programs control access to system software and applications based on the terms and conditions of the software’s owner. They ensure that the buyer or user abides by the terms that cover usage (e.g., the number of permitted installations, users, or interactions) and renewal (based on agreed payment terms).
- Virtual instances: These are virtual representations of physical hardware, such as servers or networking equipment. They abstract the capabilities of the underlying hardware and present a subset as a virtual instance that can have applications installed and interacted with.
Data center facilities
These collectively form the infrastructure required to run large-scale computing systems centrally housed at the enterprise level. They include the following:
- Server racks: These are the metal frames and cabinets that are used to mount physical hardware, such as servers and network equipment, within a server room. They facilitate effective organization, enable connectivity, ease maintenance activity, and bolster information security.
- Power equipment: These are the systems that provide power effectively and safely to physical hardware, ensuring availability and performance. They include distribution units, uninterrupted power supplies, and automatic transfer switches.
- Ventilation and cooling systems: These are the systems that provide ventilation and air conditioning to the physical hardware and power equipment to ensure an appropriate ambient temperature and humidity for effective operation. They include air conditioners, sensors, fans, and cooling distribution units.
Cloud systems
This is a category of configuration items that are accessible via the internet. They cover virtual instances of hardware assets and software assets leased from cloud providers, which own and run these systems in their own data centers. Examples include:
- Cloud applications: These are applications that are accessible via web browsers or mobile applications and are hosted by cloud providers. Typical cloud applications include email, social media sites, streaming sites, and content sites.
- Cloud resources: These are virtual assets made available to users, such as servers, databases, and network equipment.
CI attributes
Whenever the CMDB discovers the CIs within the scope of coverage (local network or subscribed cloud resources), the information that is captured within the CI record is the most important element that facilitates configuration management. Attributes are the characteristics of CIs that are captured during discovery and entered in the CI records within the CMDB. In general, there are two main categories of attributes: standard and custom.
Standard attributes
These are the commonly known attributes that have been hard-coded into the CI and are discoverable by the CMDB through common techniques. Standard attributes include the following:
- Name: The name configured on the CI
- Type: The categorization of the CI based on standard groupings
- Status: The current condition of the CI
- Model: The manufacturer’s configuration
- Operating system: The configured system software
- Computing resources: The CPU, RAM, and disk resources configured
- IP address: The configured network address that the CI was discovered with
Custom attributes
These are attributes that are either user-defined within the CMDB or configured on agents that are used in the discovery process to collect specific, non-standard information. Here are some examples of custom attributes:
- Lifecycle stage: The stage of the IT asset lifecycle where the CI is (e.g., storage, spares, production, repair, or disposal)
- Assigned: The staff member responsible for the CI from a usage or maintenance perspective
- Label: The organizational naming convention applied to differentiate the asset differently from others, e.g., a serialized notation
- Location: The storage area of the CI, be it an office location, remote location, or data center
- Vendor: The organization’s supplier contracted to maintain the CI in good working condition
Attribute presentation
When discovering CI attributes using an automated CMDB, it is important to note that these attributes can number in the hundreds. It is good practice to limit visibility to only those attributes that provide value to the configuration management practice. Other attributes can then be hidden from view, either in a tabbed manner or by completely obscuring them, to ensure that the user is not overwhelmed by the information.
An example of the presentation of attributes within the CMDB is shown below.
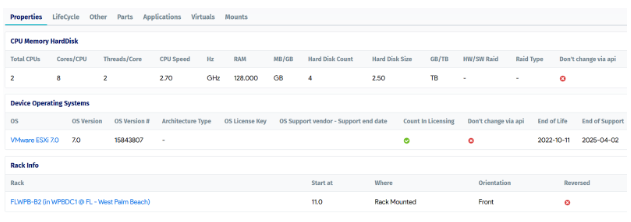
CMDB CI attributes
Attribute verification
Attributes facilitate decision-making within service management activities, especially regarding planning and maintenance. Information about computing resources can be used to plan budgets for capacity enhancement or to inform remedial measures to address performance degradation. As such, attribute information should be regularly verified to ensure that the CMDB remains the source of truth and that other inventory records are then updated accordingly.
CI relationships
Relationships between configuration items are crucial to understanding the service architectural model. Without relationships, there is no way of distinguishing an IT asset inventory record from that of the CI, so relationships are the essential element that facilitates knowledge of the CI’s contribution from a service delivery perspective.
Information about relationships is crucial in planning for new developments, upgrades, and support activities within the IT environment. Relationship information is captured during the CMDB discovery process and is displayed as part of the CI record.
Within the CMDB, relationships are normally presented as linkages between CIs, which can be tangible and simple or intangible and complex. Different facets of understanding CI relationships include:
- Physical vs. logical: A physical relationship can involve the physical interaction between CIs, such as a server blade being hosted on a data center rack. A logical relationship is an intangible association, for instance, an operating system installed in a cloud instance or a license assigned to an application.
- Upstream vs. downstream: This perspective is tied to hierarchy and impact. An upstream relationship is seen from the perspective of sharing data, where CIs are sending information to a common target CI. From a downstream point of view, the relationship is associated with shared impact, where downstream CIs are impacted when the parent CI undergoes a change or disruption.
The most common application of CI relationships within the CMDB is termed a dependency, which refers to a relationship that identifies impact whenever CIs are modified. Dependencies are associations between CIs that require them to work correctly so that service is delivered to end-users. For example, an application has dependencies on the host cloud instance it is installed on, the database it fetches information from, the security application that controls access to it, the network ports that transmit data across it, and the software license that enables it to work per the vendor’s contractual terms.
One of the ways that CI relationships are presented is through visual means. Visualization of relationships provides value in helping IT teams understand service architecture and quickly pinpoint affected CIs during change impact analysis or incident root cause analysis. This comes in handy for making IT service management processes more efficient and effective, especially where critical decisions determine the stability of operational systems.
The right CMDB solution should support all types of CI mapping approaches, including configuration-based, traffic-based, and tagging-based techniques. An example of such a visualization is shown below:
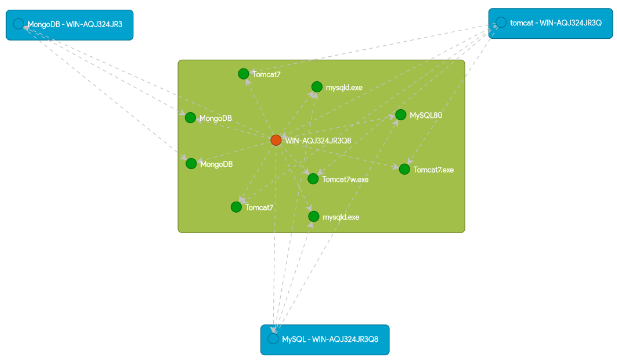
Dependency chart
CI discovery
Discovery is the process through which CIs are detected and identified, with their attributes and relationships populated as records within the CMDB. To do this, the IT function will first determine the scope of CIs whose information is to be captured and then configure the appropriate CMDB discovery mechanisms to capture the CI information based on the defined scope.
While a CMDB can be populated manually, this is neither efficient nor effective, especially in a complex IT environment with a huge number of CIs spread over multiple environments. The CMDB’s automated discovery capability is the selling point in identifying all CIs across the IT network and populating their attributes and relationships automatically.
There are two main approaches to CI discovery via the CMDB:
- Agent discovery: This involves the installation of a software agent in each target CI through the use of mass deployment tools, which can introduce administrative overhead for massive, complex environments. The agents collect in-depth information on CI availability and performance. In addition to security access permissions, some CI types will need reconfiguration to allow the agents to be installed and to transmit information.
- Agentless discovery: This involves using the native configurations of the CI and the discovery capability of the CMDB to capture CI information. No installations or deployments are required apart from security access permissions.
The CMDB’s capabilities determine the breadth of CI types and the level of detail that can be captured. To discover different CI types, the CMDB should be able to use the right protocols to pull configuration information from diverse systems, such as cloud instances, physical servers, installed applications, and networked devices. Common discovery techniques, such as ping, DNS, SNMP, WMI, SSH, and APIs, should all be supported to ensure that the entire IT environment scope is captured and brought on board to the CMDB to support IT service delivery processes. In addition, the CMDB should be able to onboard CI attributes captured by other IT systems through APIs, and then provide the capability to analyze this information and display dependency maps. In this way, organizations can leverage the CMDB capabilities to build better visibility into their CIs using data from IT monitoring and configuration management systems they have invested in.
IT environments are not static, and business requirements and external drivers all play a role in their continuing evolution. For data integrity, CI discovery should not be treated as a one-time activity for the CMDB. Through automation, the process of CI discovery should be carried out at regular intervals—at least daily—to ensure that up-to-date information exists to support IT planning, troubleshooting, and compliance activities. The right CMDB solution is always audit-ready and can be trusted to provide reliable configuration information whenever it is needed.
CI concepts in IT service management
As a discipline, IT service management involves the management of end-to-end IT service delivery to meet business goals, including the creation, delivery, and support of IT services. Having a CMDB that is populated with CI data does not automatically translate to business value until the data is disseminated to relevant stakeholders and then decisions are made based on it to support ITSM activities.
The CMDB must be depended upon as a trustworthy source of information on active IT assets and their relationships, and the relevant IT processes should be able to quickly and easily access this information when carrying out their activities. The CMDB can work as a standalone repository of CI information or be integrated with popular ITSM solutions—such as ServiceNow, Atlassian Jira Service Management, and Freshworks FreshService—to provide CI information for their modules, including service catalog, incident, change, and problem management.
An effective CMDB solution supports ITSM activities by visualizing the interconnectedness between IT assets and generating reports on CI information that stakeholders require throughout the service delivery activities. IT asset managers can make better decisions on IT assets to retire based on the end-of-life status of the associated software that is installed.
When troubleshooting incidents to identify root causes, the visualization of relationships among CIs facilitates speedy resolution. In addition, effective cost management of cloud assets is made possible when the CMDB can generate reports on which instances have been spun and what services they are supporting.
The CMDB must be trusted by all ITSM stakeholders as the single source of truth for IT asset status when making planning and optimization decisions. Stakeholder requirements for CMDB reports should be fulfilled to ensure that the relevant information they need to see is easily accessed through customized reports that meet their needs. ITSM practitioners need to be trained on the CMDB features so that they maximize the CMDB’s capabilities to visualize service models, generate impact analysis for proposed changes, and perform root cause analysis on problematic IT assets.
Recommendations
The CMDB is the central repository for CI information and, to be treated as such, a robust configuration management process must be defined that maximizes the value of the CI information for key stakeholders in the organization. This process will determine the scope that the CMDB will use for discovery across the IT environment and how the information should be regularly updated and made available to support ITSM activities. This process will also outline the appropriate metrics that will be used to track the CMDB CI information and ensure that it remains relevant to support overall organizational objectives.
When it comes to selecting the right CMDB solution, organizations should invest in one with capabilities that span the depth and breadth of CI data within the IT environment, while automating the required process activities. The CMDB must have the capability to capture all scoped CI types across on-premises and cloud environments, correlate relationships across multiple integrations, and present the complete set of attributes regarding each CI in one centralized module that other ITSM processes can access. Automating the CMDB discovery process is a no-brainer so that the CI information is refreshed quickly and efficiently.
Last thoughts
Not investing in a CMDB is a risky affair for any organization that seeks to be competitive in the digital age. Core ITSM activities, such as infrastructure planning, service restoration, and cost management, can only be carried out effectively when their associated processes are informed by updated configuration information.
Any organization that invests in an ITSM solution should consider integrating it with a CMDB that can capture all CI information across their environments to maximize its value. The true value of CMDB CI information is obtained when the ITSM practices reference the CMDB regularly, so they should be kept updated and accessible to key stakeholders. Maximizing the benefits of the CMDB directly translates into improved service delivery and ultimately generates business benefits, including improved customer satisfaction.




